Table of Links
-
Abstract and Introduction
-
Preliminaries
-
Overview
-
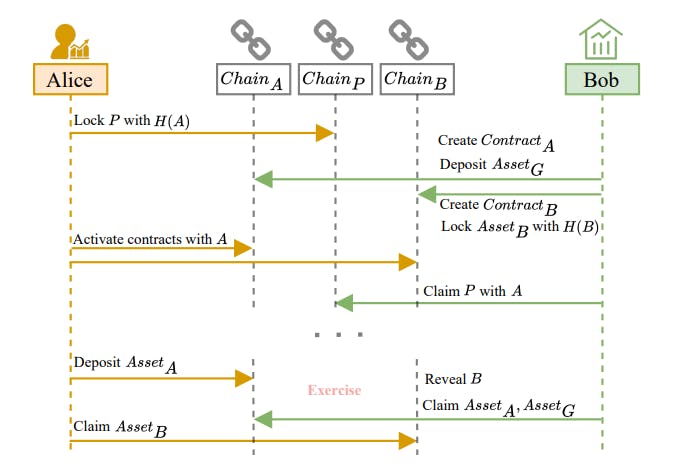
Protocol
4.1 Efficient Option Transfer Protocol
4.2 Holder Collateral-Free Cross-Chain Options
-
Security Analysis
5.1 Option Transfer Properties
5.2 Option Properties
-
Implementation
-
Related Work
-
Conclusion and Discussion, and References
A. Codes
B. Proofs
2 PRELIMINARIES
Blockchain, Smart Contract, and Asset. A blockchain is a tamperproof distributed ledger that records asset balances for each address. An asset can be a cryptocurrency, a token, or any item transactable on-chain. A party can be an individual, organization, or any entity capable of interacting with the blockchain. A smart contract (simply as “contract”) is an agreement written in code. Parties can create contracts, call functions, and check contract code and state. Δ represents the time period sufficient for parties to release, broadcast, and confirm transactions on the blockchain.
Cryptographic Primitives. A secret is known exclusively to its generator, and 𝐻(·) represents a collision-resistant hash function. In asymmetric encryption, the private key 𝑠𝑘 is used confidentially for signing, and the public key 𝑝𝑘 is shared openly.
In this paper, Double-Authentication-Preventing Signatures (DAPS) [35] is a key component in our protocol design. Initially, DAPS are designed to inhibit the reuse of a single private key for signing two different messages, where a message consists of a pair of message address and message payload in the form of (𝑎, 𝑝). DAPS ensures that a particular secret key 𝑠𝑘 cannot sign the same address 𝑎 with different payloads 𝑝. This property can be used for preventing double spending in blockchains. Two messages 𝑚1 = (𝑎1, 𝑝1) and 𝑚2 = (𝑎2, 𝑝2) are considered colliding if 𝑎1 = 𝑎2 and 𝑝1 ≠ 𝑝2. Any two signatures with the identical address but different contents will disclose the secret key. Given a security parameter 𝜆, DAPS can be delineated as follows.
• Key Generation: KeyGen(1 𝜆 ) → (𝑝𝑘, 𝑠𝑘)
• Signature: Sign(𝑠𝑘,𝑚) → 𝜎𝑚, where 𝑚 = (𝑎, 𝑝)
• Verification: Verify(𝑝𝑘,𝑚, 𝜎𝑚) → True/False
• Extraction: Extract(𝑝𝑘,𝑚1, 𝜎𝑚1 ,𝑚2, 𝜎𝑚2 ) → 𝑠𝑘/⊥
Hashed TimeLock Contracts (HTLCs). The Hashed TimeLock Contract (HTLC) is a cryptographic contract utilized to facilitate secure and trustless transactions. In an vanilla HTLC, funds are locked in a contract and can only be accessed by the designated recipient upon fulfillment of predetermined conditions within a specified time frame 𝑇 . The condition is expressed as the presentation of a preimage of the hash. For example, the contract asks the designated recipient to present the preimage 𝐴 for the hash 𝐻(𝐴). If 𝐴 is not provided before 𝑇 , the funds are refunded after 𝑇.
Authors:
(1) Zifan Peng, The Hong Kong University of Science and Technology (Guangzhou) Guangzhou, Guangdong, China ([email protected]);
(2) Yingjie Xue, The Hong Kong University of Science and Technology (Guangzhou) Guangzhou, Guangdong, China ([email protected]);
(3) Jingyu Liu, The Hong Kong University of Science and Technology (Guangzhou) Guangzhou, Guangdong, China ([email protected]).