Load balancers are network services that sit between a fleet of resources and incoming requests, where they manage traffic distribution. They distribute inbound traffic in a way that ensures single resource units are not overwhelmed, ensuring optimal performance, scalability and availability.
Azure Front Door and Azure Application Gateway are two of the load-balancing services you’ll find on the cloud computing platform Microsoft Azure, in addition to Azure Load Balancer and Azure Traffic Manager. While both can help distribute traffic to ensure balance across resources, their scopes of operation are different.
This guide delves into Azure Front Door vs Application Gateway. It explores their similarities and differences, highlighting features, pricing and use cases, while also touching on Azure Load Balancer and Azure Traffic Manager.
Reference our cloud computing terms guide if any terminology is unfamiliar.
Overview of Azure Application Load Balancer Options
As mentioned earlier, Microsoft Azure offers four main load-balancing options:
- Azure Load Balancer — Regional or Global Layer 4 Load Balancing
- Azure Application Gateway — Regional Layer 7 Application Load Balancing
- Azure Front Door — Global Layer 7 Web Traffic Management
- Azure Traffic Manager — Global Layer 7 Load Balancing
Of these four, only Azure Load Balancer works at layer four of the open systems interconnection (OSI) model.
Azure Load Balancer
Azure Load Balancer operates at the transport layer (layer four) of the OSI model. It receives incoming network traffic and checks the transport layer header for network information (such as port, IP address and protocol) to determine the traffic’s destination. Based on the load-balancing configuration, it directs the traffic to a server in the destination.
Azure Load Balancer can be regional or global. It focuses on transport-layer information and pays no attention to the actual content of the incoming packet.
Azure Application Gateway
Unlike Azure Load Balancer, Azure Application Gateway works at the application layer (layer seven) of the OSI model and is regional. It distributes traffic based on HTTP information such as the URL path, which it gets from inspecting the content.
As expected of a network load balancer, Azure Load Balancer offers faster performance, but Azure Application Gateway is more granular.
Azure Front Door
Azure Front Door routes traffic globally across multiple end points based on factors like health status, priority and latency. Like Application Gateway, it works at layer seven of the OSI model; therefore, its traffic distribution is based on application-layer information such as the host header.
Azure Traffic Manager
Load balancing in Azure Traffic Manager is global and based on the domain name system (DNS). Since its routing is based on the DNS, it works at application layer seven, but unlike Front Door and Application Gateway, it is limited because it uses only the DNS for routing. Moreover, due to DNS limitations like caching and TTLs, it is not reliable for fast failovers.
Application Gateway vs Front Door: Choosing the Right Azure Service
While they generally achieve the same goal — load balancing — Azure Application Gateway and Azure Front Door operate differently, so it comes at no surprise that some of their use cases converge while others differ.
Azure Application Gateway is ideal for regional load balancing because it cannot control traffic to resources outside of its region. Azure Front Door works better for global load balancing since it can distribute traffic to resources across multiple regions.
Both services offer session affinity and route traffic based on application-layer information such as host headers and URL paths. However, Azure Application Gateway works at the virtual machine level, so it is more granular and is the better option for complex routing.
| Feature: | Azure Front Door | Azure Application Gateway |
|---|---|---|
| Scope | Global | Regional |
| Session Affinity | Offers session affinity | Offers session affinity |
| Connection Draining | Doesn’t interact at the container or server level, so it doesn’t support connection draining | Works at the virtual machine level, making it suitable for connection draining |
| Routing | Routes traffic based on a table of rules that matches incoming domains to specific paths in the origin group | Routes traffic based on the request’s URL information |
| Web Application Firewall | Offers web application firewalls that are active at edge locations | Offers an application firewall within the server’s virtual network |
DDoS Protection |
Protects against DDoS attacks at layers three, four and seven | Protects against DDoS attacks at layer seven through web application firewall integration |
| Caching | Caches content such as JavaScript files and images for faster content delivery | Caches IP addresses to enable content to reach targets faster |
Azure Front Door vs Application Gateway Comparison
Here’s how Azure Front Door and Application Gateway differ in terms of performance, latency, security and scalability.
Azure Front Door Service: Architecture, Features, Pricing & Use Cases
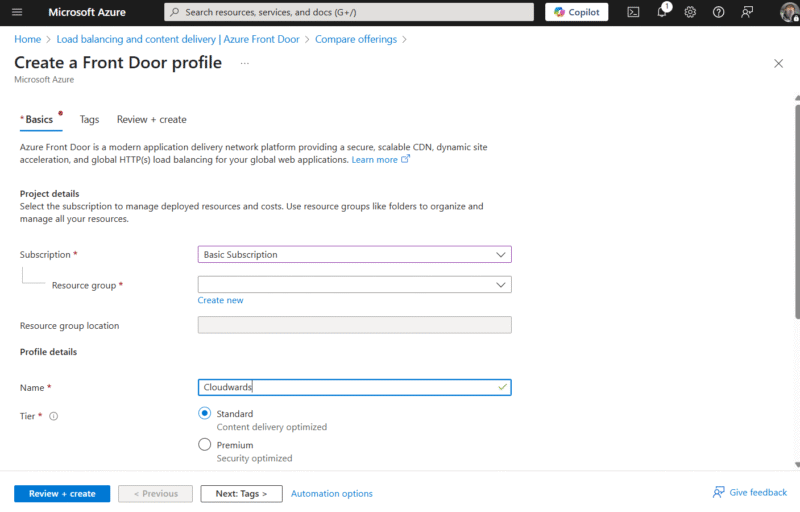
The Azure Front Door Standard tier is optimized for content delivery,
while the Premium tier comes with extra security.
Azure Front Door’s architecture is designed to prioritize proximity while ensuring reliability. We discuss this architecture in the next few sections, along with Azure Front Door’s features, pricing and use cases.
Microsoft Front Door Architecture & Global Anycast Network
Azure Front Door is built on more than 150 edge locations worldwide. Requests sent to these edge locations are directed via Anycast, which routes both HTTPS and DNS traffic. Furthermore, requests are always sent to the closest edge location or, if unavailable, the next closest edge location.
To ensure reliability, Front Door’s architecture splits the edge locations into two rings: the primary or outer rings, and the fallback or inner rings. The primary rings are the first line for handling traffic, while the inner rings serve as failover for the outer rings.
Front Door Core Features
Azure Front Door is primarily a content delivery network (CDN), but it also offers DDoS protection and load balancing.
- CDN caching for static content and dynamic site acceleration: Azure Front Door caches static site content at edge locations, promoting faster access. It also offers dynamic site acceleration by optimizing traffic routes, ensuring persistent Transmission Control Protocol (TCP) connections and eliminating TCP slow starts.
- Enhanced routing rules with RegEx and custom variables: Azure Front Door allows you to create granular routing rules using RegEx by matching patterns in the request URL, HTTP protocol and HTTP header. Furthermore, it supports matching dynamic server variables, eliminating the need to hardcode values.
- SSL/TLS certificate management and automatic renewal: Azure Front Door supports SSL/TLS encryption. It also manages and changes SSL certificates every 45 or 90 days, depending on the subscription tier.
- Built-in web application firewall and DDoS protection: Azure Web Application Firewall is integrated into Front Door, where it uses features like bot protection, managed rules, IP restriction and rate limiting to control traffic. It also provides layer-seven DDoS protection, while the default Azure DDoS Protection provides layer-three and layer-four protection.
Front Door Pricing Model
The base fees for Azure Front Door Premium and Standard are primarily charged per hour and billed monthly. However, you are also charged for requests and outbound data transfers, which are calculated per 10,000 requests and per gigabyte, respectively.
When using Azure Front Door classic, your total fees are based on the number of routing rules, the volume of inward and outbound data transfer (per gigabyte), and the number of custom domains.
Front Door Use Cases
Front Door use cases include content delivery, global traffic distribution, security and intelligent routing:
- Content delivery network (CDN): Front Door is primarily used to ensure low-latency content delivery for web apps, which it achieves by caching static content and optimizing routes and TCP for dynamic content.
- Global traffic distribution: Since Front Door is a cross-regional CDN with advanced routing, you can use it to achieve low-latency traffic distribution on globally distributed applications.
- Multi-application security: Applications behind Azure Front Door benefit from traffic filtering through Azure Web Application Firewall and network DDoS protection through the default Azure DDoS Protection. If you’re looking to secure multiple applications at the same time, Front Door is a good option.
Azure Application Gateway: Architecture, Features, Pricing & Use Cases
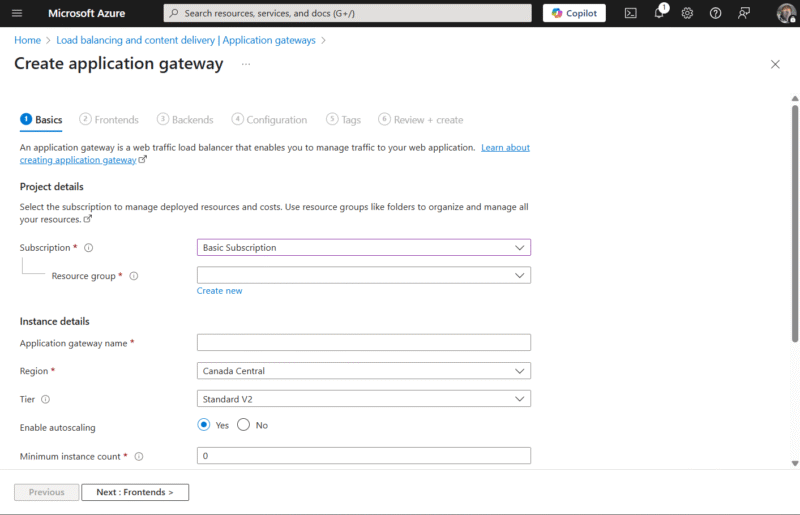
The minimum instance count specifies the minimum number of servers
available in an application gateway pool at a given time.
Like Azure Front Door, Azure Application Gateway’s architecture tends toward enhanced reliability, but it isn’t global or multi-regional. We discuss this architecture below, along with Azure Application Gateway’s features, pricing and use cases.
Application Gateway Architecture & Regional Deployment
Application Gateway exists within Azure Virtual Network, which means it is regional. It serves as the entry point for traffic destined for the resources within it, which typically are Azure virtual machines but can also be app services or on-premises servers.
Application Gateway acts as a reverse proxy; it receives requests, automatically routes traffic to available backend servers and sends responses back to the client. It supports SSL/TLS encryption, but you can integrate it with Azure WAF for further security, including protection against DDoS, SQL injection and cross-site scripting.
Application Gateway Core Features
Features like URL-based routing, session affinity and health probes are at the center of Application Gateway’s load balancing, while WAF and SSL handle security.
- URL- and path-based routing: Application Gateway allows you to route traffic based on the request’s URL path. For instance, if a request comes from “cloudwards.net/blog” and another comes from “cloudwards.net/reviews,” you can configure Application Gateway to route the former to a fleet of servers that handles your blog, while the latter goes to another fleet that serves reviews.
- Session affinity (cookie-based): Using cookie information from gateway-managed cookies, Application Gateway ensures that subsequent requests from the same user session are sent to the same backend server.
- Custom health probes and connection draining: Application Gateway probes the health of its servers and stops sending traffic to unavailable servers. Once the servers are healthy again, it routes traffic to them again. You can customize health probes, defining the port, host, interval, timeout, path, protocol and health threshold.
- SSL offloading and end-to-end TLS support: With Application Gateway, you can configure SSL sessions to end at the gateway, allowing the gateway to route traffic to its servers unencrypted. Alternatively, if you want end-to-end TLS, you can configure SSL sessions from incoming requests to end at the gateway. After that, the gateway creates a new SSL session, routing encrypted traffic to its servers.
- Optional WAF extension for Open Worldwide Application Security Project (OWASP) rule sets: Azure Web Application Firewall is an additional feature for Application Gateway. It offers protection against various exploits at the application layer, including cross-site scripting, SQL injection attacks and DDoS.
Application Gateway Pricing Model
Application Gateway V2’s pricing has a fixed component and a consumption-based capacity unit component. Both cost components are charged per hour, and partial hours are charged as full hours. In addition, inbound data transfers are free, but outbound data transfers follow regular data transfer rates and are charged per gigabyte.
Application Gateway for Containers has four cost components: frontend, association, capacity unit and application gateway for container. All four are charged per hour, with partial hours billed as full hours.
Application Gateway Use Cases
You can use Application Gateway when you need load balancing, connection draining, multi-site hosting and more.
- Load balancing: With Application Gateway, you can distribute traffic across a fleet of servers, ensuring servers are not overwhelmed and making your application highly available.
- Multi-site hosting: Application Gateway routes traffic based on information such as host headers. For this reason, you can host multiple applications within an application gateway and correctly route traffic to each one.
- Microservices: Application Gateway can also route traffic with information such as URL paths. With this feature, you can achieve granular routing to each unit in your microservices architecture.
Hybrid Approaches to Load Balancing
Given their features, Azure Front Door and Azure Application Gateway are not mutually exclusive, so you can use them together.
In a hybrid approach, Azure Front Door executes load balancing across multiple Azure regions while also providing distributed denial-of-service (DDoS) protection at the edge and optimizing content delivery. Then, Application Gateway takes over load balancing in each region, offering a more granular approach by interacting at the container and server levels.
In addition, Application Gateway offers another layer of firewall, protecting against DDoS attacks within the virtual network while also offering focused traffic management such as connection draining.
Final Thoughts
Although Azure Application Gateway is limited to regional load balancing, it is still applicable to global resources, especially when used with Azure Front Door. Moreover, using both services together offers higher availability, optimal performance, multi-layered security, optimized costs and lower latency.
Have you used an application load balancer outside of Microsoft Azure? If so, how does the service compare to Front Door and Application Gateway? Share your experience with us in the comments below. Thank you for reading.
FAQ: Azure Front Door WAF vs Application Gateway WAF
-
Azure Front Door is primarily a CDN, but it can also be used to implement application programming interface (API) gateways, serving as a global point of entry for APIs.
-
Azure WAF is used to filter and control traffic into a network, while Application Gateway is a traffic-routing system that serves as a reverse proxy.
-
Use Azure Front Door for traffic distribution and content caching in globally distributed networks.
-
Azure Front Door is not a web application firewall (WAF); it is a content delivery network with enhanced routing capabilities.