Authors:
(1) Rujia Li, Southern University of Science and Technology, China, University of Birmingham, United Kingdom and this author contributed equally to this work;
(2) Qin Wang, CSIRO Data61, Australia and this author contributed equally to this work;
(3) Qi Wang, Southern University of Science and Technology, China;
(4) David Galindo, University of Birmingham, United Kingdom;
(5) Mark Ryan, University of Birmingham, United Kingdom.
Table of Links
Abstract and I. Introduction
II. A Lightning Tour
III. Systematization Methodology
IV. Layer-One Solution
V. Layer-Two Solution
VI. Discussion
VII. Research Challenges
VIII. Concluding Remarks and References
Appendix A. Key Managements
Appendix B. Anonymity and Confidentiality
Appendix C. Background
Appendix D. A TCSC-Based Voting Protocol
Abstract—The blockchain-based smart contract lacks privacy since the contract state and instruction code are exposed to the public. Combining smart-contract execution with Trusted Execution Environments (TEEs) provides an efficient solution, called TEE-assisted smart contracts, for protecting the confidentiality of contract states. However, the combination approaches are varied, and a systematic study is absent. Newly released systems may fail to draw upon the experience learned from existing protocols, such as repeating known design mistakes or applying TEE technology in insecure ways. In this paper, we first investigate and categorize the existing systems into two types: the layer-one solution and layer-two solution. Then, we establish an analysis framework to capture their common lights, covering the desired properties (for contract services), threat models, and security considerations (for underlying systems). Based on our taxonomy, we identify their ideal functionalities, and uncover the fundamental flaws and reason for the challenges in each specification’s design. We believe that this work would provide a guide for the development of TEE-assisted smart contracts, as well as a framework to evaluate future TEE-assisted confidential contract systems.
I. INTRODUCTION
Smart contract was originally introduced by Szabo [1] and further developed by Ethereum [2] in the blockchain systems. The blockchain-based smart contracts [3], [4], [5] adopt Turing-complete scripting languages to achieve complicated functionalities [6] and execute the predefined logic through state transition replication over consensus algorithms to realize final consistency. Smart contracts enable unfamiliar and distributed participants to fairly exchange without trusted third parties, and are further used to establish a uniform approach for developing decentralized applications (DApps [7]). However, blockchain-based smart contract lacks confidentiality. The state information and the instruction code are completely transparent [8], [9], [10]. Any states with their changes are publicly accessible and all users’ transaction data and contract variables are visible to external observers. Without privacy, building advanced DApps that rely on the user’s sensitive data becomes a challenge [11], [12], [13], [14]. For instance, smart contracts in Ethereum [2] cannot be directly applied to Vickrey auction [15], [16] or e-voting systems [17], [18], where the bid and vote require to be hidden from the public. Moreover, DApps without privacy protection might be prohibited by European Union because they go against the General Data Protection Regulation [19], [20]. Thus, the complete transparency of smart contracts constrains their wide adoption. Recently, researchers have explored many cryptographic solutions to solve these issues, including utilizing techniques of zero-knowledge proof (ZKP) [21], [22], [12], [23], [24], [25], homomorphic encryption (HE) [26] and secure multiparty computation (MPC) [27]. However, these approaches are merely applicable to applications requiring simple computations.
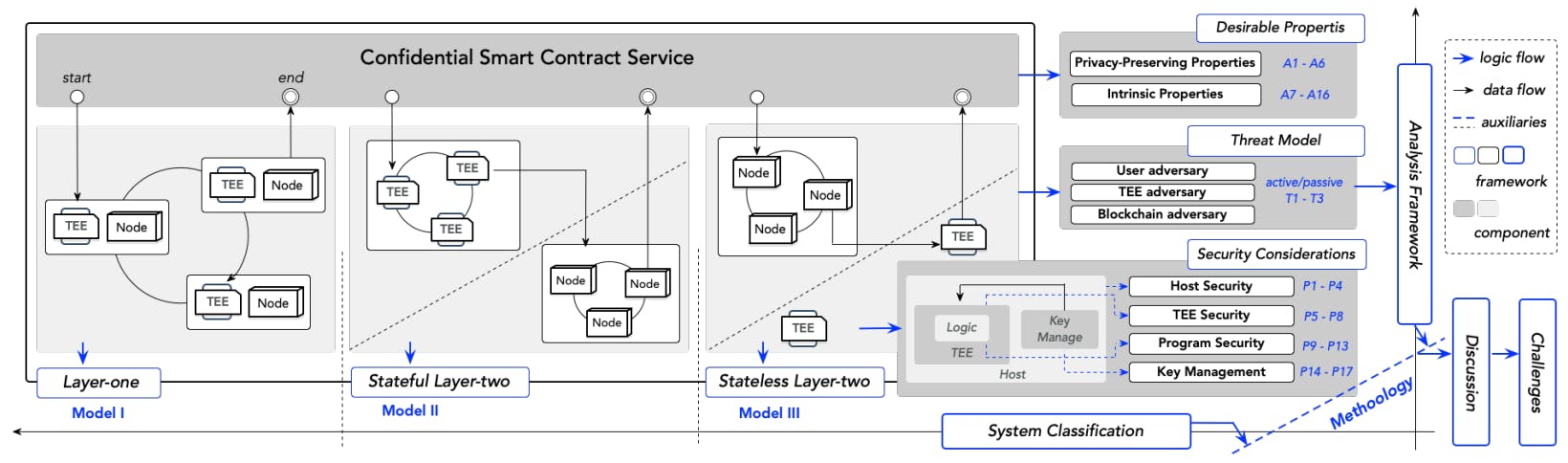
Although various TCSC protocols have been proposed, newly released projects may fail to draw upon the experience learned from existing protocols, such as repeating known design mistakes or applying cryptography in insecure ways. For example, an absence of economic incentives will pose security risks and decrease the protocol’s stability. However, the recentproposed TCSC scheme Hybridchain [41] repeats similar pitfalls by simply combining the TEE with a permissioned blockchain network, omitting considerations on the miner’s incentive mechanism. The repeating of pitfalls comes from twofold. Firstly, in-the-wild projects differ from one to another, and a relatively unique model is absent, which narrows the developers’ vision. Meanwhile, a unified evaluation framework is missing, causing many security threats to be uncovered and resulting in considerable loss from applications underpinning the execution of confidential smart contracts. This paper aims to abstract a high-level framework to simply and clearly systematize knowledge on current TCSC schemes. We attempt to capture some commonalities among these projects regarding their features, properties, and potential security vulnerability. We believe that establishing evaluation criteria to measure features and identify problems and flaws of existing TCSC protocols will offer a good guide for industry communities and promote the DApps prosperity. Main contributions (a visualized guideline in Fig.2) are:
• We provide a systematization of existing TCSC systems driven from academic work and in production projects. Based on their operating mechanisms and ways of combination, we investigate and categorize a set of typical protocols into two main classifications: the layer-one solution and the layer-two solution.
• We establish a unified evaluation framework for confidential smart contract systems. We consider two parts: the smart contracts used as services, and underlying supported blockchain systems. Accordingly, the framework covers three aspects: desirable properties for contract services, threat model and security consideration for underlying systems. Specifically, we discuss two different types of desirable properties: typical properties that inherit from traditional smart contracts and featured privacy-related properties. Then, we emphasize practical issues, pitfalls, and remedies in designing TEE-assisted blockchains from four aspects (host/TEE/program securities and key management services).
• We conduct a comparative analysis of existing protocols based on our evaluation framework. We discuss systems both from their common designs (system classification, threat model) and distinguishing features (designs, properties). The common designs show us the consistent idea when re-designing the system, while the distinguished features highlight the ingenuity of each system design that deviates from others (see Tab.III/Tab.IV).
• We further give a comprehensive discussion of current designs and implementations, including a running example, comparisons between layer-one and layer-two systems from the perspectives of security, efficiency and easy-adoption, and common issues on public verifiability. Unfortunately, a mature design is still not ready for large-scale applications. We thereby point out research challenges in this field, wishing to give insights for communities on defining their models and discovering possible solutions of designing TCSC systems.
The rest of the paper is organized as follows. Sec.II gives a high-level introduction on how to operate a confidential smart contract inside TEEs. Sec.III provides the systematization methodology (system classification and evaluation framework). Layer-one and layer-two systems are analysed in Sec.IV and Sec.V, respectively. Discussions are provided in Sec.VI. Research challenges are summarised in Sec.VII. Finally, Sec.VIII gives concluding remarks. Supplementary details are stated in Appendix A-D.