Social media is arguably your most valuable digital asset, not just for growth, but also for shaping the customer experience. And with major social media platforms being among the most public and immediate channels, even one negative post can damage your reputation fast.
So when your business social media accounts get compromised, it’s not just a tech issue. It’s a full-blown crisis that can put your entire brand at risk.
Hackers can use your account to:
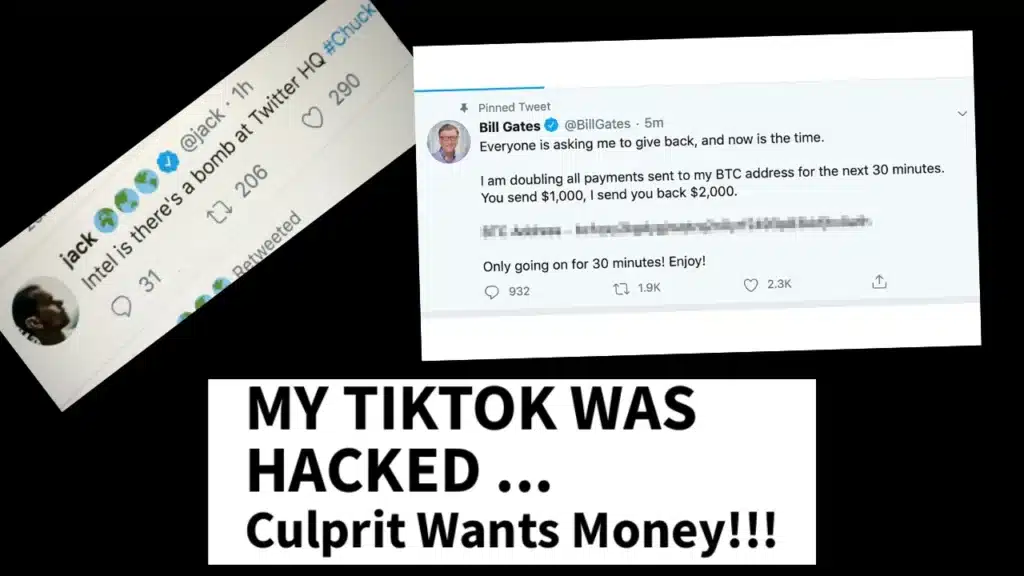
- Post false information or inflammatory content that sparks public backlash. When Jack Dorsey’s Twitter account was hacked in 2019, attackers shared offensive content, damaging both his image and the platform’s trust.
- Launch scams that target your followers. After compromising Vitalik Buterin’s account, attackers stole nearly $700,000 through a fake crypto giveaway, proving how easily social engineering attacks can trick people through social networking sites.
- Demand ransom to return control of your accounts or threaten to leak sensitive information.
- Hijack your ad account and run fake campaigns, draining your budget and exposing your financial information.
- Access private information from direct messages, shared files, or even banking details, especially if your team uses mobile devices or logs in through public Wi-Fi hotspots.
And that’s just the start. A breach can mean lost trust, lawsuits, data breaches, and sleepless nights.
Even worse, the damage doesn’t stop when you regain access. Fake posts spread quickly across social channels, and some people will continue believing them long after the cleanup. That’s why strong media security and proactive security measures are essential.
Most social media breaches come down to just a few weak spots. Whether it’s clicking a fake link, reusing passwords, or trusting the wrong app, the entry points are often simple (and avoidable).


Here are the biggest threats to your social media accounts:
- Phishing and social engineering
- Week password practices
- Insider threats
- Third-party app vulnerabilities
1. Phishing and social engineering
Most people picture hacking as complex code breaking into systems, but in reality, it’s often much simpler.
About 74% of social media account takeovers happen through phishing attacks and social engineering. That means tricking people into handing over their login credentials, often through fake links or messages.
These scams can show up as fake profiles’ giveaways, customer support messages, smishing, or fraudulent brand collaborations. They might arrive via email, SMS, DMs, or even phone calls, all designed to steal sensitive data or gain unauthorised access to your business social media accounts.
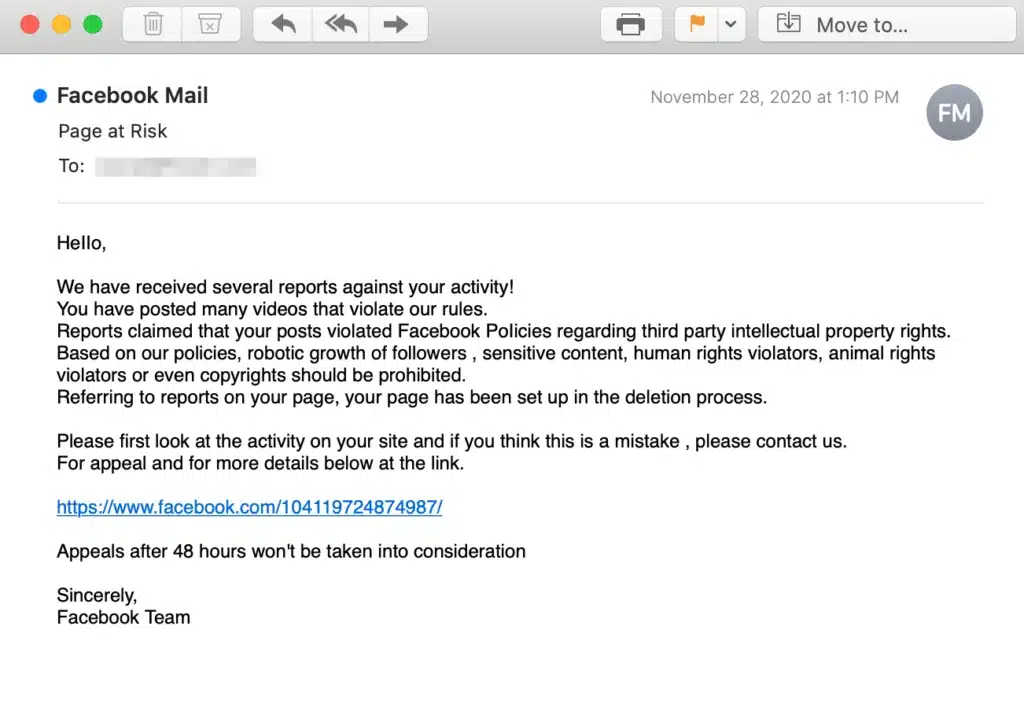

Take the example above: a fake email that looks like it’s from Facebook, claiming a post violated policy. It includes a link that looks legitimate, but clicking it could send your personal details or passwords straight to attackers.
Some phishing attempts go further, downloading malware on your devices that logs everything you type, like your banking details or social media login. Others direct you to third-party applications designed to look real but built to collect confidential information.
Tools like spam filters and email screeners can reduce these threats, but they’re not foolproof. The best defense is awareness, and making sure your team knows how to spot the warning signs.
2. Weak password practices
Weak password management is still one of the biggest security risks for brands on social media platforms. Many users reuse old passwords or pick simple ones that are easy to guess, like a pet’s name or “password123.” Only about 12% of people actually use a unique password for each of their social media accounts.
If one password gets leaked, bad actors can use it to access everything—from your direct messages and publishing privileges to banking details and sensitive information stored in third-party tools. Right now, more than 16 billion passwords are floating around the dark web. That’s why you should always check if your credentials have been exposed.
To stay ahead of these potential threats, your team should follow basic best practices like:
- Using a strong password with a mix of special characters, numbers, and capital letters
- Never reusing passwords across different accounts or devices
- Turning on multi-factor authentication wherever possible
- Avoiding password sharing across social media teams
- Updating passwords regularly, especially after a known breach
Hackers also rely on social engineering tactics, pulling personal info from public social networks to bypass weak security questions and trick users into handing over credentials.
3. Insider threats
Not everyone on your team may be as careful as they should be; and some may even pose direct security risks to your social media accounts. Former employees with lingering publishing privileges, disgruntled team members, or even accidental mistakes from trusted colleagues can all put your brand’s social media presence at risk.
Without proper security and privacy settings, insider threats can expose sensitive information, open the door for phishing attempts, or lead to loss of access altogether. That’s why it’s essential to instruct employees on media security best practices and revoke access immediately when someone leaves your organization.
4. Third-party app vulnerabilities
Your social media accounts are only as secure as the tools connected to them. Many social media platforms allow integrations with third-party applications (like scheduling tools, analytics platforms, and content creation apps) to streamline work. But if those online services aren’t secure, they introduce new security risks.
If a third-party app is compromised, bad actors may use it to trick users, hijack your accounts, or post unauthorized social media content, sometimes without your team even realizing it.
In one case, several major brands had their social media posts tampered with after a third-party analytics tool was breached. The attack exploited a single weak spot in a connected service, proving how easily hackers can gain access through indirect channels. And we’re talking about popular online services here; so always better to be safe than sorry!
The truth is, you can’t completely secure your accounts. You only need to make breaking into your accounts hard enough that cybercriminals move to the next easy target.
Here are the top recommended steps to secure your accounts:
- Use strong, unique passwords
- Enable two-factor authentication
- Limit access to trusted team members
- Regularly audit connected apps and integrations
- Review security settings on each social platform
- Avoid using public Wi-Fi without protection
- Log out of accounts on shared or public devices
- Be cautious with direct messages and links
- Disable access when employees or agencies leave
- Educate your team on security best practices
1. Use strong, unique passwords
We get it, using one easy-to-remember password across your social media accounts feels convenient. But it’s also one of the biggest security risks out there. If that password gets exposed, bad actors can quickly gain access to all your connected social networks, tools, and even banking details.
That’s why you should use a password manager. It stores all your unique passwords securely, so you only have to remember one strong password, the one that unlocks the vault. These tools also help you generate passwords with special characters, numbers, and mixed case letters, keeping your social media presence more secure.
Password managers also reduce risk on shared devices and help prevent password reuse across different social media platforms, especially if multiple team members need access.
And if your team manages accounts from mobile devices or over public Wi-Fi, this becomes even more important.
Consider pairing your setup with identity theft or credential monitoring to stay informed if your login credentials or sensitive information are ever leaked. When it comes to media security, proactive steps like these go a long way.
2. Enable two-factor authentication (2FA)
Even the strongest password management habits aren’t enough on their own. To boost your social media security, turn on two-factor authentication (2FA) wherever possible. It adds an extra layer of protection by requiring a second step (like a code or token) before anyone can log into your social media accounts.
This means that even if bad actors manage to steal your login credentials, they still won’t be able to access your accounts without that second form of verification.
Most social media platforms now support 2FA via:
- SMS text messages
- Authenticator apps
- Hardware tokens like YubiKey

But not all options are created equal. Media security experts recommend using an app or token instead of SMS (especially if your team uses mobile devices or logs in from public Wi-Fi, where phishing attempts and SIM-swapping are bigger threats).
If your brand has multiple team members with publishing privileges, enabling 2FA helps you reduce security risks and control access to your social media presence across tools, third-party applications, and social media sites.
It’s a small step, but one of the most effective best practices for keeping sensitive information safe
3. Limit access to trusted team members
Assign permissions to your social media accounts based on job function. Facebook does an excellent job of breaking down permissions into very specific tasks, which include:
- Insights: Can only see how the page, content, and ads perform
- Ads: Create, manage, and delete ads
- Content: Create, manage, or delete posts, stories, and other content
- Community activity: Review and respond to comments
- Messages and calls: Respond to direct messages and make calls as the page
X allows you to assign “contributor” access for content creation and engagement with followers, while admins handle everything else, including analytics.
With LinkedIn, users can be either analysts, content admins, or a super admin with full control over the page.
Experts recommend having two people with full admin rights to add redundancy. This helps prevent lockouts and allows for two-step approvals for sensitive actions, like managing credit lines or removing admins.









