Scammers stole $16.6 billion in 2024, and they’re getting smarter. From AI-powered voice clones to fake romance to bogus investments, criminals use sophisticated tricks to separate you from your money. Some of these are old tricks, but some are completely new—which means you need to know what to look out for.
6
AI/Deepfake-Powered Scams
My current favorite Instagram reels are the ones where infants appear to be having full conversations—obviously deepfakes, but hilarious. Unfortunately, these aren’t the only things deepfakes are being used for. According to an FBI report on AI scams, threat actors now use artificial intelligence to generate fake audio and video that’s nearly indistinguishable from the real thing. A Surfshark report found deepfake scams involving both celebrities and the public increasing at alarming rates since 2023.
These scams work through impersonation at scale. Criminals use AI to create a convincing voice of a trusted individual at an organization and then call the finance department requesting an urgent wire transfer. The technology has become so accessible that creating a convincing voice clone requires just a few seconds of audio. However, there are ways to identify AI-generated content if you know what to look for.
Financial losses from AI-driven scams exceeded $16.6 billion in 2024, marking a 33% increase from the previous year. The scammers create urgency through various channels—calls, emails, even video messages—pushing victims into making quick decisions without verification.
5
Romance Scams
Romance scammers earned their reputation as emotional predators by targeting people at their most vulnerable moments. According to a Barclays report, romance scam reports rose 20% in early 2025, with scammers specifically seeking out people who’ve recently experienced personal loss.
Romance scammers follow the same playbook every time. They find you on Tinder or Facebook, or may slide into your DMs on Instagram. After a few days of chatting, they’ll ask you for your WhatsApp number to continue the conversation.
Then comes the long con. They text you good morning every day, send you photos (that they stole from someone else’s profile), remember your birthday, and ask about your day. They’re putting in work. They’ve always got a reason they can’t meet up—they’re an oil rig worker, deployed military, or traveling businessman. They’re always somewhere far away, always with a good excuse.
Once you start trusting them, the financial requests begin. It starts small: help with a phone bill and money for internet access to keep talking. Then escalates to emergencies: medical bills, travel expenses to finally meet, and investment opportunities that will secure your future together. Victims send money believing they’re helping someone they care about, often rationalizing red flags because of emotional attachment.
Spotting dating scams is easy if you know the signs. Requests to move off-platform should raise immediate suspicion, as should any romantic interest who can’t video chat or meet in person after a reasonable time. Anyone asking for money, regardless of the reason or your feelings for them, is likely running a scam.
4
Cryptocurrency and Investment Scams
Crypto scams are now the worst of the bunch. The Better Business Bureau says they were the riskiest type of fraud in 2024, and they’re still going strong in 2025. According to Chainalysis’s Crypto Crime Report 2024 [PDF], these scams work so well because they hit you from two angles—they promise easy money while also making you panic that you’re missing the next Bitcoin if you don’t act fast.
These scams usually start with those fake investment ads you see all over Facebook and Instagram. If you try to enquire further, the ad first prompts you to provide a contact number or email, and suddenly, you’re getting calls from “investment advisors” promising you’ll triple your money in weeks.
Sometimes they play the long game—what starts as someone flirting with you on a dating app slowly turns into “Hey, I’ve been making great money with crypto, you should try it too.” Other times, they just hack your friend’s account and use it to message you about an ‘amazing investment opportunity.’ Since it looks like it’s coming from someone you know, you’re more likely to trust it. The trick involves directing potential victims to sophisticated fake websites showing fabricated profits. These platforms look professional, display convincing (but false) portfolio growth, and even allow small initial withdrawals to build confidence. Victims only discover the scam when they try to withdraw larger amounts and find their money is gone.
Before investing, verify the platform through multiple independent sources and check if it’s registered with financial authorities. Never invest based solely on social media recommendations, even from accounts that are known to you.
3
Phishing Scams
Phishing scams are nothing new, yet remain highly effective because they exploit human psychology rather than technical vulnerabilities. The 2025 Data Breach Investigations Report [PDF] identifies phishing as a persistent major threat, with attackers increasingly using AI to craft more convincing, deceptive messages.
Phishing scams are not limited to email. Smishing uses SMS messages, vishing employs voice calls, and angler phishing targets social media users. Spear phishing focuses on specific individuals using personal information gathered from data breaches or social media. Irrespective of the method used, the goal is to trick you into revealing credentials or installing malware.
These attacks succeed through manufactured urgency. A text message claiming your account will be closed, a package requiring a confirmation, or suspicious activity requires immediate action. The email looks legitimate, using official logos and formatting.
To protect yourself against phishing scams, enable multifactor authentication on all accounts. This way, even if scammers steal your password, they can’t access your account without a second authentication. Always verify sender addresses; genuine companies don’t use a free email provider like Gmail or Outlook for official communication.
2
Online Purchase Scams
A few days ago, my dad wanted my opinion on a wooden relaxation chair he’d found online, mysteriously priced at $49! The website looked professional, the reviews seemed genuine, and the countdown timer created real urgency.
To me, it was obviously a too-good-to-be-true deal, but not so apparent to my elderly parents. Fortunately, he doesn’t use online banking, cash apps, or credit or debit cards to shop online. But others might not be so lucky.
As it turns out, fake furniture sites like this one are part of a massive purchasing scam. Scammers advertise through social media, often targeting specific demographics with ads for products that look enticing. Luxury goods, private yacht rentals, electronics, and hard-to-find items are common bait.
Before purchasing from unfamiliar sites, research the seller thoroughly. Search for the company name plus “scam” or “reviews” to find others’ experiences. This is especially important for big-ticket items like purchasing a car online, where scammers often create elaborate fake listings. Check for clear return policies and contact information, including a physical address.
1
Impersonation Scams
Impersonation scams work because they exploit authority and trust simultaneously. Scammers pose as IRS agents, police officers, utility companies, or tech support, counting on people’s fear of consequences or desire to comply with authority figures.
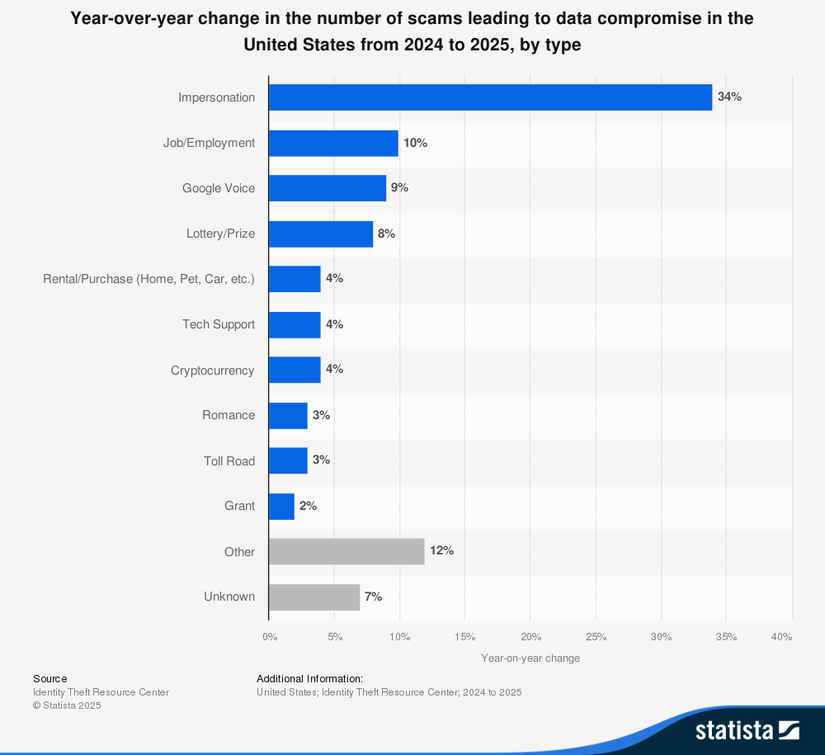
Government impersonation scams are all about fear. The caller says you’ll be arrested, deported, or sued if you don’t pay immediately. Scammers use sophisticated caller ID tricks to make the real IRS or FBI phone number show up on your caller ID via call spoofing, and it’s surprisingly easy to do. It’s no surprise that, according to Statista, impersonation scams have risen by over 30 percent from 2024 to 2025.
Tech support scams work differently. You’ll get a scary pop-up saying your computer is infected, or a fake error message that tricks you into typing commands that let the scammer in.
Scammers might have enough personal information from data breaches to seem credible, mentioning your address or partial Social Security number. Then, they use the standard pressure tactics, threatening legal consequences for non-compliance and asking to be paid via untraceable methods.
Remember that government agencies don’t demand immediate payment through gift cards or wire transfers. They communicate through official mail for important matters. Tech companies don’t call unsolicited about computer problems. If someone claims a family member is in trouble, hang up and call that family member directly to verify the situation.
AI tools are blurring the lines between obvious and sophisticated scams. Anyone with these tools can create professional-looking emails, messages, or scripts that government officials use. They can modulate voice and even videos without needing dedicated high-end computing hardware.
Always question unsolicited contact, verify requests through independent channels, and remember that legitimate organizations won’t pressure you into immediate action. The few extra minutes spent verifying could save you from joining the billions lost to yearly scams.