Calvin Wankhede / Android Authority
TL;DR
- A leaked Cellebrite chart shows Pixel phones running GrapheneOS largely resist the company’s forensic unlocking tools.
- The leak came from a private Google Teams call that someone joined and screenshotted before posting on a GrapheneOS forum.
- Pixel devices running standard Android still allow limited data access before first unlock, but GrapheneOS versions appear to block it more effectively.
Google Pixel phones already have a solid reputation for security, but leaked Cellebrite documents show they’re even harder to crack when running GrapheneOS, the privacy-focused Android alternative.
Cellebrite builds the forensic tools law enforcement uses to get data from locked phones. As reported by 404 Media, the leak came from someone who managed to join a private Microsoft Teams call between Cellebrite staff and a prospective customer. During the meeting, the uninvited participant took screenshots of what appears to be an internal ‘Android OS Access Support Matrix’ and then shared them on the GrapheneOS discussion forum.
Don’t want to miss the best from Android Authority?


The leaked slide compares Cellebrite’s success across Pixel generations and Android versions. While its software can still pull some information from standard Pixels that haven’t yet been unlocked, every locked Pixel 9 running GrapheneOS was listed as inaccessible. Older devices running GrapheneOS only showed partial results up to 2022 or 2023 security patch levels, suggesting those exploits were later closed off.
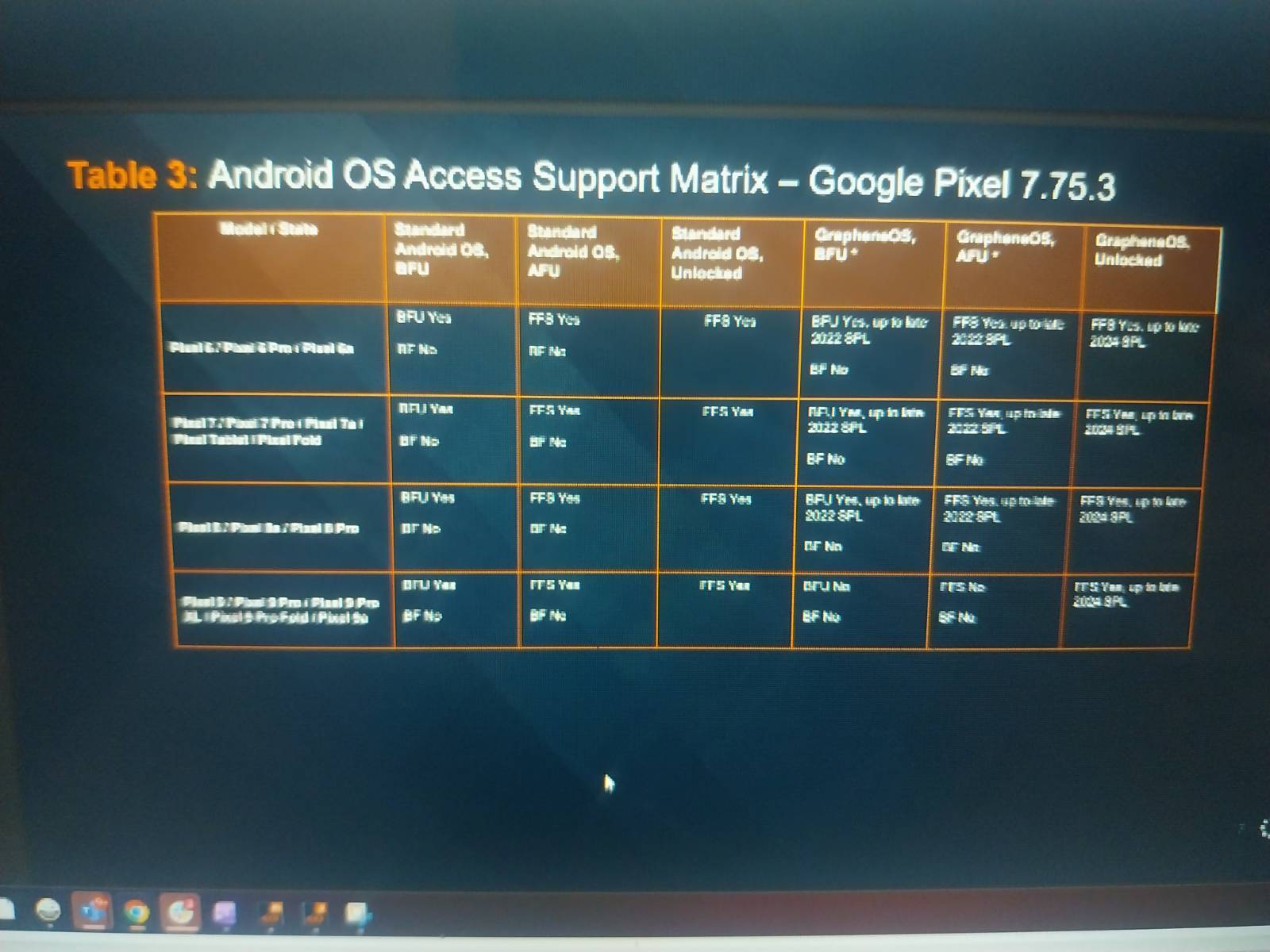
In simple terms, the chart shows that GrapheneOS effectively shuts the door on most of Cellebrite’s current extraction methods. Regular Pixels still reveal some encrypted data before they’re unlocked for the first time, but GrapheneOS devices appear to stay fully sealed.
Responses on the same forum thread purport to fill in a few extra details. The user who leaked the images said the meeting focused specifically on GrapheneOS bypass capability and took place in October. They claimed Cellebrite’s hardware costs around $1,000 with a license for ongoing use. Other members broke down what the acronyms on the chart meant and pointed out that GrapheneOS’s automatic reboot feature can make devices even harder to access.
GrapheneOS is an open-source version of Android that only runs on Pixels. It adds stricter sandboxing, optional user profiles, and security features like a duress PIN that wipes the phone if entered. It’s also the same software that’s occasionally drawn attention from police agencies who associate it with criminal use, even though its biggest audience is privacy-minded users who simply want more control over their devices.
Cellebrite declined to discuss the specifics of its capabilities, telling 404 Media that doing so could “provide potential criminals or malicious actors with an unintended advantage.” However, the leak provides a rare glimpse into the limitations of commercial forensic tools, and will be further vindication for GrapheneOS fans.
Thank you for being part of our community. Read our Comment Policy before posting.







