Microsoft recently released a security advisory and patched a critical vulnerability in ASP.NET Core that allows an attacker to bypass a security feature over a network due to an inconsistent interpretation of HTTP requests. With a CVSS score of 9.9 out of 10, CVE-2025-55315 is the highest-rated Microsoft vulnerability.
The vulnerability has been identified in ASP.NET Core versions 10.0, 9.0, 8.0, and the Kestrel package for 2.x. An attacker who is already authorized can bypass a security feature by exploiting inconsistent parsing of HTTP requests and responses. Microsoft states there are no known mitigating factors for the HTTP request/response smuggling scenario and strongly recommends patching to the listed fixed versions to prevent the security bypass.
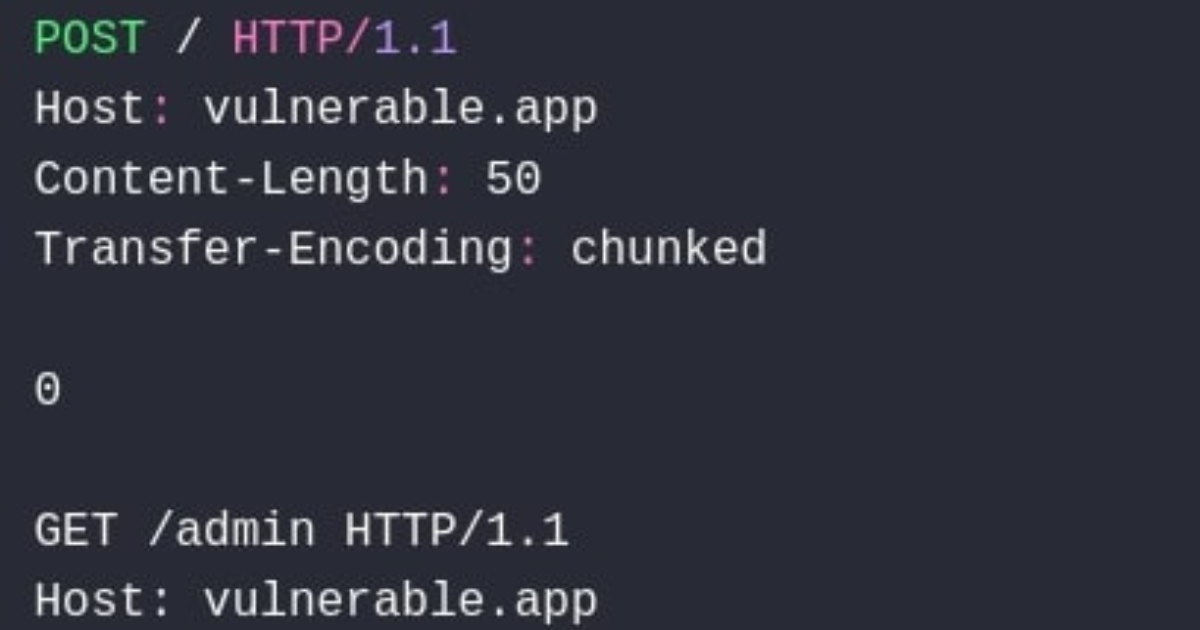
HTTP request smuggling exploits differences in how servers and proxies parse HTTP requests, using headers such as Content-Length or Transfer-Encoding to hide one request within another. In a follow-up article, the Microsoft Security Response Center explains:
The 9.9 score reflects the importance of promptly addressing this issue, which involves a security feature bypass that can influence how applications enforce authentication and authorization. (…) Depending on how your app processes requests, this could enable techniques like privilege escalation or request manipulation if left unpatched.
Barry Dorrans, security TPM for .NET at Microsoft, clarifies the high score with a comment:
The bug enables HTTP Request Smuggling, which on its own for ASP.NET Core would be nowhere near that high, but that’s not how we rate things. Instead, we score based on how the bug might affect applications built on top of ASP.NET.
Andrew Lock, staff engineer at Datadog and author of .NET Escapades, has published the article “Understanding the worst .NET vulnerability ever: request smuggling and CVE-2025-55315,” providing an example of generic request smuggling, and writes:
For ASP.NET Core applications, if you’re working with HttpRequest.Body or HttpRequest.BodyReader, or other similar methods then you may be vulnerable to attacks even if you’re not explicitly using a proxy server. Even if you don’t think of your application as a proxy or as using a proxy, if you’re doing “proxy-like” things, then you could be vulnerable.
Depending on how an application processes requests, the vulnerability could allow attacks such as elevation of privilege, server-side request forgery (SSRF), cross-site request forgery (CSRF) bypass, and injection attacks that bypass input validation. Microsoft recommends that developers check their proxy configuration and confirm that it normalizes requests and detects smuggling attempts.
Hayden Barnes, senior open source partner manager at HeroDevs, released an ASP.NET Core console application to reproduce and test HTTP chunked transfer and newline parsing behavior, allowing developers to check whether their .NET builds are affected by CVE-2025-55315.
As Microsoft does not publish CVEs for EOL software, many developers on Reddit were initially confused about how the vulnerability affects .NET 6 and earlier releases.
To address the issue, developers must install the patched runtime/SDK versions for ASP.NET Core 8, 9, or 10, or update Microsoft.AspNetCore.Server.Kestrel.Core to version 2.3.6 or above. Third-party releases address the vulnerability for unsupported .NET 6.