:::info
Authors:
Pikkin Lau, Student Member, IEEE, Lingfeng Wang, Senior Member, IEEE, Wei Wei, Zhaoxi Liu, Member, IEEE, and Chee-Wooi Ten, Senior Member, IEEE
:::
Table of Links
- ABSTRACT
- INTRODUCTION
- PROPOSED EPIDEMIC CYBER-PHYSICAL SYSTEM MODEL
- PROPOSED INSURANCE PREMIUM PRINCIPLE
- SIMULATION RESULTS
- CONCLUDING REMARKS AND REFERENCES
ABSTRACT
In this paper, a novel cyber-insurance model design is proposed based on system risk evaluation with smart technology applications. The cyber insurance policy for power systems is tailored via cyber risk modeling, reliability impact analysis, and insurance premium calculation. A stochastic Epidemic Network Model is developed to evaluate the cyber risk by propagating cyberattacks among graphical vulnerabilities. Smart technologies deployed in risk modeling include smart monitoring and job thread assignment. Smart monitoring boosts the substation availability against cyberattacks with preventive and corrective measures. The job thread assignment solution reduces the execution failures by distributing the control and monitoring tasks to multiple threads. Reliability assessment is deployed to estimate load losses convertible to monetary losses.
These monetary losses would be shared through a mutual insurance plan. To ensure a fair distribution of indemnity, a new Shapley mutual insurance principle is devised. Effectiveness of the proposed Shapley mutual insurance design is validated via case studies. The Shapley premium is compared with existent premium designs. It is shown that the Shapley premium has high indemnity levels closer to those of Tail Conditional Expectation premium. Meanwhile, the Shapley premium is nearly as affordable as the coalitional premium and keeps a relatively low insolvency probability.
INTRODUCTION
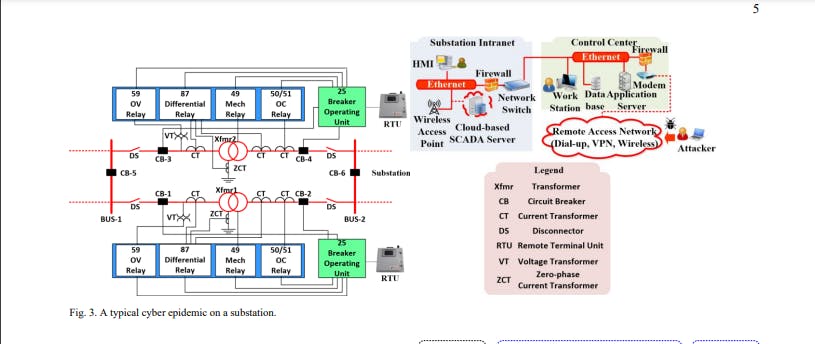
The technological transformation from the conventional power grid to smart grid has been drastically galvanized by the rapid development and deployment of ICTs. With ever increasing market values in the smart grid, the mass adoption of IEDs and other cyber-capable equipment in CPSs leads to increased network connectivity and higher operation uncertainty. Various security challenges in operations may sabotage or paralyze contemporary power grids [1]-[3]. For example, configuration change attack is a common cyber-threat where IEDs receive commands to manipulate the settings. Distance relays may receive malicious commands leading to unnecessary trips to transmission lines and disruption to substation operation.
To mitigate the emerging cyber-threats, diverse cybersecurity technologies have been developed. For example, transient detection algorithms and obfuscation strategy can be developed for mitigating device risks [4] and enhancing cybersecurity [5]. To protect the SCADA systems, IDS is a promising solution against potential cyberattacks. An advanced machine learning based IDS with high accuracy was developed [6]. A reinforcement learning algorithm was tailored to obtain the stochastic strategies that minimize load curtailment subjected to coordinated attacks [7]. IDS involving supervised learning should have collected raw data preprocessed and labeled for the classification purpose.
An ensemble approach was developed for the comparative feature extraction [8]. Security models are in place to evaluate and defend against the cyberattacks. A Cyber-Net model was developed to capture the cyber intrusion of switching attacks in a comprehensive power CPS including firewalls, SCADA and IEDs in a substation [9]. A data-driven stochastic game model was proposed to evaluate the cross-layer security of CPSs [10]. A matrix-based model was developed to capture the cyber-physical coupling behavior of IDS [11]. Strategic competition between defense and intrusion across the temporal state transition can be described by the Markov decision process [12]. Security metrics such as TTF are proposed to gauge the long-term risk of a network [13]. Investment in the enhancement of CPSs may be beneficial to reducing the interruption costs in the face of cyberattacks.
Smart monitoring based on preventive and corrective measures was proposed for cyber network of the power system [14]. Job assignment strategy was designed to boost the reliability for vehicular clouds in [15]. Conventionally, technological solutions are considered the main approach to mitigate cyber risks. In this work, cyberinsurance is further devised as a promising financial instrument to hedge against the emerging cyber risks. A cyber-insurance design framework typically includes cyber risk modeling, cyberattack-induced loss estimation, and insurance premium calculation. In [16], stochastic cybersecurity insurance pricing models for graphical networks was proposed. In [17] and [18], the potential cyber-insurance models for power systems were explored. Accounting for various cyber-intrusion scenarios, the cyber-insurance designs specific to the implications of cyberthreats on power system reliability were developed. In [17], an insurance principle was developed upon the system reliability assessment at varying intrusion tolerance capabilities of the substation SCADA servers. In [18], a Bayesian Network graphical model for integrated cybersecurity-reliability was applied to a coalitional insurance design.
In this work, a new mutual cyber insurance model will be developed for power grids deploying smart technologies. The main contributions of this paper are summarized as follows:
• A novel mutual cyber-insurance framework based on the Shapley value of the cooperative game is devised. Load loss distributions are extracted from the mutual insurance participants to formulate cost values, ultimately obtaining reduced costs in the cooperative game. • An integrated reliability evaluation model considering substations deploying smart monitoring and job thread assignment technologies is developed aiming to enhance the system robustness against cyberattacks.
• A state-sampling cyber epidemic model is integrated into the Bayesian Network cyber vulnerability model. This integrated model is devised considering the propagation of cyberattacks and network correlation. The remainder of this paper is organized as follows. Section II introduces cybersecurity in the substation CPSs coupled with the smart technologies. In Section III, the insurance principle is elaborated.
Section IV presents the case studies including numerical simulations. Section V draws conclusions for this paper. A. Related Work To clarify the advancement of this work, it would be beneficial to review the most relevant work. This work continues our quest for efficient cybersecurity insurance designs, following [17] and [18]. In [17], a cyber-insurance model based on estimating the cyber risk and reliability of interdependent TGs was proposed. Reference [18] presents an alternative cyberinsurance design based on the coalitional insurance platform [19]. In this work, a new cyber-insurance framework based on Shapley cooperative game is proposed to integrate the cyberinsurance model [17] into the coalitional cyber-insurance model [18].
A prototypical epidemic spreading model [16] was used to explore the upper and lower bounds of cyberattack infection probabilities. The proposed cyber epidemic model inspired by [16] is conceived to further estimate the long-term infectious vulnerability risk on the graphical cyber epidemic network model coupled with power systems. While the epidemic model T in [16] may be effective in estimating the upper bounds of infection probabilities in various scenarios, explicit mathematical form to evaluate the physical and monetary losses incurred in CPSs by the cyberattack needs to be further developed. The proposed epidemic network model is thus specifically tailored to the reliability-based load curtailment estimation.
This study examines the effectiveness of the proposed epidemic network model considering smart technologies including smart monitoring [14] and job thread assignment [15] for improving the reliability of TGs. The results of reliability assessment are further integrated in the proposed insurance premium design. Shapley value is utilized in the proposed insurance premium design in the proposed insurance premium design as a unique solution of the cooperative game which optimizes the price of anarchy [20]-[22]. The interdependence of CPSs was addressed in [23] by creating the probability table without explicitly assigning the SoI. In this work, the SoI are directly incorporated into the state sampling process which are then reflected in load loss profiles of TGs. The comparison with the related work described above is summarized in Table I.
:::info
This paper is available on arxiv under CC by 4.0 Deed (Attribution 4.0 International) license
:::