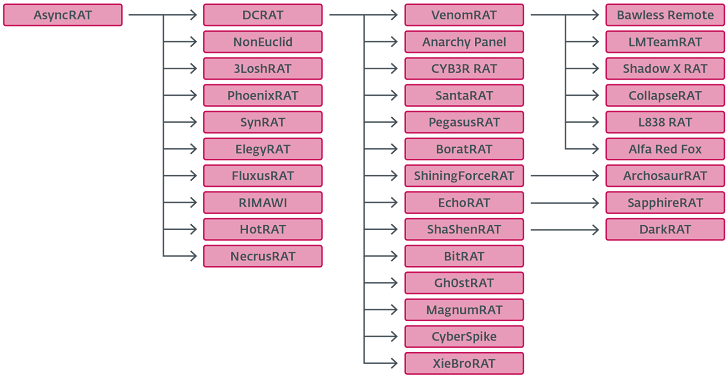
Cybersecurity researchers have charted the evolution of a widely used remote access trojan called AsyncRAT, which was first released on GitHub in January 2019 and has since served as the foundation for several other variants.
“AsyncRAT has cemented its place as a cornerstone of modern malware and as a pervasive threat that has evolved into a sprawling network of forks and variants,” ESET researcher Nikola Knežević said in a report shared with The Hacker News.
“While its capabilities are not that impressive on their own, it is the open-source nature of AsyncRAT that has truly amplified its impact. Its plug-in-based architecture and ease of modification have sparked the proliferation of many forks, pushing the boundaries even further”
While AsyncRAT’s evolution highlights its technical adaptability, its real-world impact stems from how it’s deployed in opportunistic phishing campaigns and bundled with loaders like GuLoader or SmokeLoader. These delivery methods enable rapid distribution through cracked software, malicious ads, or fake updates—targeting users in both corporate and consumer environments. Without early detection, AsyncRAT often acts as a staging tool for follow-on payloads like ransomware or credential stealers.
First published on GitHub by NYAN CAT, the C#-based malware is equipped to capture screenshots, log keystrokes, steal credentials, and allow attackers to commandeer infected systems stealthily, exfiltrate data, and execute malicious instructions.

The modular tool’s simplicity and open-source nature, coupled with its modular architecture and enhanced stealth features, has not only made it very adaptable and harder to detect, but also an attractive option for threat actors, as evidenced by the myriad campaigns distributing the threat over the years.
The Slovak cybersecurity company said the “groundwork” for AsyncRAT was laid earlier by another open-source RAT known as Quasar RAT (aka CinaRAT or Yggdrasil) that has been available on GitHub since 2015. Although both the malware strains are coded in C#, the wide-ranging differences between them suggest that AsyncRAT was much more than a fork: It was a major rewrite.
The two pieces of malware are united by the use of the same custom cryptography classes used to decrypt the malware configuration settings. Since the release of AsyncRAT, the malware has spawned diverse variants, including DCRat (aka DarkCrystal RAT) and Venom RAT.
DCRat marks a significant improvement over AsyncRAT, packing in evasion techniques to fly under the radar and augmenting its capabilities to gather webcam data, microphone recordings, and Discord tokens, alongside even a module to encrypt files.
“DCRat also implements evasion techniques like AMSI and ETW patching, which work by disabling security features that detect and log malicious behavior,” ESET said. “Addi5onally, it features an anti-process system whereby processes whose names match those in a denylist are terminated.”
Venom RAT, on the other hand, is said to have been inspired by DCRat, while also packing in enough unique features of its own.
“While they indeed belong to the Quasar RAT family, they are still different RATs,” Rapid7 researcher Anna Širokova noted in an analysis of AsyncRAT and Venom RAT in November 2024. “Venom RAT presents more advanced evasion techniques, making it a more sophisticated threat.”
ESET said it also identified lesser-known variants of AsyncRAT, such as NonEuclid RAT, which incorporates plugins to brute-force SSH and FTP credentials, collect geolocation, act as a clipper by substituting clipboard data with the attacker’s cryptocurrency wallet addresses, and even spread the malware by compromising portable executable files with an arbitrary payload.

JasonRAT, for its part, introduces bespoke changes of its own, such as the ability to target systems based on country. Likewise, XieBroRAT features a browser credential stealer and a plugin to interact with Cobalt Strike servers via a reverse connection. It’s also adapted for the Chinese market.
“AsyncRAT’s rise and its subsequent forks highlight the inherent risks of open-source malware frameworks,” ESET said. “All of these forks not only extend AsyncRAT’s technical capabilities but also demonstrate how quickly and creatively threat actors can adapt and repurpose open-source code.”
“The widespread availability of such frameworks significantly lowers the barrier to entry for aspiring cybercriminals, enabling even novices to deploy sophisticated malware with minimal effort. This democratization of malware development – especially considering the rising popularity of LLMs and potential to misuse their capabilities – further accelerates the creation and customization of malicious tools, contributing to a rapidly expanding and increasingly complex threat landscape.”
This shift has also fueled the rise of malware-as-a-service (MaaS), where preconfigured AsyncRAT builders and plug-and-play modules are sold openly on Telegram and dark web forums. The growing overlap between open-source malware, penetration testing tools, and commercial remote access frameworks complicates attribution and defense.
For security teams, this means greater focus on behavioral detection, command-and-control (C2) analysis, and understanding how fileless persistence, clipboard hijacking, and credential theft converge in modern malware campaigns.









