Douyin international registration claim debunked, over 10,000 fake foreign user accounts removed · TechNode
A recent report claiming that Douyin, the Chinese version of TikTok, has opened international registration has been debunked as a…
AI is learning to speak African languages, thanks to these startups |
It’s a rainy Saturday morning in Lagos, and the noise inside the public hospital walls on the city’s coastal edge…
A Day in the Life of Tomorrow: Cars That Work While You Play, Robots That Cook Your Dinner | HackerNoon
The house awoke first, as it always did, with a sigh of hydraulics and soft whirs behind the drywall. A…
Xiaohongshu shareholders seek to sell portion of their stakes to companies including Tencent · TechNode
According to a report by IThome on Tuesday, major shareholders at Xiaohongshu (also known as RedNote) are in talks to…
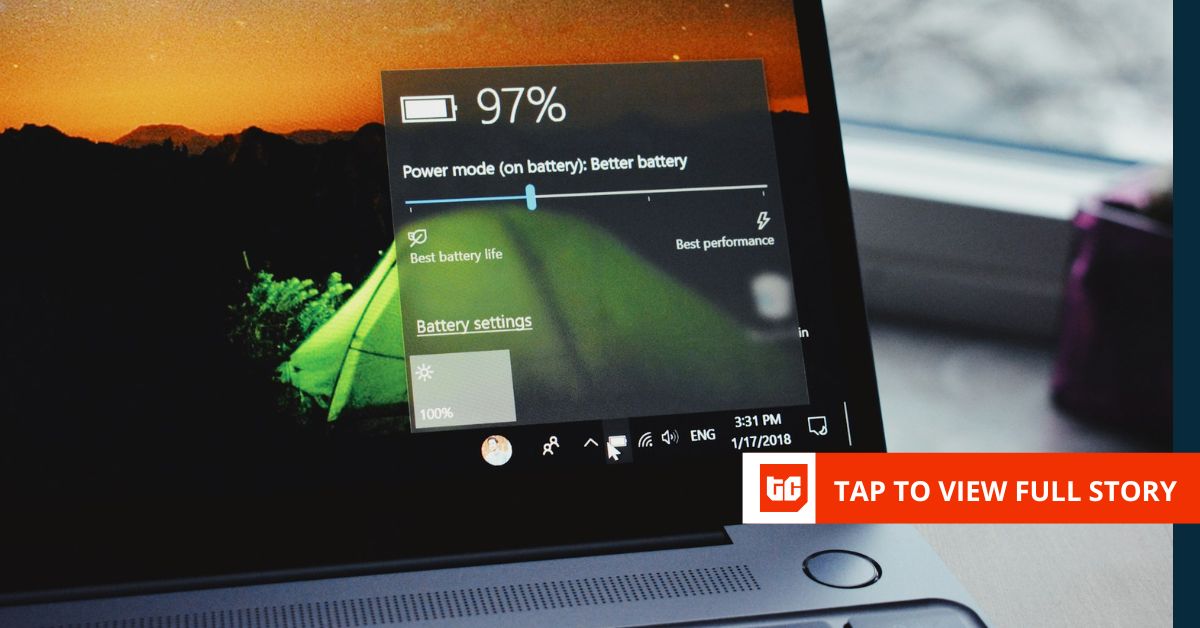
How to save your Windows 10 laptop battery
I used to treat my Windows 10 laptop like it was invincible. I would charge it when it was low,…
AI Is Eating the Browser—And That’s a Good Thing | HackerNoon
The web is no longer just a place for browsing. It’s where modern business happens: sales, support, onboarding, research, and…
China’s BYD expands to South Korea with three EV models · TechNode
BYD is taking orders for its Atto 3 electric crossovers in South Korea at a starting price of 31.5 million…
MTN’s Zakhele Futhi leaves investors disappointed with low returns
MTN’s Zakhele Futhi (MTNZF), a Black Economic Empowerment (BEE) investment scheme, will begin paying out shareholders from July 28, 2025,…
How the Right Setup Supports Social Media Marketing Strategies
Social media marketing is like building a house. You can have the fanciest furniture (your content), but without a strong…
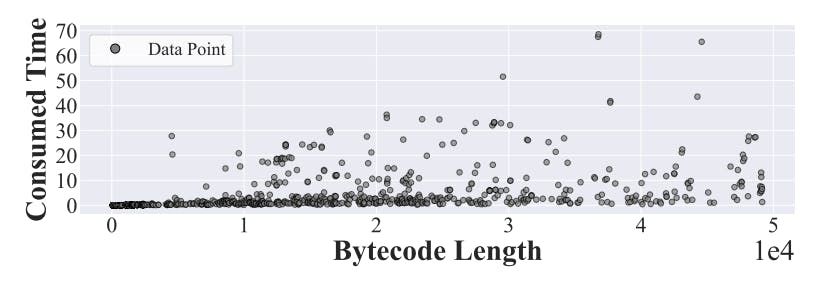
How to Find Smart Contract Vulnerabilities Before Exploit Happen | HackerNoon
Table of Links Abstract and 1. Introduction Background 2.1 Ethereum Primer 2.2 Whitelisted Address Verification 2.3 Taint Analysis on Smart…