Linux 6.19 Goes Ahead And Enables Microsoft C Extensions Support
Last month I reported on Linux 6.19 looking to enable Microsoft C Extensions support throughout the Linux kernel with setting…
How to Turn Year-End Reflections into Q1 Content Gold | HackerNoon
December is here, and if your team is anything like most tech companies, you're knee-deep in retrospectives, post-mortems, and year-end…
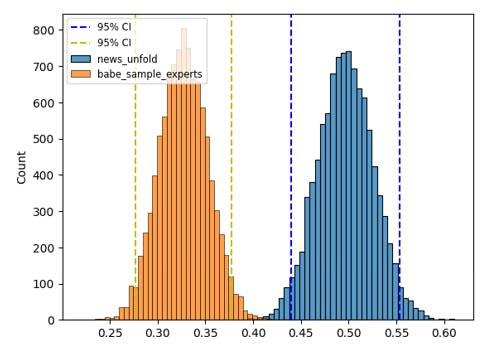
NewsUnfold Scores High on Ease of Use as Testers Call for Smoother Feedback Flow | HackerNoon
Table of Links Abstract and Introduction Related Work Feedback Mechanisms The NewsUnfold Platform Results Discussion Conclusion Acknowledgments and References A.…
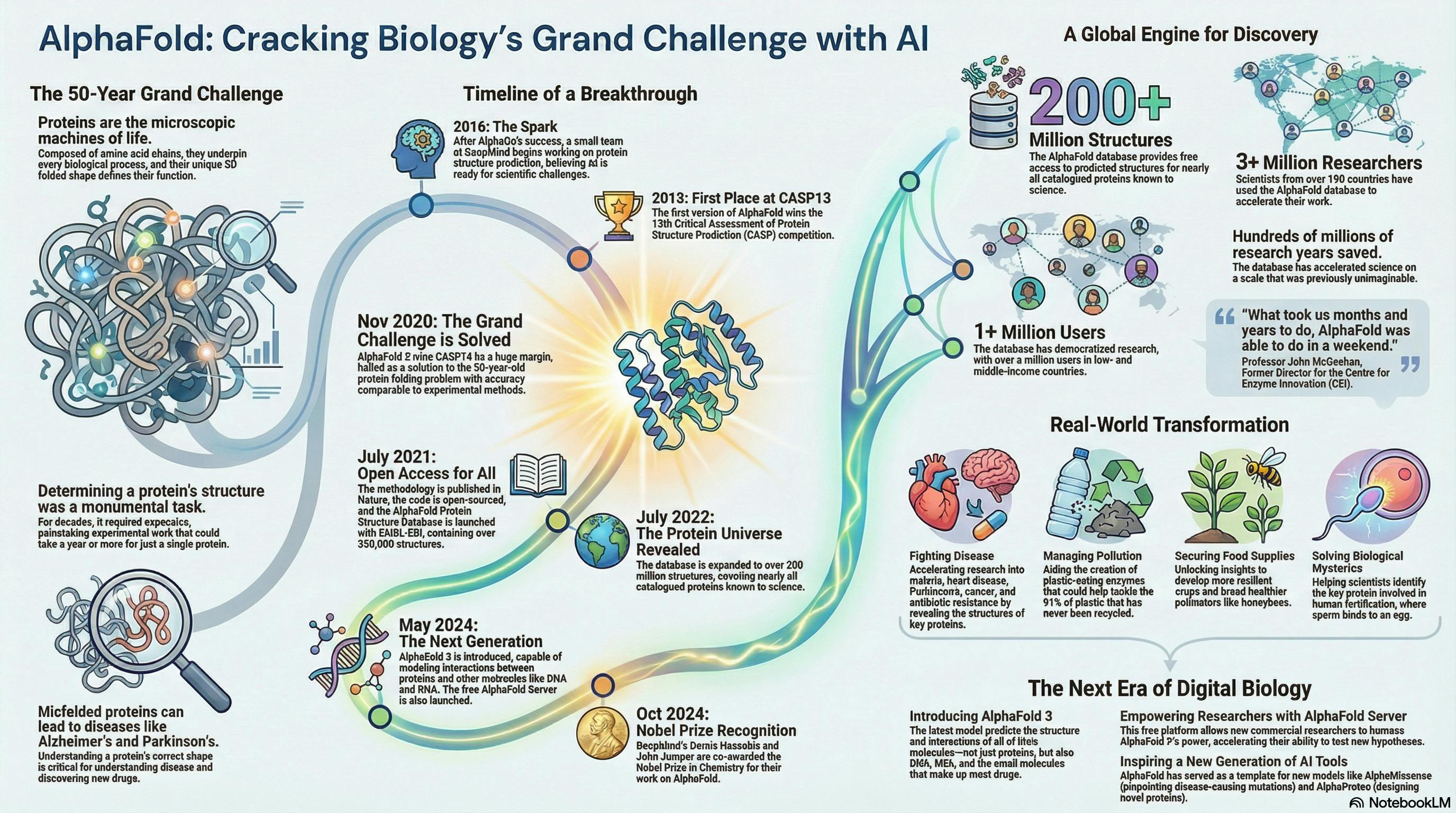
More Than a Nobel Prize: 6 Surprising Ways an AI Breakthrough Is Reshaping Science | HackerNoon
Inside every living cell is a universe of microscopic machinery. These machines, called proteins, are the engines of life, driving…
User Feedback Boosts Media-Bias Dataset Accuracy in NewsUnfold Evaluation | HackerNoon
Table of Links Abstract and Introduction Related Work Feedback Mechanisms The NewsUnfold Platform Results Discussion Conclusion Acknowledgments and References A.…
CoinAvatar Rolls Out Platform Optimizations Targeting Mainstream Web2 Adoption | HackerNoon
December 2025 - CoinAvatar, the crypto visualization platform, has rolled out major platform optimizations across its multi-chain infrastructure. The updates…
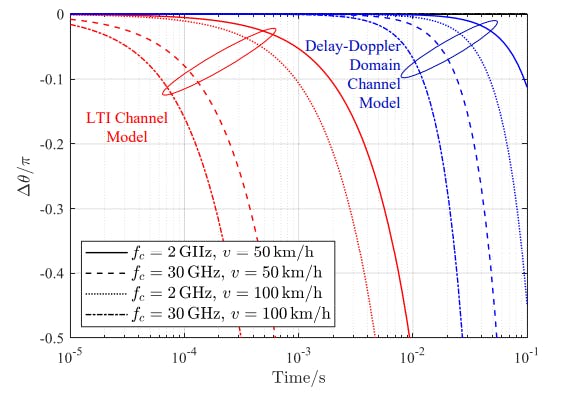
Researchers Explain How Delay–Doppler Spread Affects Interference in Discrete Channel Models | HackerNoon
Table of Links I. Abstract and Introduction II. Related Work III. Modeling of Mobile Channels IV. Channel Discretization V. Channel…
Sched_EXT With Linux 6.19 Improves Recovering For Misbehaving eBPF Schedulers
The Linux kernel's innovative sched_ext code for being able to easily write extensible task schedulers using eBPF programs has some…
Apex Fusion Connects Three Blockchain Architectures: What This Means for DeFi’s $100B Future | HackerNoon
What does it take to build infrastructure that works across fundamentally incompatible blockchain systems? The decentralized finance sector crossed $100…
While SNAP Is Safe, LA Residents Still Struggle With Food Insecurity – Knock LA
Volunteers give out food to community members at Urban Partners during their weekly Saturday distribution. (Photo: Urban Partners) On Friday October…