Linux 6.18 Will Be A Big Improvement For Servers Encountering DDoS Attacks
A set of patches merged via the networking pull request for the Linux 6.18 will help servers better cope with…
TSMC begins production of Intel’s Lunar Lake processor, Core Ultra 200V series · TechNode
Intel’s Lunar Lake processor, also known as the Core Ultra 200V series, is being fully manufactured by TSMC for the…
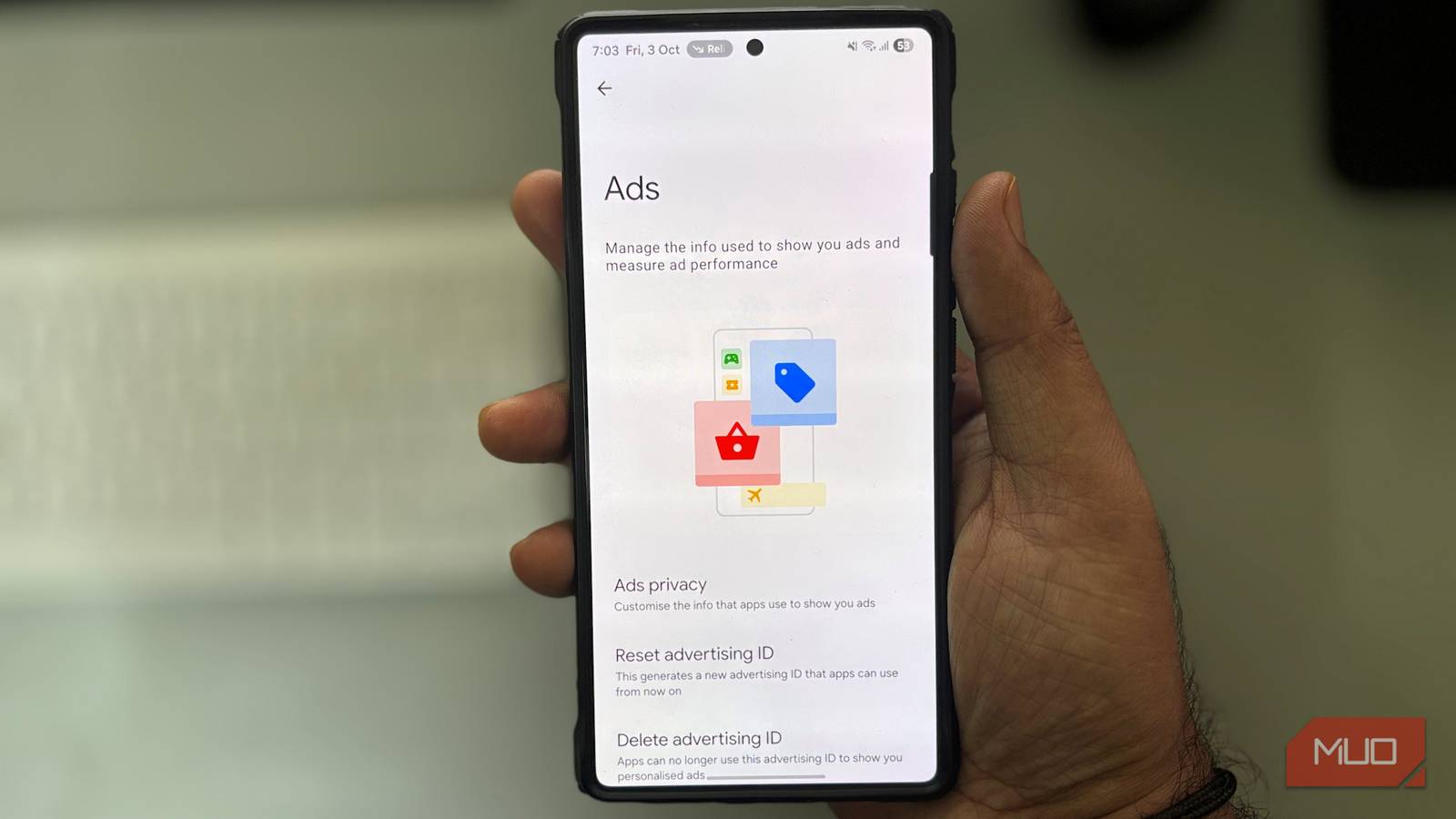
The creepy targeted ads on my phone vanished after I changed one setting
The ads on my phone were getting too personal. I could look up headphones once and then see them everywhere,…
Silo Africa takes on $4 billion post-harvest challenge
In Kenya, harvest season is bittersweet for farming communities. They work the land for months, but within weeks of harvest,…
Stop Memorizing—Start Forecasting: How Superforecasters Outthink Experts | HackerNoon
Here's a statistic that will shatter your faith in "expertise": In a landmark 20-year study, Wharton professor Philip Tetlock proved…
Detour Dog Caught Running DNS-Powered Malware Factory for Strela Stealer
A threat actor named Detour Dog has been outed as powering campaigns distributing an information stealer known as Strela Stealer.…
Out of Office: Luca Cazzanti’s AI and data skills are in play while coaching kids in the sport he loves
Luca Cazzanti, a Seattle AI and data professional, shows off his soccer skills during a break from his coaching duties…
Free Software Foundation Names New President
A new Free Software Foundation president has been elected. Geoffrey Knauth had been serving as president of the FSF since…
CATL builds first factory in northern China, deepens partnership with BAIC · TechNode
CATL announced on Tuesday it is establishing a giant new battery plant on an area of 260,000 square meters (2.8…
Excel’s Quick Analysis menu is the shortcut you’re ignoring
Excel has this useful feature that probably most people completely overlook—the Quick Analysis menu. If you've been manually creating charts,…