DeepSeek accelerates launch of next-gen AI model amid China’s AI push · TechNode
Chinese AI startup DeepSeek is fast-tracking the launch of its R2 model after the success of its earlier release, R1,…
AI is Nigeria’s new music disruptor, but not its replacement
The year is 2014, and Nigerian singer-songwriter, Harrysong, is one of the biggest stars in Africa. After a couple of…
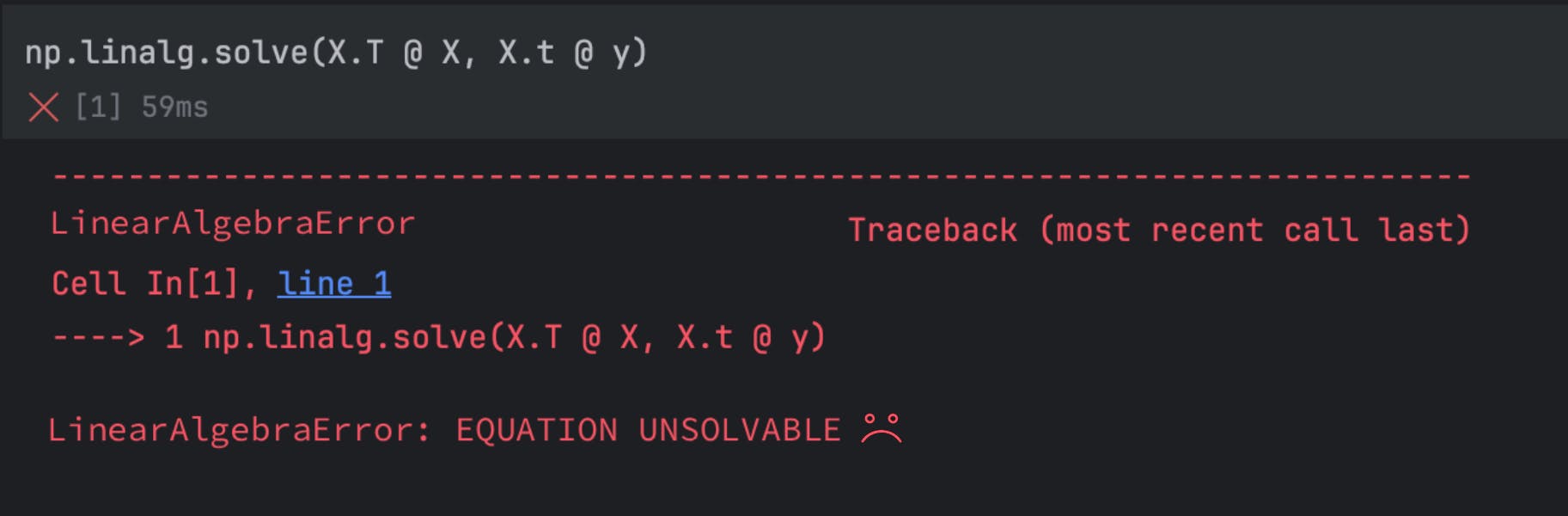
Model.fit is More Complex Than it Looks | HackerNoon
Discover AnythingHackernoonSignupWrite New StorybyIvan SmirnovbyIvan Smirnov@loneasML | WEB | SCIENCESubscribeDecember 12th, 2025TLDR Your browser does not support the audio element.Audio…
AMD ROCm 7.10 Released – Strix Point APUs Now Officially Supported
Sure enough, yesterday's inaugural TheRock 7.10 release tag ended up being a precursor to ROCm 7.10 as predicted in the…
Xpeng Motors prepares for ADAS available outside of China: CEO · TechNode
Xpeng Motors is adapting its advanced driver-assistance system for overseas markets outside China this year and could make the feature…
7 African startups redefining travel, training, transportation, and treatment |
Startups On Our Radar spotlights African startups solving African challenges with innovation. In our previous edition, we featured seven game-changing…
Obscura Brings Bulletproofs++ to the Beldex Mainnet for Sustainable Scaling | HackerNoon
Since 2018, Beldex has evolved into a major privacy network with a growing ecosystem of decentralized, privacy-preserving dApps. From private…
Linux Patches Fix eMMC Secure Erase Of 1GB Taking ~10 Minutes To Now Just 2 Seconds
A new patch series from an NXP engineer optimizes the secure erase performance for certain Kingston eMMC devices. Currently with…
Chinese GPU firm MetaX plans to lay off 200 employees ahead of IPO launch · TechNode
Chinese GPU maker MetaX is initiating a pre-IPO layoff plan, affecting around 200 employees, or 20% of its 900-person workforce,…
How WrappedCBDC’s cNGN stablecoin works
WrappedCBDC set out to fix how Nigerians move money with a naira-backed stablecoin. After 11 months and 1 billion tokens…