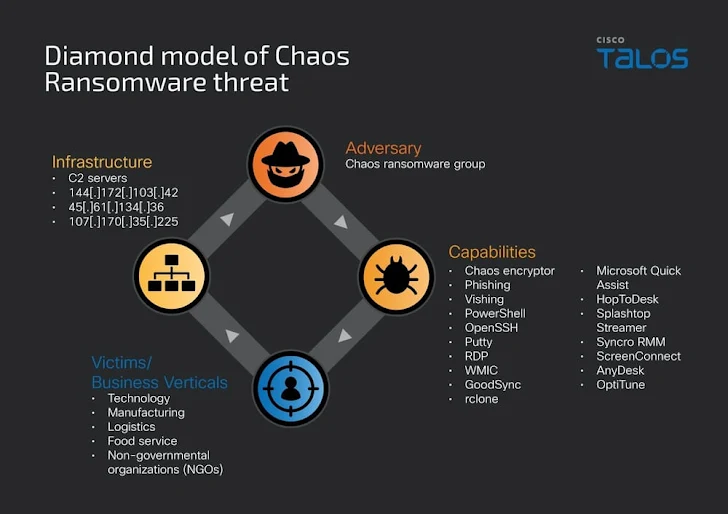
A newly emerged ransomware-as-a-service (RaaS) gang called Chaos is likely made up of former members of the BlackSuit crew, as the latter’s dark web infrastructure has been the subject of a law enforcement seizure.
Chaos, which sprang forth in February 2025, is the latest entrant in the ransomware landscape to conduct big-game hunting and double extortion attacks.
“Chaos RaaS actors initiated low-effort spam flooding, escalating to voice-based social engineering for access, followed by RMM tool abuse for persistent connection and legitimate file-sharing software for data exfiltration,” Cisco Talos researchers Anna Bennett, James Nutland, and Chetan Raghuprasad said.
“The ransomware utilizes multi-threaded rapid selective encryption, anti-analysis techniques, and targets both local and network resources, maximizing impact while hindering detection and recovery.”
It’s important to note here that the ransomware group is unrelated to the Chaos ransomware builder variants such as Yashma and Lucky_Gh0$t, indicating that the threat actors are using the same name to sow confusion. A majority of the victims are located in the United States, based on data from Ransomware.live.
Compatible with Windows, ESXi, Linux and NAS systems, Chaos has been observed seeking ransoms of $300,000 from victims in exchange for a decryptor and a “detailed penetration overview with main kill chain and security recommendations.”
The attacks involve a combination of phishing and voice phishing techniques to obtain initial access by tricking victims into installing remote desktop software, particularly Microsoft Quick Assist.

The threat actors subsequently carry out post-compromise discovery and reconnaissance, followed by installing other RMM tools such as AnyDesk, ScreenConnect, OptiTune, Syncro RMM, and Splashtop to establish persistent remote access to the network.
Also undertaken are steps to harvest credentials, delete PowerShell event logs, and delete security tools installed on the machine to undermine detection. The attacks culminate with the deployment of the ransomware, but not before lateral movement and data exfiltration using GoodSync.
The ransomware binary supports multithreading to facilitate rapid encryption of both local and network resources, all while blocking recovery efforts and implementing multi-layered anti-analysis techniques to evade debugging tools, virtual machine environments, automated sandboxes, and other security platforms.
The links to BlackSuit stem from similarities in the tradecraft employed, including in the encryption commands, the theme and structure of the ransom note, and the RMM tools used. It’s worth noting that BlackSuit is a rebrand of the Royal ransomware group, which, in itself, was an offshoot of Conti, highlighting the shape-shifting nature of the threat.
The development comes around the same time BlackSuit’s dark web sites were seized as part of a joint law enforcement effort called Operation Checkmate. Visitors are greeted by a splash screen that states, “This site has been seized by U.S. Homeland Security Investigations as part of a coordinated international law enforcement investigation.” There has been no official statement from authorities on the takedown.
In a related move, the U.S. Federal Bureau of Investigation (FBI) and the Department of Justice (DoJ) publicly announced the seizure of 20.2891382 BTC (now valued at over $2.4 million) from a cryptocurrency wallet address associated with a member of the Chaos ransomware group known as Hors.
Chaos is the latest entrant to the ransomware landscape, which has also witnessed the arrival of other new strains like Backups, Bert, BlackFL, BQTLOCK, Gunra, Jackalock, Moscovium, RedFox, and Sinobi. Assessed to be based on the infamous Conti ransomware, Gunra has claimed 13 victims since late April 2025.
“Gunra ransomware employs advanced evasion and anti-analysis techniques used to infect Windows Operating systems while minimizing the risk of detection,” CYFIRMA said. “Its evasion capabilities include obfuscation of malicious activity, avoidance of rule-based detection systems, strong encryption methods, ransom demands, and warnings to publish data on underground forums.”

Other recent ransomware attacks include the use of DLL side-loading to drop NailaoLocker and ClickFix-like lures to trick users into downloading malicious HTML Application (HTA) files under the pretext of completing a CAPTCHA verification check and spreading Epsilon Red ransomware.
“Epsilon Red ransomware, first identified in 2021, leaves a ransom note on infected computers that bears a resemblance to the REvil ransomware note, albeit with minor grammatical improvements,” CloudSEK said.
According to NCC Group, ransomware attacks in the second quarter of 2025 dropped 43% to 1,180, a decline from 2,074 in Q1 2025. Qilin has become the most active ransomware group during the time period, leading with 151 attacks, followed by Akira at 131, Play at 115, SafePay at 108, and Lynx at 46. In all, a total of 86 new and existing active attack groups are estimated to be active in 2025.
“The volume of victims being exposed on ransomware leak sites might be declining but this doesn’t mean threats are reduced,” Matt Hull, Global Head of Threat Intelligence at NCC Group, said.
“Law enforcement crackdowns and leaked ransomware source code is possibly a contributing factor as to a drop in activity, but ransomware groups are using this opportunity to evolve through rebranding and the use of advanced social engineering tactics.”