Paul Jones / Android Authority
TL;DR
- The team behind the /e/OS Android fork has addressed some security claims about the platform.
- This comes after GrapheneOS developers criticized /e/OS for “lagging far behind” in terms of updates.
- The /e/OS software ships on the Fairphone Gen 6 in the US.
The Fairphone Gen 6 will launch in the US next month using the Google-free /e/OS platform. However, the developers behind the privacy-focused GrapheneOS Android fork made a few concerning claims about this platform. The team behind /e/OS has now published a blog post addressing these claims.
Murena, the company behind /e/OS, published a blog post stating that it took security issues seriously. However, it also criticized the GrapheneOS developers for making what it called “misleading claims.”
The team confirmed that it targeted “standard industry practices” for timely security updates:
Therefore, for a given release on month N, our current work-flow is to integrate Android security patches from month N-1. As a result, in the worst case, it will take up to nine weeks to roll out the latest available security updates. In most cases, it will be much sooner.
The team also explained that it makes an exception for zero-day exploits and tries to deliver these patches “as soon as possible.” It also posted a table showing how major Android smartphone makers compare in terms of update lag. This suggests that /e/OS is in line with some major OEMs as far as typical patches go. You can view this screenshot below.
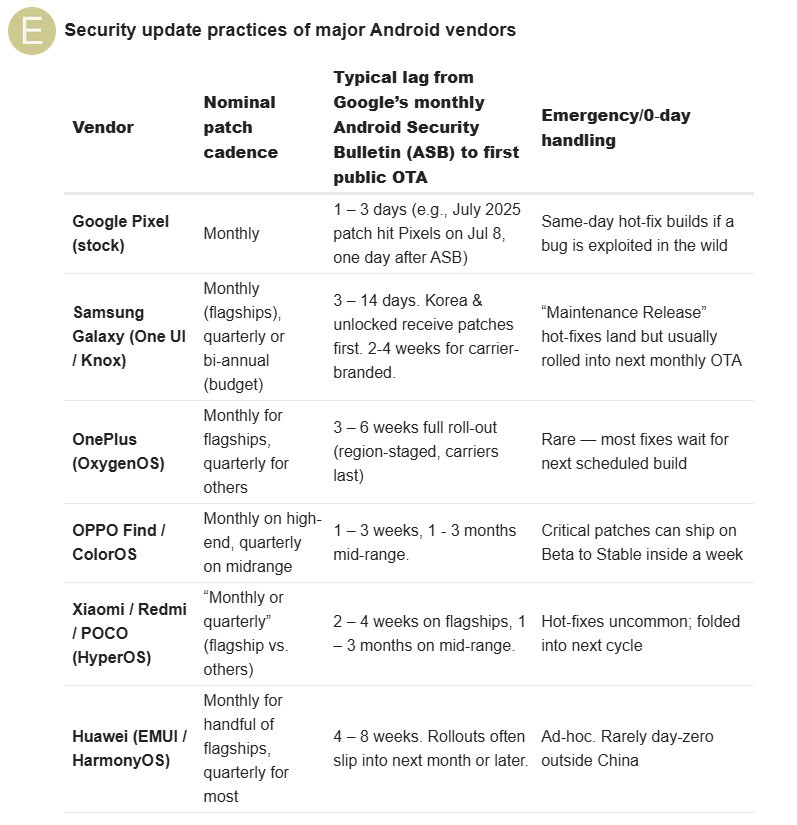
Murena also took umbrage with claims that it lagged on browser updates for WebView issues. The company said it issued two zero-day WebView fixes and the June security patch level with the recently released /e/OS 3.0.4 update. For what it’s worth, these two zero-day exploits were disclosed in early June and late June, respectively.
What’s next for Murena, though? Well, the company confirmed that it will be making some improvements:
Murena is taking security issues seriously, and our policy about integration of security patches in /e/OS is very comparable to or even better in some cases than many of mobile OS vendors in the smartphone industry.
However, as part of our ongoing efforts to continuously improve we have decided to reduce the integration time of monthly security updates in /e/OS. Therefore we’ll progressively update our build infrastructure to allow the roll-out of latest security updates following the days after they have been released.
Murena will continue to deploy urgent /e/OS builds for 0-day security fixes
The company also disputed several other claims by the GrapheneOS team. For one, it said that /e/OS didn’t hide the true patch level but exposes these fields “exactly like stock Android.” The GrapheneOS developers argued that the Fairphone Gen 6 lacks a secure element, which made it “trivial” for bad actors to brute-force a PIN code or basic password. Murena downplayed these assertions, arguing that Qualcomm’s secure processing unit means it could take “years” for attackers to recover a six-digit PIN.
What do you think of /e/OS’s security and privacy?
2 votes
Murena also confirmed that it uses the open-source microG framework to hook into a few Google services (e.g. push notifications) but adds that users can swap Google’s notification service out for the UnifiedPush platform. It’s worth noting that microG is a long-established, popular alternative to Google Play Services that allows people to use Google apps and services. This framework is particularly useful on devices for custom ROMs and HUAWEI phones, which typically lack Google services. So this is a sensible inclusion if you want to let people use some Google apps on an otherwise deGoogled platform.
There’s evidently some room for Murena and Fairphone to improve their security practices. However, not every Android fork has the same security and privacy priorities. Thankfully, the beauty of the Android ecosystem means you can switch to a different Android skin, Android fork, or custom ROM if you have specific needs. In any event, you can read the full blog post for a more comprehensive response by the /e/OS team.