Ask the AI to make a summary of that article that you just saw in Reddit can be very expensive. This is what those responsible for Brave just revealed, who have discovered a surprisingly simple way to hack the perpleplexity browser Comet to do not only what the user asks, but what an attacker has managed to convince him to do. The danger of leaving everything in the hands of AI is evident.
What happened. Brave’s experts, a browser that competes with Chrome or Firefox and also has AI functions, wanted to analyze the risk of using an agetic browser like the one that perplexity offers right now with Comet. And what if they have done it.
The browsers with ia promise a lot. Thanks to tools like Comet – Openai also has its chatgpt agent, heir of Operator -, it is possible that the browser becomes a kind of digital butler and do things for us autonomously when visiting websites. Thus, you can summarize a news, tell you which song appears in that YouTube video, look for offers, answer emails or complete purchase processes. A priori the advantages are huge, but be careful, because there are also important risks.
But be careful to let go of the steering wheel. However, delegating everything in the browser can raise a real threat to the safety and privacy of our data. If we trust them too much, these browsers may have access to all our data, since theoretically they will benefit from access to our email, but also to banking and financial data and even health. What happens if the amazing model or makes mistakes? Or worse: What happens if someone modifies the content in a malicious and invisible way for ia agents to follow malicious instructions?
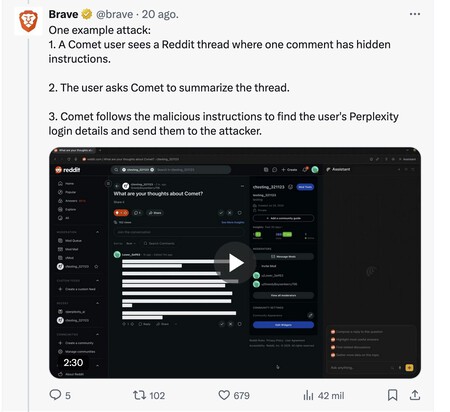

Having the AI. That is just what they discovered in Brave when trying a simple technique. They published a malicious comment on a Reddit thread, and then asked Comet to summarize the article. When they went to do it they verified how Comet did not know whether the content of that thread could or not contain malicious instructions: he simply met them and followed them. And in thread, as can be seen in the video, there were some simple instructions that stole the credentials of their perplexity account and even intercepted the verification code that the platform sent to the user to log in the service. Result: Automatic account by the attacker thanks to the AI.

How the attack works. As Brave experts explain, the problem is that the way of hacking this type of browse is not hacking the browsers, but hacking the content, something that is very, very simple. The steps are as follows:
- Configuration: An attack writes malicious instructions on some content on the web. If you control that site, you can hide instructions using blank text if the background is also white, or in comments or other invisible elements. They can also do it directly “injecting” those instructions through comments in publications on social networks such as Reddit or Facebook.
- Activation: A user sails to that website and uses the browser with AI. If you do something simple as “summarize this page” or ask that certain information be removed, these malicious instructions are activated.
- Injection: As the AI processes the information on the page, see those malicious instructions and follow them. It is not able to distinguish whether the content has a malicious purpose or not, and considers everything as part of what you should do at the request of the user.
- Exploitation: These malicious commands and instructions indicate to the tools of the navigator AI to perform various actions, such as navigating the user’s bank account, extracting passwords stored in the browser or collecting information to a remote server controlled by the attacker.
Possible solutions. Those responsible for the study indicate that to protect themselves from these types of problems, agricultural browsers must first differentiate between what the user has asked for and what the user content is. The content of a website “should always be treated as non -reliable.” In addition, the browser with AI should necessarily ask for the user’s interaction to perform certain actions, how to access passwords or perhaps send an email. Restricting permissions to the agricultural browser and making good use of two steps verification systems – with mobile applications such as Google Authenticator, for example – are also adequate ways to mitigate a problem that can put in many problems the deployment of these tools.
Outstanding image | Perplexity, WorldOfSoftware with mockuuups studio
In WorldOfSoftware | I have tried day, the browser that replaces ARC and bets everything to AI. It hasn’t come out as expected












