Table Of Links
Abstract
1. Introduction
2. Background
- Memory Tagging Extension
- Speculative Execution Attack
3. Threat Model
4. Finding Tag Leakage Gadgets
- Tag Leakage Template
- Tag Leakage Fuzzing
5. TIKTAG Gadgets
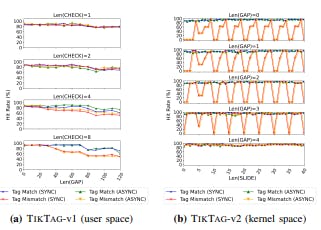
- TIKTAG-v1: Exploiting Speculation Shrinkage
- TIKTAG-v2: Exploiting Store-to-Load Forwarding
6. Real-World Attacks
6.1. Attacking Chrome
7. Evaluation
8. Related work
9. Conclusion And References
Related work
MTE Security Analysis. Partap et al. [51] analyzed the software-level MTE support in real-world memory allocators. Google Project Zero [38] explored speculative execution attacks against MTE hardware for the first time. StickyTags [22] identified an MTE tag leakage gadget (which is similar to TIKTAG-v1) and proposed a deterministic tagging-based defense that does not utilize random tags due to the potential tag leakage. Compared to StickyTags, our work identified a new type of MTE tag leakage gadget, TIKTAG-v2, and analyzed the root cause of both TIKTAG-v1 and TIKTAG-v2 gadgets.
We also demonstrated the realworld exploitation of TIKTAG gadgets in Google Chrome and the Linux kernel and proposed new defense mechanisms to mitigate the security risks posed by TIKTAG gadgets. While StickyTags proposed deterministic tagging due to the potential tag leakage, our work focuses on hardening the random tagging-based MTE defense, which are developed by major vendors including Google [39], the Linux kernel [26], and secure operating systems [23, 50, 63].
Speculative Attacks on Protection Mechanisms. Speculative probing [20] suggested that speculative execution can be used to probe address mappings and bypass address space layout randomization (ASLR). PACMAN [54] identified speculative gadgets that leak Pointer Authentication Code (PAC). ARMv8.6 FEAT_FPAC mitigates PACMAN attacks by authentication and memory access, allowing all memory accesses regardless of the authentication result [35]. MTE tag leakage can also be mitigated by separating tag check and memory access in the hardware, not allowing tag check results to affect memory access.
Transient Execution Attacks. Transient execution attacks exploit micro-architectural behaviors to leak secret information. Researchers have analyzed various micro-architectural implementations including speculative execution [30, 36, 66, 71], memory disambiguation prediction [24, 41, 45], and CPU internal buffers [67, 68]. Recent attacks exploited data prefetching behaviors to leak secret information or construct covert channels [14, 57, 59, 69]. Compared to these attacks, we identified for the first time that data prefetching behaviors can also be exploited to leak hardware exceptions, such as tag check faults (§5.1).
9. Conclusion
This paper explores the potential security risks posed by speculative execution attacks against ARM Memory Tagging Extension (MTE). We identify new MTE oracles, TIKTAG-v1 and TIKTAG v2, capable of leaking MTE tags from arbitrary memory addresses. TIKTAG gadgets can bypass MTE-based defense in real-world systems, including Google Chrome and the Linux kernel. Our findings provide significant insights into the design and deployment of both memory taggingbased hardware and software defenses.
References
[1] Gigacage. https://phakeobj.netlify.app/posts/gigacage/.
[2] base/allocator/partitionallocator/partitionbucket.cc. https: //source.chromium.org/chromium/chromium/src/+/main: base/allocator/partitionallocator/src/partitionalloc/partition_ bucket.cc?q=TagMemoryRangeRandomly&start=21.
[3] external/scudo/standalone/combined.h. https://cs. android.com/android/platform/superproject/main/+/main: external/scudo/standalone/combined.h;l=1225;drc= dd7fe3fedd9446067b06d31fdf6c191760405e6d;bpv=0;bpt=1.
[4] Pointer authentication on armv8.3, 2017. https://www.qualcomm.com/ media/documents/files/whitepaper-pointer-authentication-on-armv8- 3.pdf.
[5] Memory tagging extension, 2019. https://developer.arm.com/- /media/Arm%20Developer%20Community/PDF/ArmMemory TaggingExtensionWhitepaper.pdf.
[6] M. Abadi, M. Budiu, U. Erlingsson, and J. Ligatti. Control-flow integrity principles, implementations, and applications. In Proceedings of the ACM Transactions on Information and System Security, Nov. 2009.
[7] R. Abhishek, K. M. Bruce, and A. P. TONNERRE. Skipping tag check for tag-checked load operation, 2020. https://patents.google. com/patent/US11221951/.
[8] A. Agarwal, S. O’Connell, J. Kim, S. Yehezkel, D. Genkin, E. Ronen, and Y. Yarom. Spook. js: Attacking chrome strict site isolation via speculative execution. In Proceedings of the 42rd IEEE Symposium on Security and Privacy (Oakland), San Francisco, CA, May 2022.
[9] D. N. Armstrong, H. Kim, O. Mutlu, and Y. N. Patt. Wrong path events: Exploiting unusual and illegal program behavior for early misprediction detection and recovery. In Proceedings of the 37th Annual IEEE/ACM International Symposium on Microarchitecture (MICRO), Portland, OR, Dec. 2004.
[10] M. Bakhshalipour, P. Lotfi-Kamran, and H. Sarbazi-Azad. Domino temporal data prefetcher. In 2018 IEEE International Symposium on High Performance Computer Architecture (HPCA), pages 131–142. IEEE, 2018.
[11] G. S. Blog. Mte – the promising path forward for memory safety. https://security.googleblog.com/2023/11/mte-promising-pathforward-for-memory.html.
[12] L. CAI, K. Nathella, J. Lee, and S. Dam. Prefetch mechanism for a cache structure, 2020. https://patents.google.com/patent/ US11526356B2/.
[13] M. Castro, M. Costa, and T. Harris. Securing software by enforcing data-flow integrity. In Proceedings of the 7th USENIX Symposium on Operating Systems Design and Implementation (OSDI), Seattle, WA, Nov. 2006.
[14] Y. Chen, L. Pei, and T. E. Carlson. Afterimage: Leaking control flow data and tracking load operations via the hardware prefetcher. In Proceedings of the 28th ACM International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS), Vancouver, Canada, Apr. 2023.
[15] Chromium. [pac] enable armv8.3 pac (pointer authentication code).
[16] M. W. Docs. Sharedarraybuffer. https://developer.mozilla.org/en-US/ docs/Web/JavaScript/Reference/Global_Objects/SharedArrayBuffer. [17] eBPF. ebpf documentation. https://ebpf.io/what-is-ebpf/.
[18] J. Edge. Kernel address space layout randomization, 2013. https: //lwn.net/Articles/569635/.
[19] J. W. Fu, J. H. Patel, and B. L. Janssens. Stride directed prefetching in scalar processors. volume 23, pages 102–110. ACM New York, NY, USA, 1992.
[20] E. Göktas, K. Razavi, G. Portokalidis, H. Bos, and C. Giuffrida. Speculative probing: Hacking blind in the spectre era. In Proceedings of the 27th ACM Conference on Computer and Communications Security (CCS), Virtual, Nov. 2022.
[21] Google. Spectre, 2021. https://leaky.page.
[22] F. Gorter, T. Kroes, H. Bos, and C. Giuffrida. Sticky tags: Efficient and deterministic spatial memory error mitigation using persistent memory tags. In Proceedings of the 43rd IEEE Symposium on Security and Privacy (Oakland), San Francisco, CA, May 2024.
[23] GrapheneOS. hardenedmalloc. https://github.com/GrapheneOS/ hardenedmalloc.
[24] S. Islam, A. Moghimi, I. Bruhns, M. Krebbel, B. Gulmezoglu, T. Eisenbarth, and B. Sunar. {SPOILER}: Speculative load hazards boost rowhammer and cache attacks. In Proceedings of the 28th USENIX Security Symposium (Security), Santa Clara, CA, Aug. 2019.
[25] P. Z. Jann Horn. Reading privileged memory with a sidechannel. https://googleprojectzero.blogspot.com/2018/01/readingprivileged-memory-with-side.html.
[26] T. L. Kernel. Hardware tag-based kasan. https://docs.kernel.org/devtools/kasan.html#hardware-tag-based-kasan.
[27] J. Kim, S. van Schaik, D. Genkin, and Y. Yarom. ileakage: Browserbased timerless speculative execution attacks on apple devices. In Proceedings of the 30th ACM Conference on Computer and Communications Security (CCS), Copenhagen, Denmark, Nov. 2022.
[28] O. Kirzner and A. Morrison. An analysis of speculative type confusion vulnerabilities in the wild. In Proceedings of the 30th USENIX Security Symposium (Security), Virtual, Aug. 2021.
[29] S. Knox. Real-time kernel protection (rkp).
[30] P. Kocher, J. Horn, A. Fogh, D. Genkin, D. Gruss, W. Haas, M. Hamburg, M. Lipp, S. Mangard, T. Prescher, M. Schwarz, and Y. Yarom. Spectre attacks: Exploiting speculative execution. In Proceedings of the 40th IEEE Symposium on Security and Privacy (Oakland), San Jose, CA, May 2019.
[31] G. Li, H. Zhang, J. Zhou, W. Shen, Y. Sui, and Z. Qian. A hybrid alias analysis and its application to global variable protection in the linux kernel.
[32] H. Liljestrand, C. Chinea, R. Denis-Courmont, J.-E. Ekberg, and N. Asokan. Color my world: Deterministic tagging for memory safety. arXiv preprint arXiv:2204.03781, 2022.
[33] A. Limited. Cache speculation side-channels, . https://developer.arm. com/documentation/102816/0205/.
[34] A. Limited. Speculative oracles on memory tagging, . https://developer. arm.com/documentation/109544/latest.
[35] A. Limited. Pacman security vulnerability, . https://developer.arm. com/documentation/ka005109/latest/.
[36] M. Lipp, M. Schwarz, D. Gruss, T. Prescher, W. Haas, A. Fogh, J. Horn, S. Mangard, P. Kocher, D. Genkin, Y. Yarom, and M. Hamburg. Meltdown: Reading kernel memory from user space. In Proceedings of the 27th USENIX Security Symposium (Security), Baltimore, MD, Aug. 2018.
[37] G. P. Z. Mark Brand. Mte as implemented, part 3: The kernel, . https://googleprojectzero.blogspot.com/2023/08/mte-as-implementedpart-3-kernel.html.
[38] G. P. Z. Mark Brand. Mte as implemented, part 1: Implementation testing, . https://googleprojectzero.blogspot.com/2023/08/mte-asimplemented-part-1.html.
[39] G. P. Z. Mark Brand. First handset with mte on the market, 2023. https://googleprojectzero.blogspot.com/2023/11/first-handsetwith-mte-on-market.html.
[40] D. McKee, Y. Giannaris, C. O. Perez, H. Shrobe, M. Payer, H. Okhravi, and N. Burow. Preventing kernel hacks with hakc. In Proceedings of the 2022 Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, Apr. 2022.
[41] M. Minkin, D. Moghimi, M. Lipp, M. Schwarz, J. Van Bulck, D. Genkin, D. Gruss, F. Piessens, B. Sunar, and Y. Yarom. Fallout: Reading kernel writes from user space. In Proceedings of the 26th ACM Conference on Computer and Communications Security (CCS), London, UK, Nov. 2019.
[42] Mitre. Cve-2020-6449, . https://cve.mitre.org/cgi-bin/cvename.cgi? name=CVE-2020-6449.
[43] Mitre. Cve-2022-0185, . https://cve.mitre.org/cgi-bin/cvename.cgi? name=CVE-2022-0185.
[44] Mitre. Cve-2023-5217, . https://cve.mitre.org/cgi-bin/cvename.cgi? name=CVE-2023-5217.
[45] MITRE. Cve-2018-3639. https://cve.mitre.org/cgi-bin/cvename.cgi? name=CVE-2018-3639.
[46] MITRE. CVE-2019-2215., 2019. https://cve.mitre.org/cgi-bin/ cvename.cgi?name=CVE-2019-2215.
[47] K. Mitsunami. Delivering enhanced security through memory tagging extension. https://community.arm.com/arm-communityblogs/b/architectures-and-processors-blog/posts/enhanced-securitythrough-mte.
[48] O. Oleksenko, C. Fetzer, B. Köpf, and M. Silberstein. Revizor: Testing black-box cpus against speculation contracts. In Proceedings of the 42rd IEEE Symposium on Security and Privacy (Oakland), San Francisco, CA, May 2022.
[49] J. Olšan. Cortex-x3: the new fastest core from arm (architecture analysis). https://fuse.wikichip.org/news/6855/arm-unveils-next-genflagship-core-cortex-x3/.
[50] OP-TEE. libutils: add mte support in malloc() and friends. https://github.com/OP-TEE/optee_os/commit/ 08a5c4f9ae421384e52b87107283181e3fddf056.
[51] A. Partap and D. Boneh. Memory tagging: A memory efficient design, 2022.
[52] A. O. S. Project. Control flow integrity, 2022. https://source.android. com/docs/security/test/cfi.
[53] T. C. Projects. Site isolation. https://www.chromium.org/Home/ chromium-security/site-isolation/.
[54] J. Ravichandran, W. T. Na, J. Lang, and M. Yan. Pacman: attacking arm pointer authentication with speculative execution. In Proceedings of the 49th ACM/IEEE International Symposium on Computer Architecture (ISCA), New York, USA, June 2022.
[55] N. L. Rocco. Arm-kerne 2022: Cortex-a715 und cortex-a510 refresh: Effizienz im fokus. https://www.computerbase.de/2022-06/arm-cortexx3-a715-a510-refresh/3/.
[56] saelo. V8 sandbox. https://docs.google.com/document/d/ 1FM4fQmIhEqPG8uGp5o9A-mnPB5BOeScZYpkHjo0KKA8/edit.
[57] T. Schlüter, A. Choudhari, L. Hetterich, L. Trampert, H. Nemati, A. Ibrahim, M. Schwarz, C. Rossow, and N. O. Tippenhauer. Fetchbench: Systematic identification and characterization of proprietary prefetchers. In Proceedings of the 30th ACM Conference on Computer and Communications Security (CCS), Copenhagen, Denmark, Nov. 2022.
[58] M. Schwarz, C. Maurice, D. Gruss, and S. Mangard. Fantastic timers and where to find them: High-resolution microarchitectural attacks in javascript. In Financial Cryptography and Data Security: 21st International Conference, FC 2017, Sliema, Malta, April 3-7, 2017, Revised Selected Papers 21, pages 247–267. Springer, 2017.
[59] Y. Shin, H. C. Kim, D. Kwon, J. H. Jeong, and J. Hur. Unveiling hardware-based data prefetcher, a hidden source of information leakage. In Proceedings of the 25th ACM Conference on Computer and Communications Security (CCS), Tronto, Canada, Oct. 2018.
[60] C. Song, B. Lee, K. Lu, W. Harris, T. Kim, and W. Lee. Enforcing kernel security invariants with data flow integrity. In Proceedings of the 2016 Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, Feb. 2016.
[61] S. S. Stone, K. M. Woley, and M. I. Frank. Address-indexed memory disambiguation and store-to-load forwarding. In Proceedings of the 38th Annual IEEE/ACM International Symposium on Microarchitecture (MICRO), Barcelona, Spain, Dec. 2005.
[62] C. Tice, T. Roeder, P. Collingbourne, S. Checkoway, Ú. Erlingsson, L. Lozano, and G. Pike. Enforcing forward-edge control-flow integrity in {GCC} & {LLVM}. In Proceedings of the 23rd USENIX Security Symposium (Security), San Diego, CA, Aug. 2014.
[63] Trustonic. Armv9-a: How our kinibi 600 trusted os utilises mte and ff-a features to create state-of-the-art tees. https://www.trustonic.com/technical-articles/armv9-a-how-ourkinibi-600-trusted-os-utilises-mte-and-ff-a-features-to-create-stateof-the-art-tees/.
[64] V8. Pointer compression in v8, . https://v8.dev/blog/pointercompression.
[65] V8. v8/include/v8-internal.h, . https://github.com/v8/v8/blob/ 7161638e5ead74bf84a52d27e69ebda26fbd2416/include/v8- internal.h#L235C11-L235C11.
[66] J. Van Bulck, M. Minkin, O. Weisse, D. Genkin, B. Kasikci, F. Piessens, M. Silberstein, T. F. Wenisch, Y. Yarom, and R. Strackx. Foreshadow: Extracting the keys to the intel {SGX} kingdom with transient {Outof-Order} execution. In Proceedings of the 27th USENIX Security Symposium (Security), Baltimore, MD, Aug. 2018.
[67] J. Van Bulck, D. Moghimi, M. Schwarz, M. Lippi, M. Minkin, D. Genkin, Y. Yarom, B. Sunar, D. Gruss, and F. Piessens. Lvi: Hijacking transient execution through microarchitectural load value injection. In Proceedings of the 41st IEEE Symposium on Security and Privacy (Oakland), Virtual, USA, May 2020.
[68] S. Van Schaik, A. Milburn, S. Österlund, P. Frigo, G. Maisuradze, K. Razavi, H. Bos, and C. Giuffrida. Ridl: Rogue in-flight data load. In Proceedings of the 40th IEEE Symposium on Security and Privacy (Oakland), San Jose, CA, May 2019.
[69] J. R. S. Vicarte, M. Flanders, R. Paccagnella, G. Garrett-Grossman, A. Morrison, C. W. Fletcher, and D. Kohlbrenner. Augury: Using data memory-dependent prefetchers to leak data at rest. In Proceedings of the 42rd IEEE Symposium on Security and Privacy (Oakland), San Francisco, CA, May 2022.
[70] P. Vila, B. Köpf, and J. F. Morales. Theory and practice of finding eviction sets. In Proceedings of the 40th IEEE Symposium on Security and Privacy (Oakland), San Jose, CA, May 2019.
[71] J. Wikner and K. Razavi. {RETBLEED}: Arbitrary speculative code execution with return instructions. In Proceedings of the 3125 USENIX Security Symposium (Security), Boston, MA, Aug. 2022.
[72] H. Xiao and S. Ainsworth. Hacky racers: Exploiting instruction-level parallelism to generate stealthy fine-grained timers. In Proceedings of the 28th ACM International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS), Vancouver, Canada, Apr. 2023.
:::info
Authors:
- Juhee Kim
- Jinbum Park
- Sihyeon Roh
- Jaeyoung Chung
- Youngjoo Lee
- Taesoo Kim
- Byoungyoung Lee
:::
:::info
This paper is available on arxiv under CC 4.0 license.
:::