Antivirus software is not free from errors and sometimes reports computer viruses when they are not present. For this reason, the company Procolored, a manufacturer of textile printers, indignantly defended itself against a printer tester’s report that the software of one of its devices contained a virus.
The testing official explained to Procolored that both Google Chrome and Microsoft Defender had triggered an alarm when the printer software was downloaded and quarantined it.
Despite Procolored’s protests, the tester persisted. He sent the software to security company G Data, a manufacturer of antivirus programs.
Upon investigation, it was found that the printer software actually contained a backdoor virus called Xred and a Trojan horse.
When G Data subsequently confronted Procolored with the results, the company admitted that a virus had crept into the download area and provided a new version of the software.
With the online sandbox Any.run you can start suspicious programs in a virtual Windows environment and study their behavior.
Foundry
How false alarms arise
Procolored’s initially defensive attitude is understandable. After all, antivirus programs sometimes recognize malware where there is none.
But not often. Long-term tests have repeatedly shown that false alarms typically make up less than 1 percent of virus reports. However, they are always annoying, as many users initially become alarmed when their computer reports malware.
How do these false positives come about?
It has to do with the way antivirus programs work. On the one hand, they have access to daily updated virus definitions, with which they can recognize intruders very reliably.
However, because there are also many previously unknown malware threats on the Internet for which no virus definitions exist, manufacturers also integrate heuristic and behavioral analysis methods into their software. Heuristic means that the programs look for suspicious characteristics of a file or program.
Behavioral analysis, on the other hand, observes the programs running on the PC. Both methods work with probabilities and calculate whether a program with these or those characteristics could be a virus. False alarms occasionally occur.
System programs are especially affected
False alarms are especially common with programs that access system settings or data that the antivirus program classifies as confidential or even secret.
This applies, for example, to several tools from software company Nirsoft, such as the Produkey program. It reads the license keys for Windows and Office 2003/2007 and displays them in the window.
In itself an innocent process, but it apparently provides the antivirus software with enough suspicious facts to classify the application as a virus.
The same applies to many other programs that read data such as license keys or passwords or change system settings. The antivirus software’s heuristics look, among other things, for combinations of certain system calls that are typical of malware.
However, well-known hacker tools, such as those used to crack passwords, are also blocked by the virus guards. Even though they are legally offered for download. Hacking your own computer, for example to reconstruct a forgotten password, is not prohibited.
A perfectly functioning antivirus program that does not give false alarms is an illusion. On the one hand, the software should under no circumstances miss malware, on the other hand it should recognize harmless programs as such.
It is therefore inevitable that the virus hunter plays it safe on a case-by-case basis and labels software as dangerous even when it is not.
Check the false alarm trigger
If your virus protection triggers an alarm, you should always investigate the trigger yourself. Otherwise, there is a risk that the antivirus program will block parts of the software that are absolutely necessary for it to function. A multi-stage procedure is recommended.
Check the purpose of the tool: As a first step, you should consider what you have downloaded. If it is one of the tools already mentioned for determining license codes or passwords, you can assume that it is a false alarm.
Check for reputation: However, you should also check where you got the software from and think about its reputation. To do this, you need to look at the file that caused the alarm and clarify its origin.
If you use Microsoft Defender as virus protection, you can find the file and its origin in “Settings” under “Privacy & security > Windows security > Virus & threat protection > Security history.”
All malware found by Defender is listed there. Click on one of the entries to find out the file name and origin. There are similar folders in every other antivirus program.
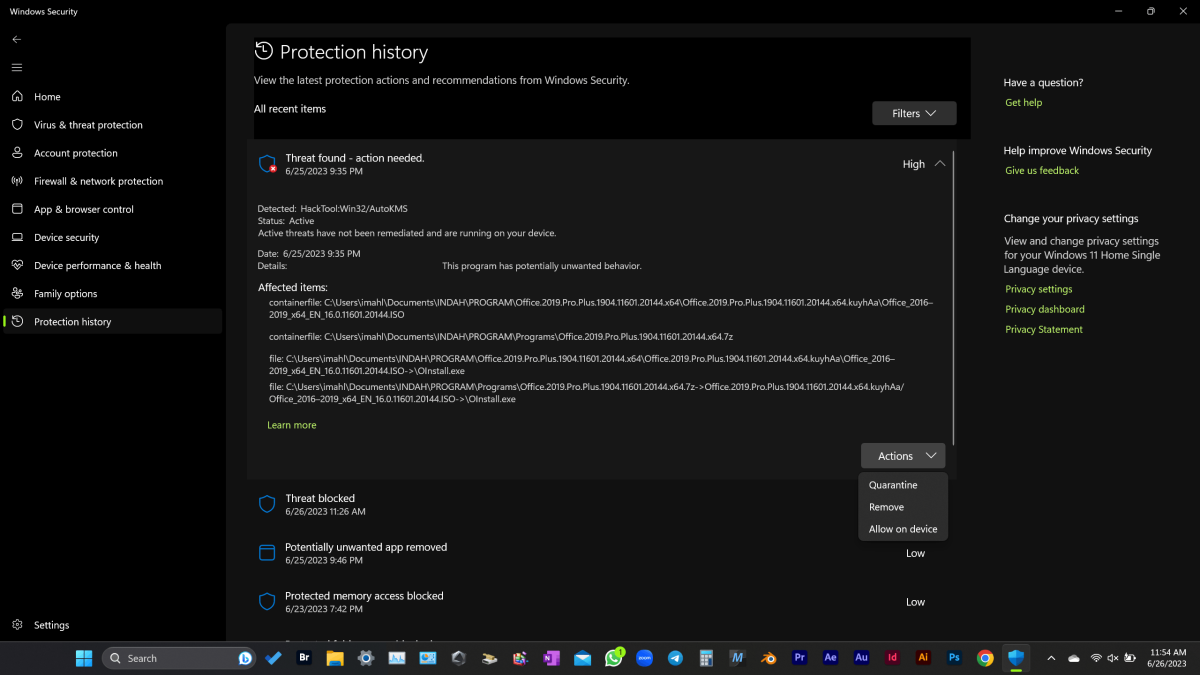
Defender lists the most recently found threats and shows you details if desired. To do this you need to point the mouse at an area. A pop-down menu will then appear.
Microsoft
It is important to know where you got the file from and whether this download site has a good or bad reputation.
Sites that offer cracked programs and games or tools for hacking license applications, for example, have a bad reputation. Hackers often use this software to deliver malware to users’ computers.
Websites that illegally make films and videos available for download also fall into this category.
Check for signs of social engineering: Social engineering refers to tricks that cause someone to exhibit certain behaviors that they would not exhibit without these tricks.
Social engineering is regularly used in phishing of private data and, somewhat less often, in the distribution of malware. For example, emails or text messages claim that an order is at risk of getting stuck in the mail if you do not take action quickly and install a service tool. However, this is actually a virus.
If the antivirus program now reports malware, there is a good chance that it is actually malware. Typical social engineering techniques are pressure, urgency, emergencies and requests for help.
Beware of scams: The general rule on the internet is that if something seems too good to be true, it usually is. These can, for example, be very favorable purchase offers. If a virus message appears in such a context, it is probably justified.
What to do in case of a false alarm
If your antivirus software identifies a downloaded program as malware, but you are sure it is not, you can define the download file or the address of its source on the Internet as an exception. Each security program offers a corresponding feature.
Use alternative virus scanners
If your antivirus program has reported malware and you are not sure whether it is actually malware or a false alarm, the next step is to request a second opinion from another antivirus program.
There’s no need to uninstall your existing software and then download and install a competitor’s product. It is faster and easier to scan the suspicious file with an online scanner.
Some antivirus manufacturers offer online scanners as a free service on their website. There is an area where you can upload suspicious files to the manufacturer’s servers and have them scanned there.
Corresponding offers are available from Eset, F-Secure and Trend Micro.
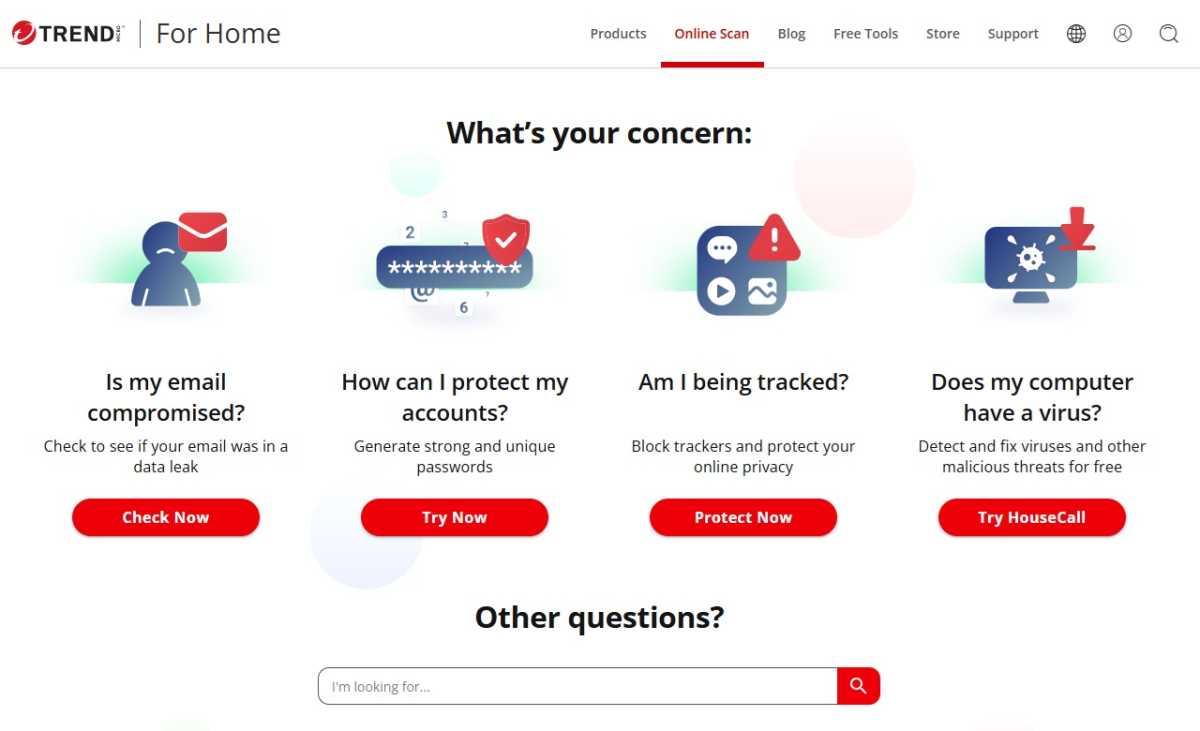
You can use Trend Micro’s online scanner to scan your computer for existing malware. No installation is required.
Foundry
Or you can go straight to Virustotal, Google’s online scanner. It presents the suspicious file to several dozen antivirus programs from different manufacturers and displays their scan results.
Although there have been isolated cases in the past where Virustotal also failed to recognize malware, this is probably the safest way to rule out false alarms.
There are also alternatives to Virustotal, including Metadefender Cloud, Hybrid Analysis, and Jotti’s Malware Scan.

Jotti’s Malware Scan is an alternative to Virustotal and sends uploaded files to a total of 13 different antivirus scanners. There is a data limit of 250 MB per file.
Foundry
Offline scanning with bootable USB sticks and DVDs
If you frequently use different computers, you can also install a virus scanner on a bootable USB stick or DVD. This way you can check the PC in question first before starting your work.
There are several ways to obtain such a stick or DVD. Some antivirus programs include wizards that allow you to create a portable version on a stick or DVD directly from the software.
This applies to the identical programs from Avast and AVG and the paid Norton Antivirus.
The downside: You must first install the appropriate antivirus program to create the disk.
Other manufacturers offer rescue disks as ready-made downloads. These drives are usually based on a Linux live system that is supplemented with a virus scanner. They are available from Avira and Kaspersky.
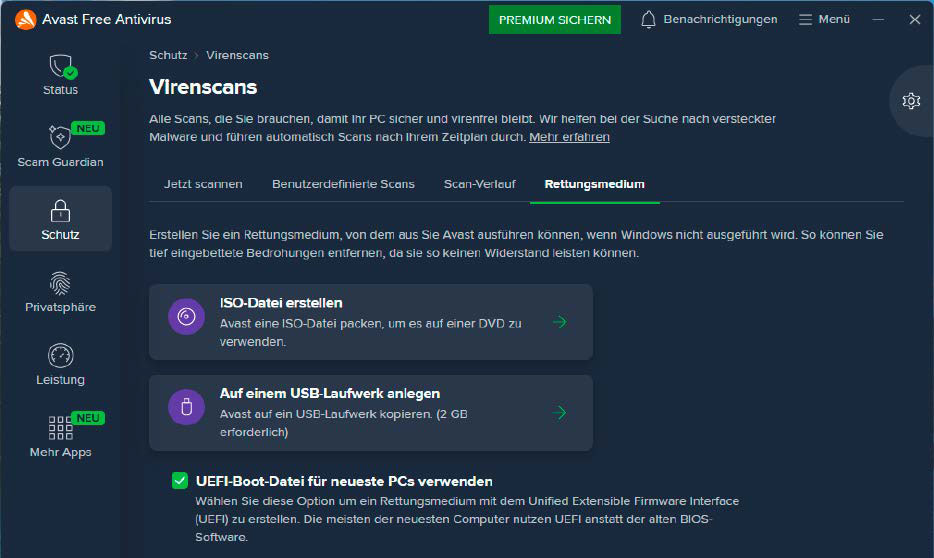
After installing an additional component, the Avast virus scanner offers the possibility of creating a rescue disk on DVD or USB stick with an integrated virus scanner.
Foundry
Thirdly, you can also use Sardu. This freeware allows you to create bootable USB drives and DVDs and equip them with an antivirus program of your choice.
For this purpose, Sardu provides links to freely available rescue systems from antivirus manufacturers and offers to download the programs directly and integrate them onto the stick or DVD.
Launch suspicious programs safely
Another method to detect false alarms is to run a suspicious program in a secure environment.
This can be a virtual machine in which you install Windows and then start the software to be analyzed.
If it carries a virus, it will remain locked in the virtual machine. As a rule, it is not possible to go to your desktop Windows. So you can take your time to observe whether it is, for example, ransomware that is now starting to encrypt the virtual SSD.
The alternative is to use a sandbox. This is also a protected environment that offers no opportunity for malware to break out. Online sandboxes like Any.run are easy to use, but you can also use locally installable sandbox software like Sandboxie.
Caution: Many viruses are programmed in such a way that they only become active after a period of several hours, days or even weeks. So if a program in a sandbox initially shows no anomalies, that does not mean that it is definitely safe.
Virus warnings as bait
Especially in the dark corners of the Internet, browser windows appear time and again informing you that a virus has been found on your PC. To solve the problem, you should immediately agree to download an antivirus program.
Caution: These messages are invariably scams. The software offered normally has no function. However, it tries to convince you to pay for a license by showing regular notices.
Worse still, these programs often contain a virus themselves, which can turn your PC into part of a botnet, for example.
Related content
This article originally appeared in our sister publication PC-WELT and was translated and localized from German.










