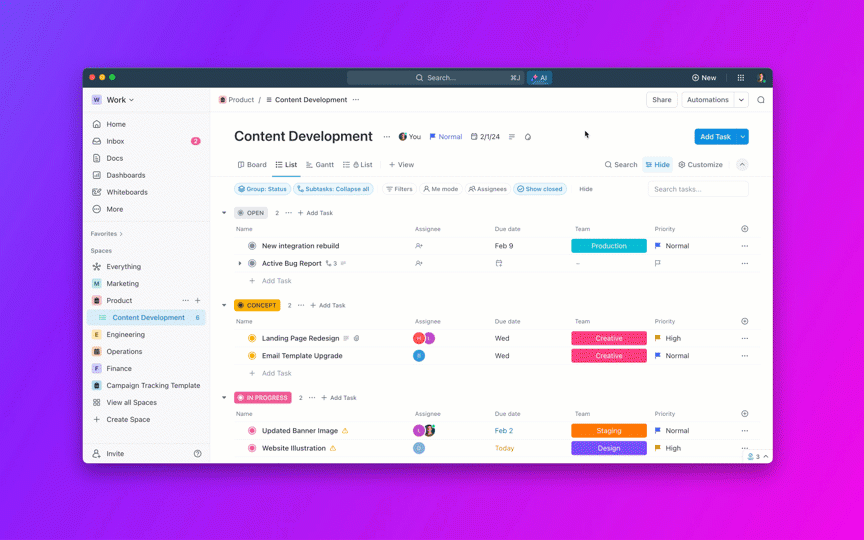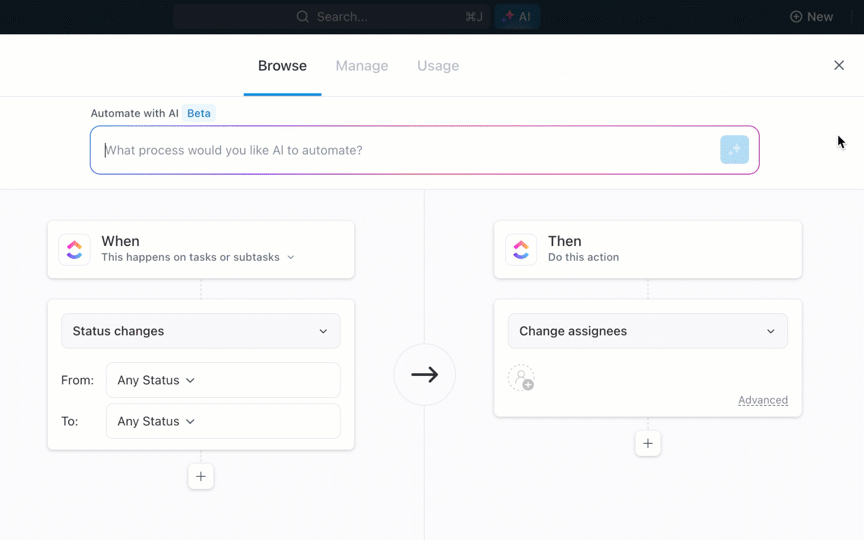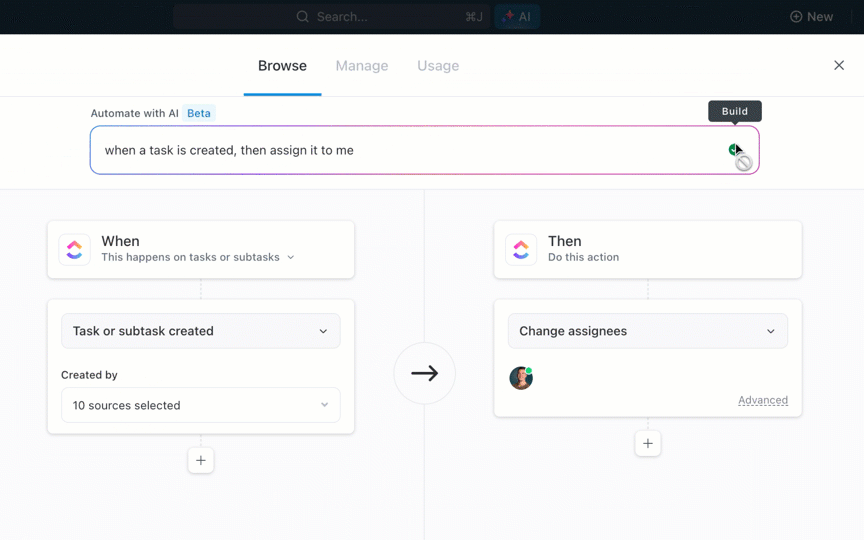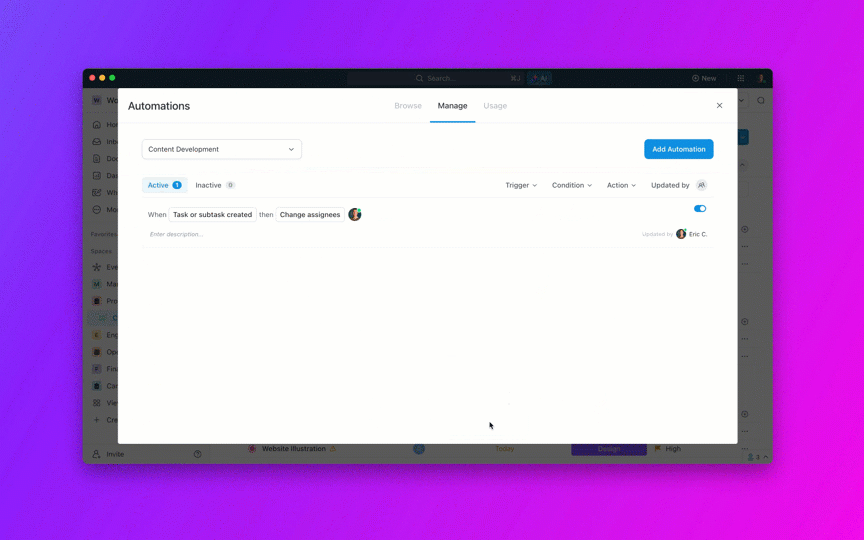
Cybersecurity researchers have flagged an updated version of the LightSpy implant that comes equipped with an expanded set of data collection features to extract information from social media platforms like Facebook and Instagram.
LightSpy is the name given to a modular spyware that’s capable of infecting both Windows and Apple systems with an aim to harvest data. It was first documented in 2020, targeting users in Hong Kong.
This includes Wi-Fi network information, screenshots, location, iCloud Keychain, sound recordings, photos, browser history, contacts, call history, and SMS messages, and data from various apps like Files, LINE, Mail Master, Telegram, Tencent QQ, WeChat, and WhatsApp.
Late last year, ThreatFabric detailed an updated version of the malware that incorporates destructive capabilities to prevent the compromised device from booting up, alongside expanding the number of supported plugins from 12 to 28.
Previous findings have also uncovered potential overlaps between LightSpy and an Android malware named DragonEgg, highlighting the cross-platform nature of the threat.
Hunt.io’s latest analysis of the malicious command-and-control (C2) infrastructure associated with the spyware has uncovered support for over 100 commands spanning Android, iOS, Windows, macOS, routers, and Linux.

“The new command list shifts focus from direct data collection to broader operational control, including transmission management (‘传输控制’) and plugin version tracking (‘上传插件版本详细信息’),” the company said.
“These additions suggest a more flexible and adaptable framework, allowing LightSpy operators to manage deployments more efficiently across multiple platforms.”
Notable among the new commands is the ability to target Facebook and Instagram application database files for data extraction from Android devices. But in an interesting twist, the threat actors have removed iOS plugins associated with destructive actions on the victim host.
Also discovered are 15 Windows-specific plugins designed for system surveillance and data collection, with most of them geared towards keylogging, audio recording, and USB interaction.
The threat intelligence firm said it also discovered an endpoint (“/phone/phoneinfo”) in the admin panel that grants logged-in users the ability to remotely control the infected mobile devices. It’s currently not known if these represent new developments or previously undocumented older versions.

“The shift from targeting messaging applications to Facebook and Instagram expands LightSpy’s ability to collect private messages, contact lists, and account metadata from widely used social platforms,” Hunt.io said.
“Extracting these database files could provide attackers with stored conversations, user connections, and potentially session-related data, increasing surveillance capabilities and opportunities for further exploitation.”
The disclosure comes as Cyfirma disclosed details of an Android malware dubbed SpyLend that masquerades as a financial app named Finance Simplified (APK name “com.someca.count”) on the Google Play Store but engages in predatory lending, blackmail, and extortion aimed at Indian users.
“By leveraging location-based targeting, the app displays a list of unauthorized loan apps that operate entirely within WebView, allowing attackers to bypass Play Store scrutiny,” the company said.
“Once installed, these loan apps harvest sensitive user data, enforce exploitative lending practices, and employ blackmail tactics to extort money.”
Some of the advertised loan apps are KreditPro (formerly KreditApple), MoneyAPE, StashFur, Fairbalance, and PokketMe. Users who install Finance Simplified from outside India are served a harmless WebView that lists various calculators for personal finance, accounting, and taxation, suggesting that the campaign is designed to specifically target Indian users.
The app is no longer available for download from the official Android app marketplace. According to statistics available on Sensor Tower, the application was published around mid-December 2024 and attracted over 100,000 installations.

“Initially presented as a harmless finance management application, it downloads a fraud loan app from an external download URL, which once installed, gains extensive permissions to access sensitive data, including files, contacts, call logs, SMS, clipboard content, and even the camera,” Cyfirma pointed out.
Indian retail banking customers have also become the target of another campaign that distributes a malware codenamed FinStealer that impersonates legitimate bank apps, but is engineered to collect login credentials and facilitate financial fraud by carrying out unauthorized transactions.
“Distributed via phishing links, and social engineering, these fake apps closely mimic legitimate bank apps, tricking users into revealing credentials, financial data, and personal details,” the company said.
“Using Telegram bots, the malware can receive instructions and send stolen data without raising suspicion, making it more difficult for security systems to detect and block the communication.”