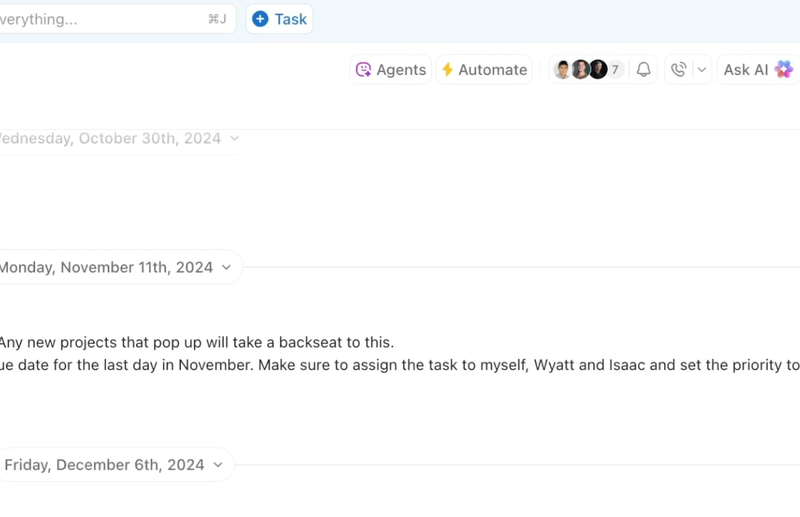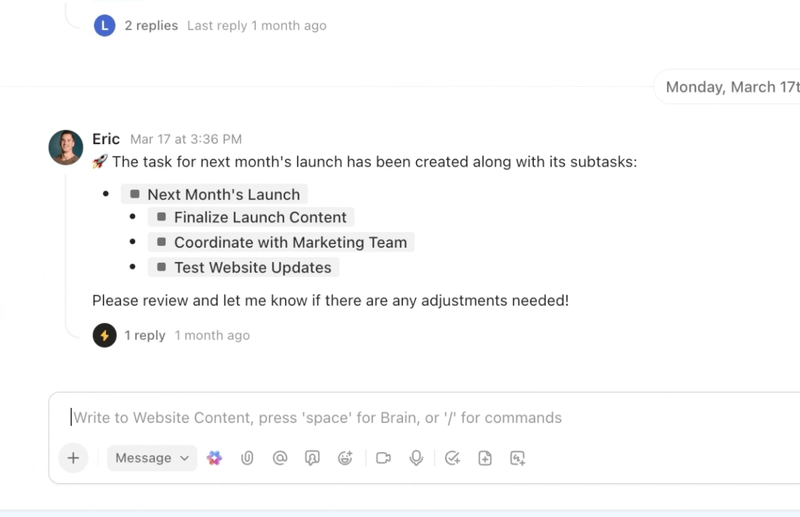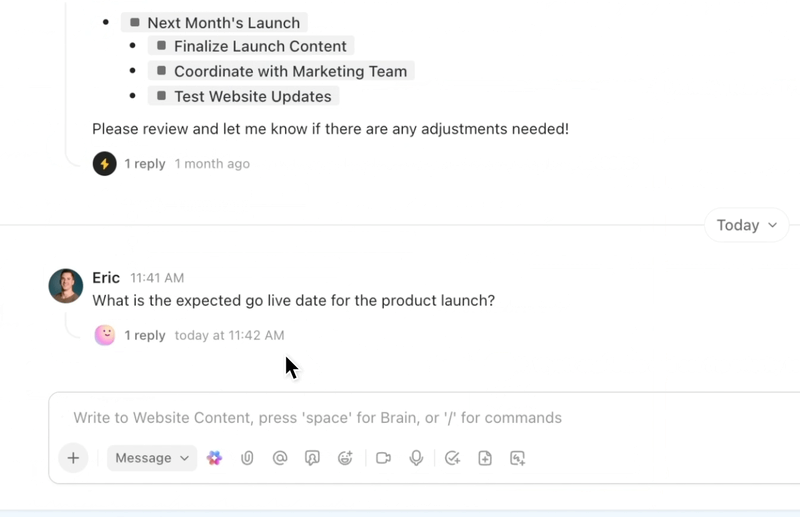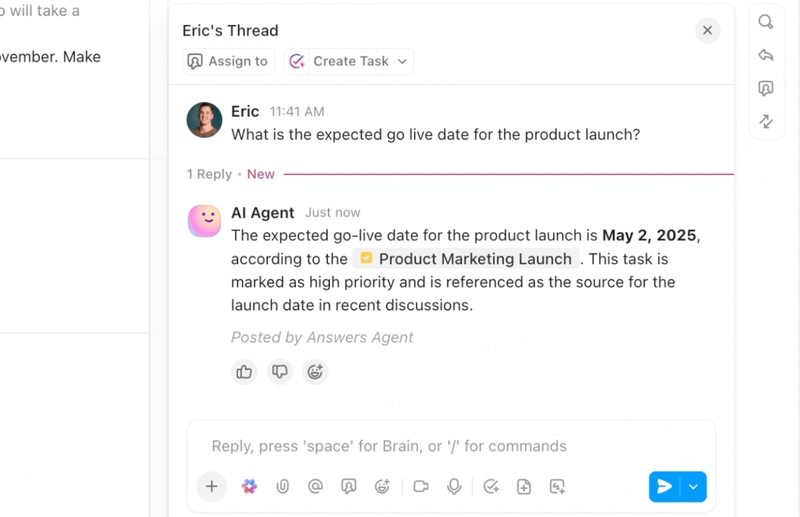
Cybersecurity researchers have lifted the lid on two threat actors that orchestrate investment scams through spoofed celebrity endorsements and conceal their activity through traffic distribution systems (TDSes).
The activity clusters have been codenamed Reckless Rabbit and Ruthless Rabbit by DNS threat intelligence firm Infoblox.
The attacks have been observed to lure victims with bogus platforms, including cryptocurrency exchanges, which are then advertised on social media platforms. An important aspect of these scams is the use of web forms to collect user data.
“Reckless Rabbit creates ads on Facebook that lead to fake news articles featuring a celebrity endorsement for the investment platform,” security researchers Darby Wise, Piotr Glaska, and Laura da Rocha said. “The article includes a link to the scam platform which contains an embedded web form persuading the user to enter their personal information to ‘register’ for the investment opportunity.”
Some of these forms, besides requesting users’ names, phone numbers, and email addresses, offer the ability to auto-generate a password, a key piece of information that’s used to progress to the next phase of the attack — validation checks.
The threat actors perform HTTP GET requests to legitimate IP validation tools, such as ipinfo[.]io, ipgeolocation[.]io, or ipapi[.]co, in order to filter out traffic from countries that they are not interested in. Checks are also carried out to ensure that the provided numbers and email addresses are authentic.
Should the user be deemed worthy of exploitation, they are subsequently routed through a TDS that either takes them directly to the scam platform where they are coaxed into parting with their funds by promising high returns, or to a different page that instructs them to wait for a call from their representative.
“Some campaigns use call centers to provide the victims with instructions on how to set up an account and transfer money into the fake investment platform,” the researchers explained. “For users who do not pass the validation step, many campaigns will simply display a ‘thank you’ landing page.”
An important aspect of the activity is the use of a registered domain generation algorithm (RDGA) to set up domain names for the sketchy investment platforms, a technique also adopted by other threat actors like Prolific Puma, Revolver Rabbit, and VexTrio Viper.

Unlike traditional domain generation algorithms (DGAs), RDGAs a secret algorithm to register all the domain names. Reckless Rabbit is said to have been creating domains as far back as April 2024, primarily targeting users in Russia, Romania, and Poland, while excluding traffic from Afghanistan, Somalia, Liberia, Madagascar, and others.
The Facebook ads used to direct users to the fake news articles are interspersed with advertising content related to items listed for sale on marketplaces like Amazon in a bid to evade detection and enforcement action.
What’s more, the ads contain unrelated images and display a decoy domain (e.g., “amazon[.]pl”) that’s different from the actual domain the user will be redirected to once they click on the link (e.g., “tyxarai[.]org”).
Ruthless Rabbit, on the other hand, is believed to have been actively running investment scam campaigns since at least November 2022 that are aimed at Eastern European users. What sets this threat actor apart is that they run their own cloaking service (“mcraftdb[.]tech”) to perform validation checks.

Users who get past the verification checks are subsequently routed to an investment platform where they are urged to enter their financial information to complete the registration process.
“A TDS enables threat actors to strengthen their infrastructure, making it more resilient by providing the ability to hide malicious content from security researchers and bots,” Infoblox said.
This is not the first time such fraudulent investment scam campaigns have been discovered in the wild. In December 2024, ESET exposed a similar scheme dubbed Nomani that uses a combination of social media malvertising, company-branded posts, and artificial intelligence (AI) powered video testimonials featuring famous personalities.
Then last month, Spanish authorities revealed they have arrested six individuals aged between 34 and 57 for allegedly running a large-scale cryptocurrency investment scam that used AI tools to generate deepfake ads featuring popular public figures to deceive people.
Renee Burton, vice president of threat intelligence at Infoblox, told The Hacker News that they “would have to take a closer look to see if there is any evidence” to ascertain if there are any connections between these activities and those conducted by Reckless Rabbit and Ruthless Rabbit.
“Threat actors like Reckless and Ruthless Rabbits will be relentless in their attempts to trick as many users as possible,” the researchers said. “Because these types of scams have proven to be highly profitable for them, they will continue to grow rapidly—both in number and sophistication.”
Mystery Box Scams Proliferate via Facebook Ads
The development comes as Bitdefender is warning of a spike in sophisticated subscription scams that a network of more than 200 convincing fake websites to trick users into paying monthly subscriptions and sharing their credit card data.

“Criminals create Facebook pages and take out full ads to promote the already classic ‘mystery box’ scam and other variants,” the Romanian company said. “The ‘mystery box’ scam has evolved and now includes almost hidden recurring payments, alongside links to websites to various shops. Facebook is used as the main platform for these new and enhanced mystery box scams.”
The rogue sponsored ads advertise clearance sales from brands like Zara or offer a chance to buy a “mystery box” containing Apple products and seek to entice users by claiming that they can grab one of them by paying a minimal sum of money, sometimes as low as $2.
The cybercriminals deploy various tricks to sidestep detection efforts, including creating multiple versions of the ad, only one of which is malicious, while the others display random product images.

These scams, like the ones perpetrated by Reckless Rabbit and Ruthless Rabbit, incorporate a survey component to ensure that the victims are real people and not bots. Additionally, the payment pages rope unsuspecting users into a subscription program that earns the threat actors recurring revenues under the pretext of giving them a discount.
“Criminals have been pumping funds in ads promoting impersonated content creators, using the same subscription model that seems to be now the driving revenue stream of these scams,” Bitdefender researchers Răzvan Gosa and Silviu Stahie said.
“Scammers often change the impersonated brands, and they’ve begun expanding past the existing mystery boxes. They are now trying to sell low-quality products or imitation articles, fake investments, supplements, and much more.”
U.S. Treasury Sanctions Junta-Linked Militia in Myanmar Over Scam Compounds
The findings also follow a wave of sanctions imposed by the U.S. Department of the Treasury against the Myanmar-linked Karen National Army (KNA) for assisting organized crime syndicates operate multi-billion-dollar scam compounds, as well as facilitating human trafficking and cross-border smuggling.
The actions also target the group’s leader Saw Chit Thu, and his two sons, Saw Htoo Eh Moo and Saw Chit Chit. Saw Chit Thu was sanctioned by the United Kingdom in 2023 and the European Union in 2024 for becoming a key enabler of scam operations in the region.
“Cyber scam operations, such as those run by the KNA, generate billions in revenue for criminal kingpins and their associates, while depriving victims of their hard-earned savings and sense of security,” said Deputy Secretary Michael Faulkender.
In these so-called romance baiting scams, fraudsters — who are themselves trafficked to the scam sites by luring them with high-paying jobs — are coerced into targeting strangers online, building rapport with them over time, and then induce them to invest in bogus cryptocurrency and trading platforms controlled by the criminal actors.
“The KNA profits from cyber scam schemes on an industrial scale by leasing land it controls to other organized crime groups, and providing support for human trafficking, smuggling, and the sale of utilities used to provide energy to scam operations,” the Treasury Department said. “The KNA also provides security at scam compounds in Karen State.”
The United Nations Office on Drugs and Crime (UNODC) last month divulged the scam centers are still expanding despite recent crackdowns, generating annual profits to the tune of about $40 billion.