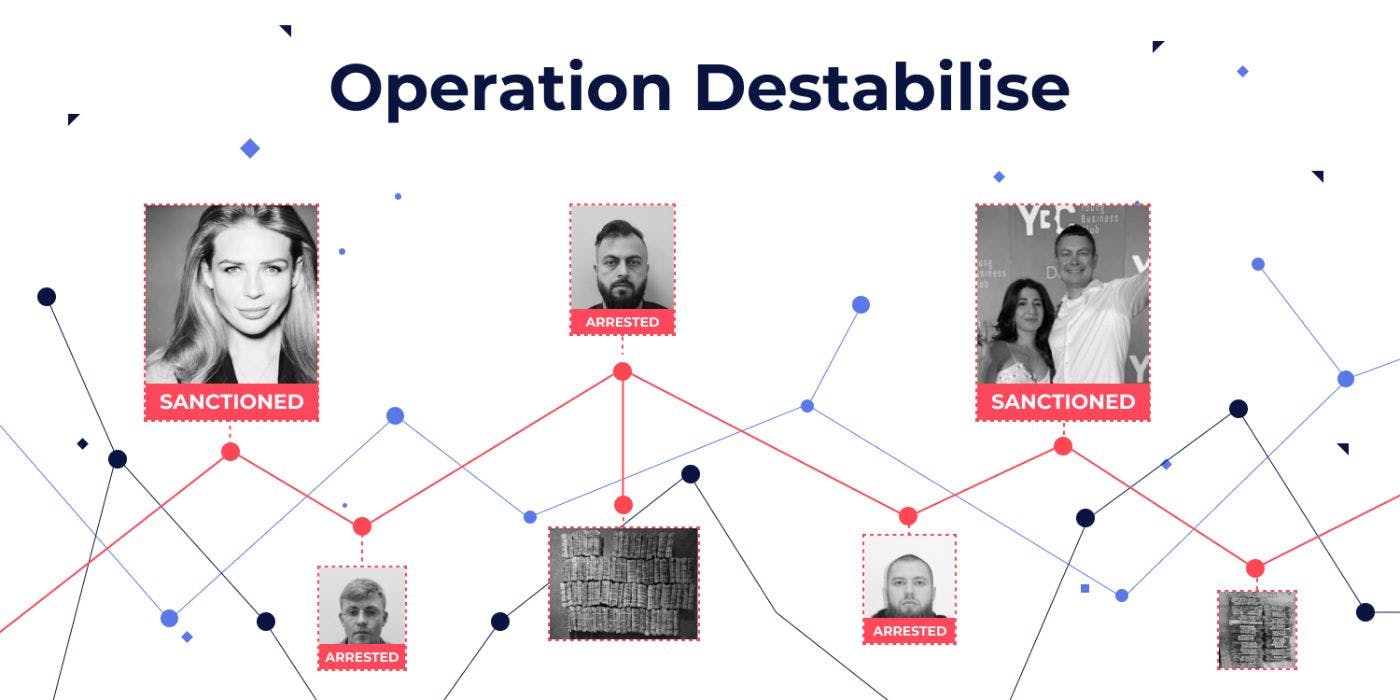
Following the news about
As a reminder, the networks, Smart and TGR, facilitated the movement of criminally gained funds from one country to another using cryptocurrency transfers. Such crypto transactions were used both to launder money and to bypass Western sanctions against Russia.
As a result of the operation, the US Office of Foreign Assets Control (OFAC)
Sanctioned Crypto Addresses: Six Lessons Learned
1. USDT is #1 for laundering
Most laundering operations relied on Tether (USDT), a commonly used stablecoin that preserves the value of transfers. Given the volume of transactions, including numerous cash-to-crypto exchanges, Tether allowed criminals to minimize value loss across transfers.
2. 195M+ USDT laundered via Magomedov’s sanctioned wallet
The total value of cryptocurrency laundered through Magomedov’s sanctioned wallet exceeded USDT 195 million, as outlined in the Counterparty Report below. The laundering activity included interactions with a wide range of counterparties, but the wallet’s largest counterparty was a major centralized exchange.
Source: Gl Vision Protocol — 3. 146K+ USDT laundered through Chirkinyan’s wallet
3. 146K+ USDT laundered through Chirkinyan’s wallet
In contrast, the total value of cryptocurrency transacted through Chirkinyan’s wallet was much smaller, amounting to just over USDT 146,000.
4. Addresses made direct deposits to CEXs, including both well-regulated ones and sanctioned Garantex
Both wallets’ top counterparties included addresses at top well-known and well-regulated crypto exchanges.
However, they also engaged in transactions with the Russian crypto exchange Garantex long after it
As for the number of counterparties involved, Magomedov’s wallet interacted with a significantly greater number of exchanges and counterparties compared to Chirkinyan’s wallet, including activity with a high-risk wallet previously flagged as a reported hack. Chirkinyan’s transactions mostly culminated in deposits to a prominent centralized exchange.
Conversely, Magomedov’s transactions involved multiple counterparties. Notably, Magomedov’s activity did not include numerous hops aimed at obfuscating the flow of funds, opting instead for direct deposits to CEX deposit wallets.
5. Wallets interacted with exchanges requiring partial KYC
Except for CEXs, wallets interacted with exchanges requiring KYC only partially, depending on the customer’s activity, such as where KYC would only be required for crypto transfers, but not fiat ones.
6. Chirkinyan’s wallet received crypto from a Cyprus-based gambling service
One wallet was receiving incoming crypto transfers from a gambling service domiciled in Cyprus, which processes all its transactions in crypto.
Sanctioned Crypto Addresses: Challenges for the Industry
While the two sanctioned wallets are unlikely to continue operating due to their identification by blockchain analytics providers and likely blacklisting by crypto exchanges, numerous connected wallets may continue transacting and being used by professional money launderers. These wallet networks pose ongoing risks. We recommend these wallets be placed under monitoring using a blockchain analytics provider to prevent exposure and ensure compliance.
Even without reusing the wallets spotted as part of the transactional activity linked to the two sanctioned wallets, criminal networks can easily create new crypto addresses. Depending on the type of wallet and the platform being used, creating a wallet can take anywhere from a few seconds to a few minutes. The process could be slower if it includes additional verification steps, such as Know Your Customer procedures, which are usually required by centralized exchanges for custodial wallets but are not often included for decentralized ones.
To sum up
In summary, while sanctioning these wallets was a necessary step, Chirkinyan’s and Magomedov’s wallets are unlikely to be reused for money laundering purposes. However, placing these wallets under monitoring and including them on an internal blacklist are recommended steps for industry players, such as crypto exchanges, to prevent any future exposure and to remain compliant.
We also recommend that the full extent of these wallets’ activity be investigated and understood using a blockchain analytics tool and that all other direct past counterparties of these wallets be placed on a watchlist.
As a common theme of the wallets’ activity was exposure to Garantex even after the exchange was sanctioned, it is advised that crypto industry participants use blockchain analytics to identify and prevent such exposure in the future.
Finally, crypto wallets identified as having frequent high-value incoming and outgoing transactions with an unusually large number of counterparties should be considered as presenting a higher risk of money laundering.