On 7 May 2024, the presumed identity of the operator of the LockBit 3.0 franchise, also known as LockBitSupp, was revealed during UK National Crime Agency and its partners’ Operation Cronos: Dmitry Yuryevich Khoroshev.
One year later, to the day, the entire contents of the SQL database of a web administration interface for the company’s affiliates was made public. And not just anywhere – on the ransomware franchise’s websites. The irony is – they were hacked. The data was extracted on 29 April. It concerns a system that was set up on 18 December last year.
A rare light
This data provides unprecedented visibility into the activities of the LockBit 3.0 ransomware. The compilation dates of the encryption malware make it possible to adjust previous estimates of attack occurrence dates. In the case of certain known victims, they have already revealed a gap of up to 10 days between the end of the exfiltration of the victim’s data and the launch of the encryption. This underlines the importance of efforts to detect such exfiltration.
This data can also be used to attribute different victims to their attackers. This grouping will be useful for analysing negotiation methods and tracking any ransom payments.
This administration interface for affiliates contained 75 user accounts, two of which were most likely used by LockBitSupp itself. No less than 35 accounts were “paused,” two of which had been used against victims in Russia. The company’s operator has assured that this is the reason for their suspension.
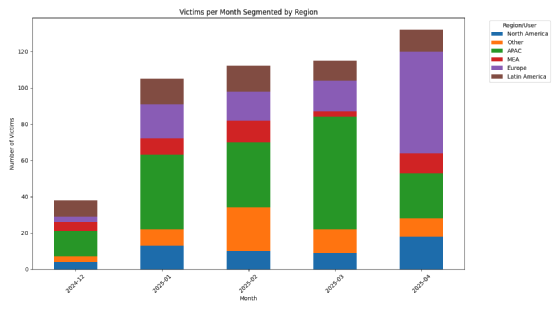
But only 44 accounts were actually used to generate ransomware and possibly launch cyber attacks. Of these, 30 were active on 29 April, but only seven appear to have been engaged in conducting attacks at that time.
LeMagIT
A geographical spread
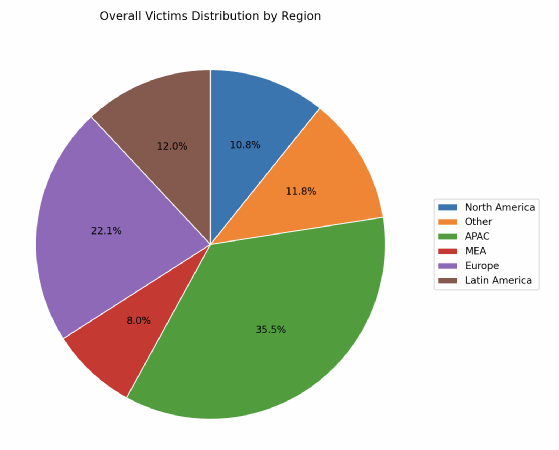
Research into the geographical origins of the victims mentioned reveals an unusual trend – in all likelihood, the Asia-Pacific region was the focus for 35.5% of the efforts of LockBit’s affiliates over the period in question, compared with 22% for Europe, and less than 11% for North America, behind Latin America at 12%.
LeMagIT
But there are very marked disparities between affiliates. PiotrBond, for example, concentrated on the Asia-Pacific region, with 76% of its victims. The same applies to Umarbishop47 (81%). DarraghBerg bet equally (33.3%) on this region and Africa-Middle East. But JamesCraig also gave priority to Asia-Pacific (42%).
This geographical review also highlights the lack of observability of the threat in this region, particularly in China, which accounted for 51 victims in the sample studied. Indonesia comes a close second with 49 victims, followed by India (35).
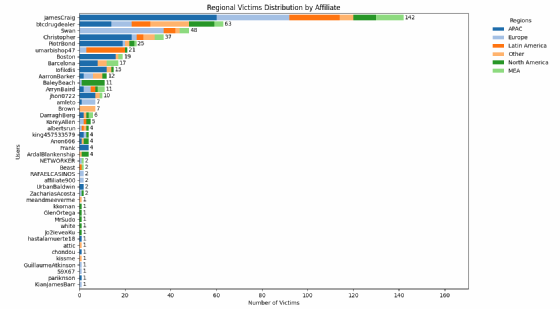
LeMagIT
The data also suggests that South Korea is globally under-represented in observable malicious activity.
This unusual geographical distribution may reflect changes in the profiles recruited by LockBit 3.0. The most active affiliates do not seem to be those who go after the most attractive victims.
The reflection of a tarnished image
The available data suggests instead that those who multiply their victims try to target potentially less mature people than others, even if they have to pay modest sums, in countries with per-capita incomes around the world average.
The negotiations observed support this analysis, with ransom amounts very frequently requested of less than $20,000.
All in all, the LockBit 3.0 banner currently appears to have only two or three active high-flying affiliates. This is only half a surprise – the Cronos international judicial operation dented the image of the mafia-like franchise. If it manages to attract anyone, its appeal is, unsurprisingly, limited.
It even makes you wonder whether some victims who refuse to pay the ransom are deliberately not being claimed on LockBit’s showcase site so as not to tarnish its image even further.
And this new leak is unlikely to improve matters – it has exposed the Tox encrypted email IDs of certain affiliates, their passwords (stored in clear text), and pseudonyms with which certain open source intelligence specialists will no doubt be happy to investigate – not to mention the victims’ private encryption keys.