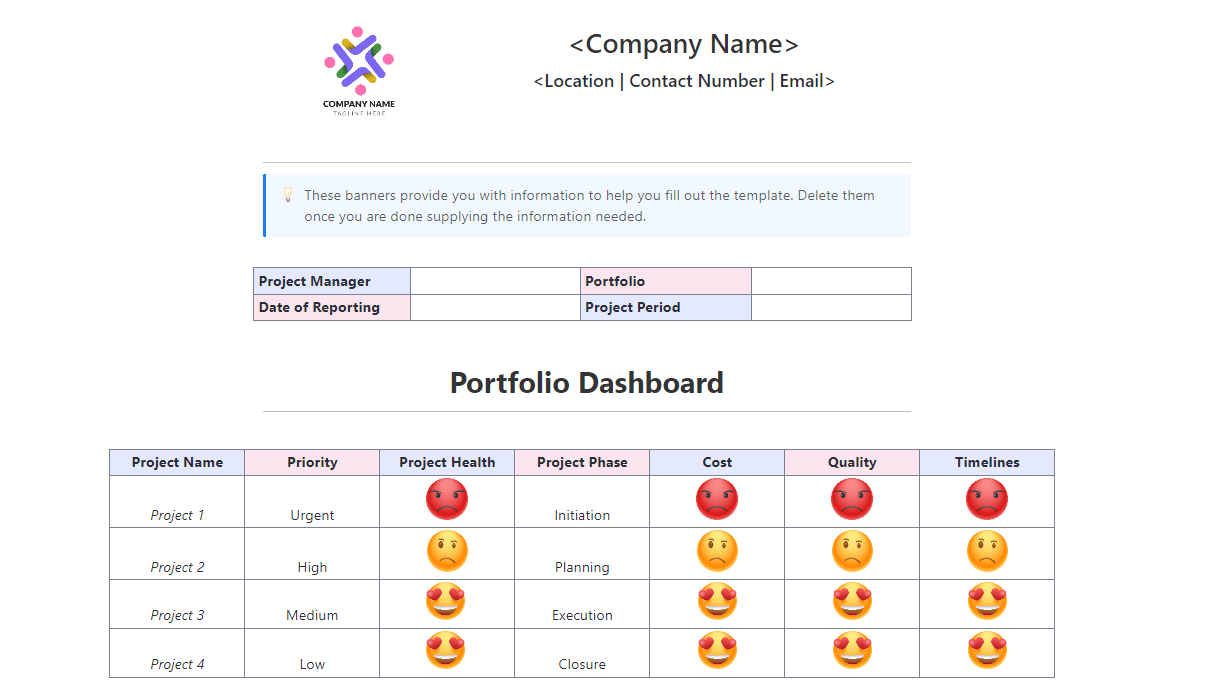
The Russian nation-state threat actor known as Secret Blizzard has been observed orchestrating a new cyber espionage campaign targeting foreign embassies located in Moscow by means of an adversary-in-the-middle (AitM) attack at the Internet Service Provider (ISP) level and delivering a custom malware dubbed ApolloShadow.
“ApolloShadow has the capability to install a trusted root certificate to trick devices into trusting malicious actor-controlled sites, enabling Secret Blizzard to maintain persistence on diplomatic devices, likely for intelligence collection,” the Microsoft Threat Intelligence team said in a report shared with The Hacker News.
The activity is assessed to be ongoing since at least 2024, with the campaign posing a security risk to diplomatic personnel relying on local ISPs or telecommunications services in Russia.
Secret Blizzard (formerly Krypton), affiliated with the Russian Federal Security Service, is also tracked by the broader cybersecurity community under the monikers Blue Python, Iron Hunter, Pensive Ursa, Snake, SUMMIT, Uroburos, Turla, Venomous Bear, and Waterbug.

In December 2024, Microsoft and Lumen Technologies Black Lotus Labs disclosed the hacking group’s use of a Pakistan-based threat actor’s command-and-control (C2) infrastructure to carry out its own attacks as a way to cloud attribution efforts.
The adversary has also been observed piggybacking on malware associated with other threat actors to deliver its Kazuar backdoor on target devices located in Ukraine.
The Windows maker noted that the AitM position is likely facilitated by lawful intercept and includes the installation of root certificates under the guise of Kaspersky antivirus to obtain elevated access to the system.

Initial access is achieved by redirecting target devices to threat actor-controlled infrastructure by putting them behind a captive portal, leading to the download and execution of the ApolloShadow malware.
“Once behind a captive portal, the Windows Test Connectivity Status Indicator is initiated—a legitimate service that determines whether a device has internet access by sending an HTTP GET request to hxxp://www.msftconnecttest[.]com/redirect, which should direct to msn[.]com,” Microsoft said.
“Once the system opens the browser window to this address, the system is redirected to a separate actor-controlled domain that likely displays a certificate validation error, which prompts the target to download and execute ApolloShadow.”

The malware then beacons host information to the C2 server and runs a binary called CertificateDB.exe should the device not be running on default administrative settings, and retrieves as a second-stage payload an unknown Visual Basic Script.
In the last step, the ApolloShadow process launches itself again and presents the user with a user access control (UAC) pop-up window and instructs them to grant it the highest privileges available to the user.

ApolloShadow’s execution path varies if the running process is already running with sufficient elevated privileges, abusing them to set all networks to Private via registry profile changes and create an administrative user with the username UpdatusUser and a hard-coded password, allowing persistent access to the machine.
“This induces several changes, including allowing the host device to become discoverable, and relaxing firewall rules to enable file sharing,” the company said. “While we did not see any direct attempts for lateral movement, the main reason for these modifications is likely to reduce the difficulty of lateral movement on the network.”
Once this step is successfully completed, victims are displayed a window showing that the deployment of the digital certificates is in progress, causing two root certificates to be installed on the machine using the certutil utility. Also dropped is a file called “wincert.js” that allows Mozilla Firefox to trust the root certificates.
To defend against Secret Blizzard activity, diplomatic entities operating in Moscow are urged to implement the principle of least privilege (PoLP), periodically review privileged groups, and route all traffic through an encrypted tunnel to a trusted network or use a virtual private network (VPN) service provider.