Table of Links
Abstract/Zusammenfassung
Publications
Acknowledgements
CHAPTER 1: INTRODUCTION
-
Introduction
1.1 Overview of thesis contributions
1.2 Thesis outline
CHAPTER 2: BACKGROUND
2.1 Blockchains & smart contracts
2.2 Transaction prioritization norms
2.3 Transaction prioritization and contention transparency
2.4 Decentralized governance
2.5 Blockchain Scalability with Layer 2.0 Solutions
CHAPTER 3. TRANSACTION PRIORITIZATION NORMS
-
Transaction Prioritization Norms
3.1 Methodology
3.2 Analyzing norm adherence
3.3 Investigating norm violations
3.4 Dark-fee transactions
3.5 Concluding remarks
CHAPTER 4. TRANSACTION PRIORITIZATION AND CONTENTION TRANSPARENCY
-
Transaction Prioritization and Contention Transparency
4.1 Methodology
4.2 On contention transparency
4.3 On prioritization transparency
4.4 Concluding remarks
CHAPTER 5. DECENTRALIZED GOVERNANCE
-
Decentralized Governance
5.1 Methodology
5.2 Attacks on governance
5.3 Compound’s governance
5.4 Concluding remarks
CHAPTER 6. RELATED WORK
6.1 Transaction prioritization norms
6.2 Transaction prioritization and contention transparency
6.3 Decentralized governance
CHAPTER 7. DISCUSSION, LIMITATIONS & FUTURE WORK
7.1 Transaction ordering
7.2 Transaction transparency
7.3 Voting power distribution to amend smart contracts
Conclusion
Appendices
APPENDIX A: Additional Analysis of Transactions Prioritization Norms
APPENDIX B: Additional analysis of transactions prioritization and contention transparency
APPENDIX C: Additional Analysis of Distribution of Voting Power
Bibliography
3.3 Investigating norm violations
Our analysis so far showed that while Bitcoin miners by and large follow transactionprioritization norms, there are many clear instances of norm violations. Our next goal is to develop a deeper understanding of the underlying reasons or motivations for miners to deviate from the fee rate based norms, at least for some subset of all transactions. To this end, we focus our investigation on the following three types of transactions, where we hypothesize miners might have an incentive to deviate from the current norms, which are well-aligned towards maximizing their rewards for mining.
-
Self-interest Transactions: Miners have a vested interest in a transaction, where the miners themselves are a party to the transaction, i.e., a sender or a receiver of bitcoins. Miners may have an incentive to selfishly accelerate the commitment of such transactions in the blocks mined by themselves.
-
Scam-payment Transactions: Bitcoins are increasingly being used to launch a variety of ransomware and scam attacks (Lee Mathews, 2017; Sheera Frenkel and Nathaniel Popper and Kate Conger and David E. Sanger, 2020; Sheera Frenkel, Mark Scott and Paul Mozur, 2017). A scam attack involved using hijacked Twitter accounts of celebrities to encourage their followers to send bitcoins to a specific Bitcoin wallet address (Sheera Frenkel and Nathaniel Popper and Kate Conger and David E. Sanger, 2020). Given the timely and widespread coverage of this attack in popular press and other similar attacks on crowdsourced websites for reporting scam transactions (BitcoinAbuse, 2021; Whale Alert, 2021), and with governments trying to blacklist wallet addresses of entities suspected of illegal activities (Andrew Hinkes and Joe Ciccolo, 2021; Nikhilesh De, 2021), we hypothesize that some miners might decelerate or even absolutely exclude the commitment of scam-payment transactions out of fear or ethical concerns.
-
Dark-fee Transactions: Recently, some mining pool operators have started offering transaction acceleration services (AntPool, 2022; BTC.com, 2022; F2Pool, 2022; Poolin, 2022; ViaBTC, 2022), where anyone wanting to prioritize their transactions can pay an additional fee to a specific mining pool via a side-channel (often, the MPO’s website or via a private-channel (Strehle and Ante, 2020)). Such transaction fees are “dark” or opaque to other mining pools and the public, and we hypothesize that some committed low-fee transactions might have been accelerated by using such services.
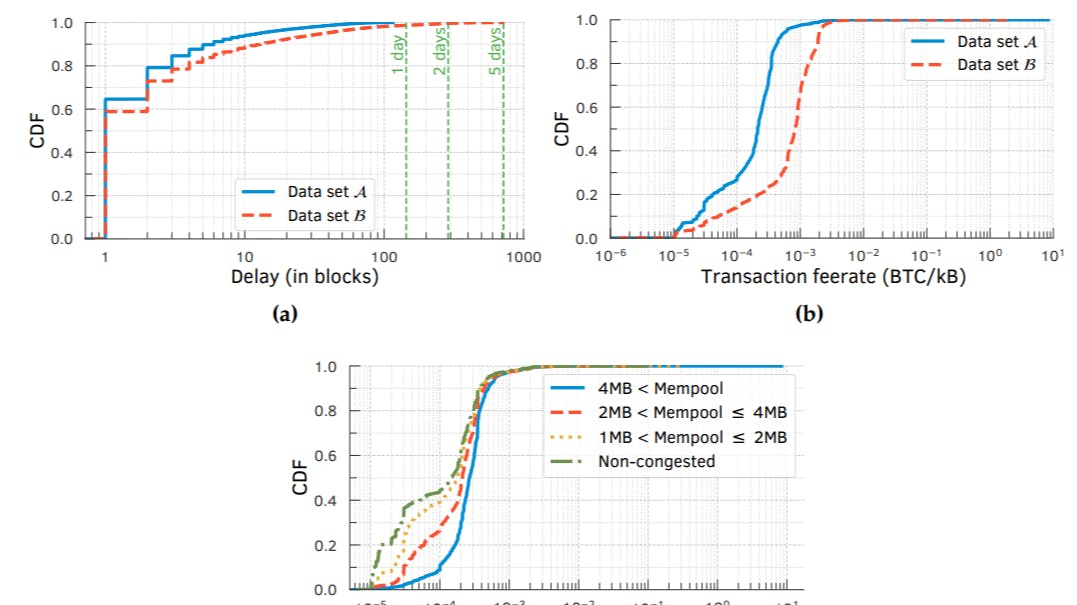
To detect whether a mining pool has accelerated or decelerated the above types of transactions, we first design a robust statistical test. , we report our findings from applying the test on the three types of transactions.
3.3.1 Statistical test for differential prioritization
Our goal here is to propose a robust statistical test for detecting whether a given mining pool m is prioritizing a given set of committed transactions c differently than all other miners. The basic idea behind the statistical test is as follows. Suppose a mining pool is accelerating (decelerating) transactions in set c. In that case, these transactions will have a disproportionately high (low) chance of being included in blocks mined by this mining pool compared to the mining pool’s hashing power (or rate).
Test for differential transaction acceleration
Test for differential transaction deceleration
While the previous test checks for prioritization (or acceleration), one may also want to test for deceleration. To that end, a symmetric test can be used. Specifically, with the previous notation, the test would be
Scaling the tests
3.3.2 Self-interest transactions
To identify transactions where a mining pool is a sender or receiver of transactions, we first need to identify Bitcoin wallets (addresses) that belong to mining pools. In Bitcoin, whenever a mining pool discovers a new block, it specifies a wallet address to receive the mining rewards. This mining pool address is included in the Coinbase transaction (refer §2.1) that appears at the start of every block. In our data set C, we gathered all the wallet addresses used by the top-20 mining pools to receive their rewards. For each mining pool, we then retrieved all committed transactions, in which coins were sent from the mining pool’s wallet. Figure 3.7 shows the statistics for the mining pool wallets and the transactions spending (sending) coins from (to) the wallets, for each of the top-20 mining pools in data set C. We found hundreds or thousands of self-interest transactions for most of the mining pools.
Acceleration of self-interest transactions
For self-interest transactions belonging to each of the top-20 mining pools, we separately applied our statistical test to check whether any of the top-10 mining pools (that mined at least 4% of all mined blocks in data set C) are preferentially accelerating or decelerating the transactions. In Table 3.2, we report the statistics from our test for mining pools that were found to preferentially treat transactions belonging to their own or other mining pools. Strikingly, Table 3.2 shows that 4 out of the top-10 mining pools namely, F2Pool, ViaBTC, 1THash & 58Coin, and SlushPool selfishly accelerated their own transactions, i.e., coin transfers from or to their own accounts (p-value for acceleration test is less
than 0.001). Equally, if not more interestingly, Table 3.2 shows collusive behavior among mining pools. Specifically, it shows that transactions issued by 1THash & 58Coin and SlushPool were collusively accelerated by ViaBTC (p-value for acceleration test is less than 0.001). That these mining pools were accelerating the transactions is further confirmed by the SPPE measure, which clearly shows that in each of the above cases, the self-interest transactions were also being included within the blocks ahead of other higher fee rate transactions.
3.3.3 Scam-payment transactions
Next, we investigate whether any mining pool attempted to decelerate or exclude scam-payment transactions.
On July 15, 2020, multiple celebrities’ accounts on Twitter fell prey to a scam attack. The scammers posted the message that anyone who transferred bitcoins to a specific wallet will receive twice the amount in return (Sheera Frenkel and Nathaniel Popper and Kate Conger and David E. Sanger, 2020). In response, several people sent, in total, 12.87051731 bitcoins—then worth nearly 142,000 (USD)—to the attacker’s wallet via 386 transactions, which were confirmed across 53 blocks by 12 miners.
To examine the miners’ behavior during this scam attack, we selected all blocks mined from July 14 to August 9, 2020 (i.e., 3697 blocks in total, containing 8,318,621 issued transactions as described in §A.6) from our data set C. Once again, we applied our statistical test to check whether any of the top-9 mining pools (that mined at least 5% of all mined blocks from this data) are preferentially accelerating or decelerating the transactions. Table 3.3 shows the test statistics. Interestingly, we find no statistically significant evidence (i.e., p-value less than 0.001) of scam-payment acceleration or deceleration across all top mining pools. Looking at SPPE measure across the mining pools, we find no evidence of mining pools (other than AntPool) preferentially ordering the scam-payment transactions within blocks. In short, our findings show that most mining pool operators today do not distinguish between normal and scam-payment transactions.
Inferring other scam payment transactions from crowded source data
We also want to investigate whether other types of scams payments have been recorded on the Bitcoin blockchain.
To conduct this experiment, we gathered data from the Bitcoin Abuse (Bitcoin Abuse, 2020) crowdsource platform. This platform allows users to report Bitcoin wallet addresses that they suspect are associated with scams. From May 16, 2017, to October 15, 2020, we gathered a total of 186,731 reports from users. These reports identified 54,032 unique wallet addresses that could potentially be linked to scams. The monthly trend of scam reports is illustrated in Figure 3.8a. Notably, there is an increase in the number of reports starting from July 2018. The reports predominantly originated from users in the US, followed by users in the UK (refer Figure 3.8b).
To simplify our analysis, we focused on transactions that occurred during the year 2018.1[0 ]However, out of the total reported wallets, only a small portion, 1169 (2.16%) wallets, were found in our Bitcoin 2018 data set. On average, each wallet address was reported 3.46 times, with a std. of 14.41. Both the minimum and the median number of reports for a wallet address were 1, while the maximum number of reports reached 950.
To ensure accuracy in our analysis, we complemented the data from Bitcoin Abuse with information from another platform called Scam Alert (Scam Alert, 2020). Scam Alert verifies the wallet addresses reported by users to determine if they are indeed associated with scams. Initially, we had a set of 1169 identified wallets reported by Bitcoin Abuse. Upon cross-checking with Scam Alert, we discovered that 100 were not involved with scams. Out of the remaining 1069 wallet addresses, 473 were confirmed to be scams, 79 were labeled as probable scams, and 517 were pending review at the time of our analysis. Thus, for our analysis, we only considered wallet addresses confirmed or labeled as probable scams by Scam Alert. This resulted in a final scam wallet data set containing 552 unique wallet addresses.
Table 3.4 provides information about the number of wallet addresses and the number of transactions that sent coins to at least one of the scam wallets during 2018. We identified several types of scams using the Scam Alert data set, with Sextortion comprising 40.79% of the total, followed by Terrorism at 16.79%, and Dark Web Shop at 15.65%. Together, these three types of scams accounted for 73.23% of the total scams identified in our study. Additionally, Table 3.5 shows the top-20 most frequently used wallet addresses for scam payments. Notably, the wallet 1LaN· · · Qctq has been associated with
a terrorist organization using it to collect donations (Huillet, 2020). This specific wallet address was involved in a total of by 1093 transactions.
Moreover, we observed that despite these scam wallets being publicly available, most of the mining pools still included them in their blocks. Figure 3.9 shows the distribution of blocks and transactions associated with scam payments that were included by each of the mining pools. BTC.com included alone 20.09% out of the 6511 scam transactions in 2018.
Author:
(1) Johnnatan Messias Peixoto Afonso
[10] Due to limitations in data gathering, we considered transactions issued in 2018. This forms a subset of our data set D introduced in §4.1.