Table of Links
Abstract and 1. Introduction
1.1 Background
1.2 Motivation
1.3 Our Work and Contributions and 1.4 Organization
-
Related Work
2.1 Mobile AIGC and Its QoE Modeling
2.2 Blockchain for Mobile Networks
-
Preliminaries
-
Prosecutor Design
4.1 Architecture Overview
4.2 Reputation Roll-up
4.3 Duplex Transfer Channel
-
OS2a: Objective Service Assessment for Mobile AIGC
5.1 Inspiration from DCM
5.2 Objective Quality of the Service Process
5.3 Subjective Experience of AIGC Outputs
-
OS2A on Prosecutor: Two-Phase Interaction for Mobile AIGC
6.1 MASP Selection by Reputation
6.2 Contract Theoretic Payment Scheme
-
Implementation and Evaluation
7.1 Implementation and Experimental Setup
7.2 Prosecutor Performance Evaluation
7.3 Investigation of Functional Goals
7.4 Security Analysis
-
Conclusion and References
7.3 Investigation of Functional Goals
The above experiments prove the architectural superiority of ProSecutor for adapting to mobile environments. Next, we test whether ProSecutor can achieve the aforementioned three functional design goals, using the proposed on-chain mechanisms (including OS2A framework, contract theoretic payment scheme, and duplex transfer channels).
7.3.1 Reputation-based MASP selection
In this part, we evaluate the effectiveness of the proposed OS2A framework for MASP selection. Recall that OS2A is measured by the MWSL-based reputation, allowing clients to express their subjective feelings via personalized models and standards. We model these clients using two strategies: forming explicit and implicit scenarios.
1) Explicit Scenario: As shown in Fig. 8-A(a), the explicit scenario contains four types of clients, which evaluate the AIGC images from Frechet inception distance (FID) [ ´ 12], but with different levels of strictness. The larger the number of indexes, the higher the requirement for FID. We further divide all the MASPs into four levels, with diverse abilities in terms of FID, also illustrated in Fig. 8-A(a). Then, we initialize such a mobile AIGC market, in which each client randomly selects the first MASP and then performs MASP selection following Algorithm 2. The average reputation of each type of MASP is depicted in Fig. 8-A(b). From this figure, we can observe that reputation is semantically meaningful since the reputation values of MASPs strictly align with their capability levels. Moreover, from the 120th round, we intentionally decrease the FID values of level1 and level-3 MASPs. Accordingly, their reputation values drop gradually due to the increasing proportion of negative opinions. Therefore, we can conclude that the reputation-based OS2AS can effectively reflect the performance and behaviors of the MASPs.
2) Implicit Scenario: To further simulate the practical mobile AIGC market, we consider the following implicit scenario. Specifically, we use ChatGPT (empowered by GPT4 model) to simulate the heterogeneous clients with diverse and latent QoE models. As shown in Fig. 8-A(c), given that ChatGPT cannot directly understand images, we evaluate each AIGC image from seven aspects. Then, we let ChatGPT act as four types of clients, each of which generates a customized model to fuse a subset of metrics and sets a personalized strictness level to determine whether the AIGC service experience is positive or negative. From Fig. 8-A(d), we can observe that the reputation values are meaningful even in such a complicated scenario. Moreover, the MASPs with higher capacity and providing customized services can gain higher reputations, even if the clients evaluate the AIGC services from different aspects and use diverse models. In contrast, the traditional modality-specific models [7] cannot accommodate these heterogeneous clients.
3) Ablation Study: Moreover, we conduct an ablation study to prove the effectiveness of the factors used for calibrating reference opinions. Firstly, Fig. 8-B(a) shows the reputation trend with all the factors. Then, we disable the Familiarity factor, in which case the attackers can launch the flooding attack [32]. To simulate it, we employ numerous clients to submit massive fake opinions, thereby increasing the reputation of the Level-2 MASPs. As shown in Fig. 8-B(b), Level-2 MASPs outperform Level-1 MASPs at the beginning. However, the flooding opinions usually have a small market worth; otherwise, they are easy to detect and mark, which may lead to token freezing. Therefore, after honest clients reach consistency on the Level-2 MASPs’ actual reputation, the effect of flooding opinions gradually drops because of the Market worth factor. Next, we disable
the Freshness factor. In this case, the system is vulnerable to long-range attacks [32], in which the attackers first forge several high-value opinions and thus gain great weight forever. As shown in Fig. 8-B(c), the reputation of Level-2 MASP exhibits a U-shape, with each uptick corresponding to a high-value opinion. Since no more such opinions after the 30th round, the increment stalls, while the effect caused by them can last for a long time. Finally, we disable the Market worth factor, in which case the attackers can launch dusting attacks by submitting massive opinions. As shown in Fig. 8-B(d), the reputation of Level-2 MASPs increases dramatically since massive high-value opinions are sent in the initial stage. Hence, the attackers can obtain the highest familiarity and freshness levels, thus tempering the reputation of the target MASPs.
7.3.2 Contract Theoretic Payment Scheme
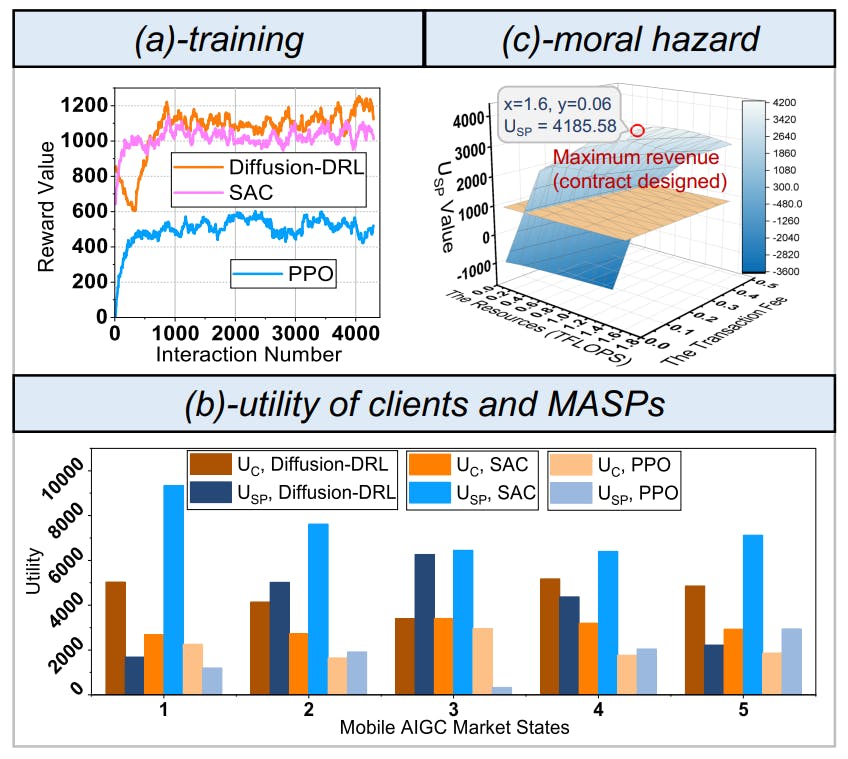
To optimize the contract design, we train the diffusionDRL model [7], whose training curve is shown in Fig. 9(a). Note that we use two conventional DRL methods, namely Proximal Policy Optimization (PPO) and Soft Actor-Critic (SAC), as the baselines. From Fig. 9(a), we can observe that the diffusion-DRL converges faster and achieves a higher reward. The reasons are two-fold: 1) the multiple-step diffusion keeps refining the model parameters to optimize the contract design, and 2) the long-term dependence in the complex mobile AIGC environments can be learned since the contract design is generated by steps rather than onetime in PPO and SAC. Using the well-trained model for inferences, Fig. 9(b) further shows the utility of clients by following the optimal contracts in different AIGC market states. We can observe that our method maintains the highest utility in all the tested situations, ensuring a stable revenue for the clients. Additionally, the IC and IR constraints are satisfied, ensuring that the MASPs are willing to sign the contracts. In contrast, PPO fails to reach the IR constraints in one state. Finally, Fig. 9(c) evaluates the defensive performance of our contract theoretic payment scheme against moral hazard. We can find that regardless of how the MASP changes the contract parameters, their utility decreases. Therefore, it will strictly follow the contract to maximize its utility, and the threats from the moral hazard can be circumvented.
7.3.3 Atomic Fee-Ownership Transfers
The atomicity of the fee-ownership transfer is protected by the smart contract, whose logic is presented in Fig. 10(a). We can observe that only if the current instruction is executed correctly, as well as the other side performs as promised, can the program proceed to the next step. If all the instructions are finished normally, the transfer succeeds. Otherwise, the roll-back will be triggered without any immediate states. The transfer contract is deployed on the anchor chain and instantiated by the transfer channels. All the operations (e.g., instruction fetches and executions) are automatically
conducted when the pre-defined conditions are met, which guarantees that malicious attackers cannot manipulate the transfer process.
Although unable to tamper with the smart contracts, dishonest participants might disturb the normal contract execution by intentionally delaying the instruction executions. For instance, in Fig. 10(a), if the client continuously submits fake signatures of its updated balance in Step 4, not only its Step 5 but also Step 4 of the MASP will be affected. The atomicity and latency of transfers are shown in Fig. 10(b), where Probability of Delay represents the probability that one instruction execution is delayed. We can observe that the transfer atomicity level maintains at 100% due to the protocol logic and the features of the smart contract. However, the latency continues to increase, adversely affecting the system performance and the user experience. To defend the intentional delay, in practice, we can assign each instruction execution a timer whose value is customized during the channel establishment. If one instruction fails to be completed within the pre-defined time, the rollback operation will be triggered. Furthermore, the clients and MASPs can configure the timer according to specific tasks and scenarios (e.g., the time sensitivity of the service and the trustworthiness between the two parties).
7.4 Security Analysis
TABLE 2 summarizes the defenses of ProSecutor against potential security issues. Firstly, the attacks aiming to destroy ProSecutor in terms of the consistency, identity, and liveness [39] can be effectively defended by DPoS, SHA256- based cryptography scheme, and transaction fee scheme, respectively. Since these defenses are theoretically proven [32], [33], we omit the detailed explanations. Secondly, during the opinion collection and reputation calculation, the attackers can adopt diverse ways to tamper with the values. Leveraging MWSL [16], we calibrate the reputation by Familiarity, Freshness, and Market worth factors, which are proven to defend flooding, long-range, and dusting attacks effectively. Furthermore, the contract theoretic payment scheme and duplex transfer channels are proven to defend the moral hazard and repudiation, respectively.
Authors:
(1) Yinqiu Liu, School of Computer Science and Engineering, Nanyang Technological University, Singapore ([email protected]);
(2) Hongyang Du, School of Computer Science and Engineering, Nanyang Technological University, Singapore ([email protected]);
(3) Dusit Niyato, School of Computer Science and Engineering, Nanyang Technological University, Singapore ([email protected]);
(4) Jiawen Kang, School of Automation, Guangdong University of Technology, China ([email protected]);
(5) Zehui Xiong, Pillar of Information Systems Technology and Design, Singapore University of Technology and Design, Singapore ([email protected]);
(6) Abbas Jamalipour, School of Electrical and Information Engineering, University of Sydney, Australia ([email protected]);
(7) Xuemin (Sherman) Shen, Department of Electrical and Computer Engineering, University of Waterloo, Canada ([email protected]).

![Fig. 8: The inspection of MWSL-based reputation scheme for MASP selection. FID, SI, CLIP, and BRISQUE are general image quality assessment KPIs [12]. The images with different KPI scores can be generated by first generating an original image and then adding noise/blur.](https://hackernoon.imgix.net/images/fWZa4tUiBGemnqQfBGgCPf9594N2-1x032sl.png?auto=format&fit=max&w=3840)