How are you, hacker?
🪐Want to know what’s trending right now?:
The Techbeat by HackerNoon has got you covered with fresh content from our trending stories of the day! Set email preference here.
## ISO 27001 Compliance Tools in 2026: A Comparative Overview of 7 Leading Platforms
By @stevebeyatte [ 7 Min read ]
Breaking down the best ISO 27001 Compliance tools in the market for 2026. Read More.
The Hidden Cost of AI: Why It’s Making Workers Smarter, but Organisations Dumber 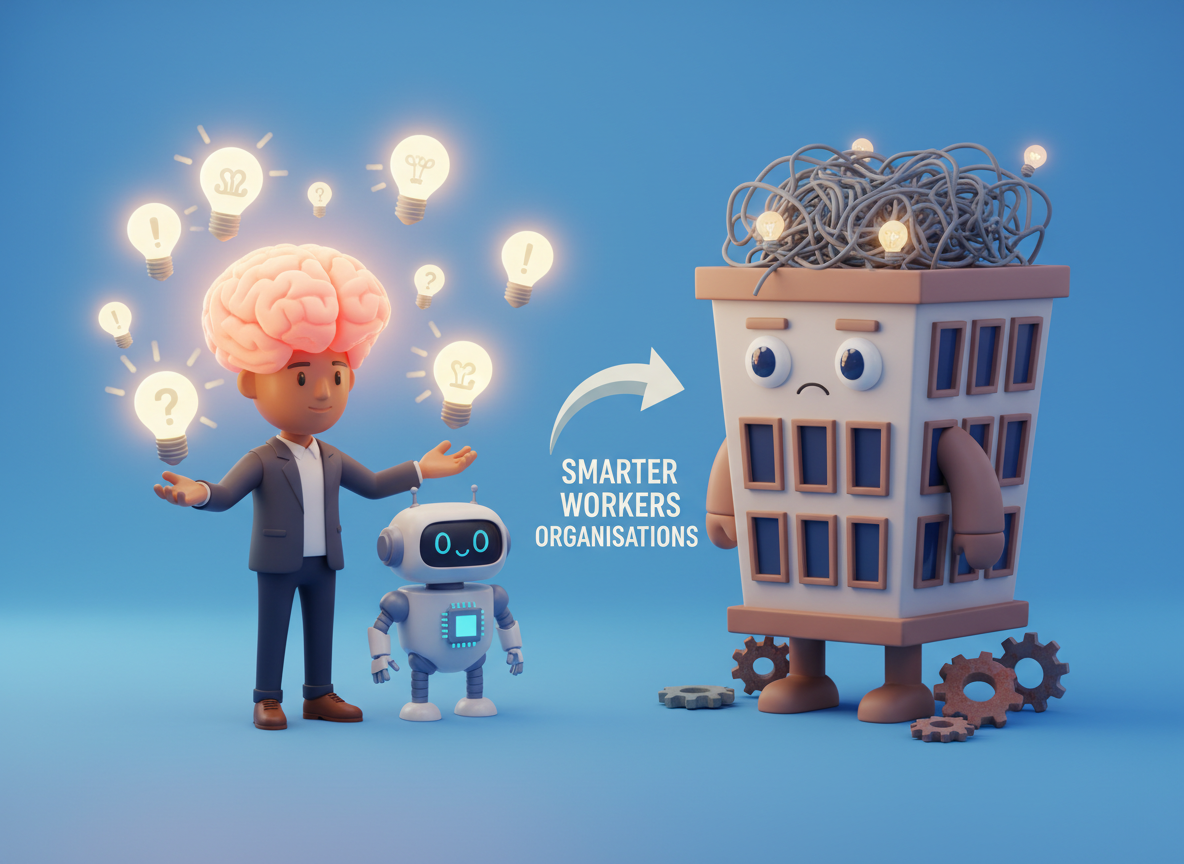
By @yuliiaharkusha [ 8 Min read ]
AI boosts individual performance but weakens organisational thinking. Why smarter workers and faster tools can leave companies less intelligent than before. Read More.
A Developer’s Guide to Building Next-Gen Smart Wallets With ERC-4337 — Part 2: Bundlers 
By @hacker39947670 [ 15 Min read ]
Bundlers are the bridge between account abstraction and the execution layer. Read More.
IPv6 and CTV: The Measurement Challenge From the Fastest-Growing Ad Channel 
By @ipinfo [ 7 Min read ]
IPv6 breaks digital ad measurement. Learn how IPinfo’s research-driven, active-measurement model restores accuracy across CTV and all channels. Read More.
Should We Be Worried About Losing Jobs? Or Just Adapt Our Civilization to New Reality? 
By @chris127 [ 10 Min read ]
The question isn’t whether jobs will disappear—it’s whether our traditional work model is still valid. Read More.
How Crypto Can Protect People from Currency Wars 
By @chris127 [ 8 Min read ]
When we think of war, we imagine soldiers, weapons, and physical destruction. But there’s another type of war that affects millions of people worldwide… Read More.
The Realistic Guide to Mastering AI Agents in 2026 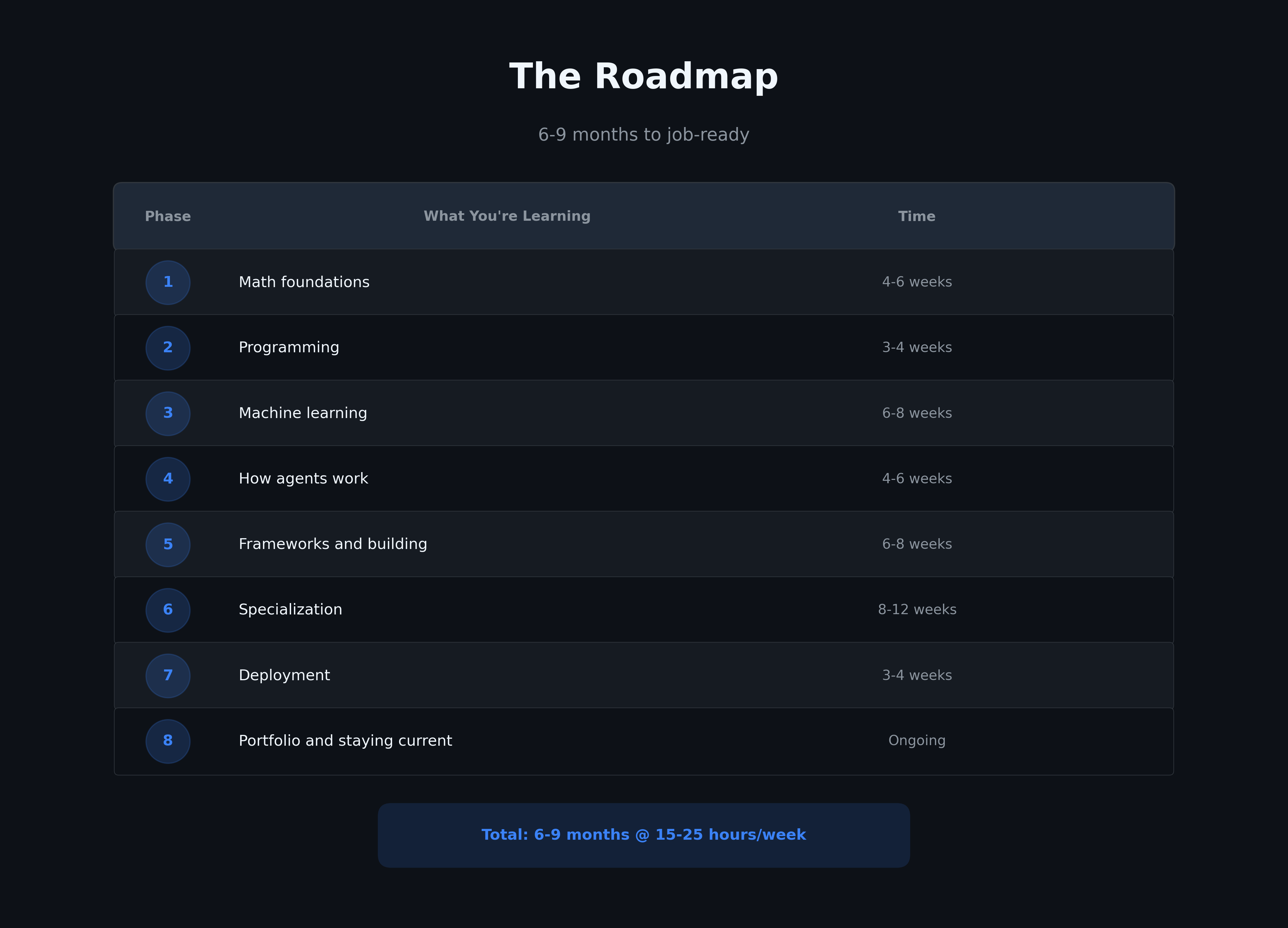
By @paoloap [ 12 Min read ]
Master AI agents in 6-9 months with this complete learning roadmap. From math foundations to deploying production systems, get every resource you need. Read More.
Cursor’s Graphite Deal Aims to Close the Loop From Writing Code to Merging It 
By @ainativedev [ 3 Min read ]
Cursor’s acquisition of Graphite aims to unify code creation and review, and in the process brings the company closer to territory long dominated by GitHub. Read More.
Should You Trust Your VPN Location? 
By @ipinfo [ 9 Min read ]
IPinfo reveals how most VPNs misrepresent locations and why real IP geolocation requires active measurement, not claims. Read More.
Prompt Chaining: Turn One Prompt Into a Reliable LLM Workflow 
By @superorange0707 [ 7 Min read ]
Prompt Chaining links prompts into workflows—linear, branching, looping—so LLM outputs are structured, debuggable, and production-ready. Read More.
Can ChatGPT Outperform the Market? Week 23 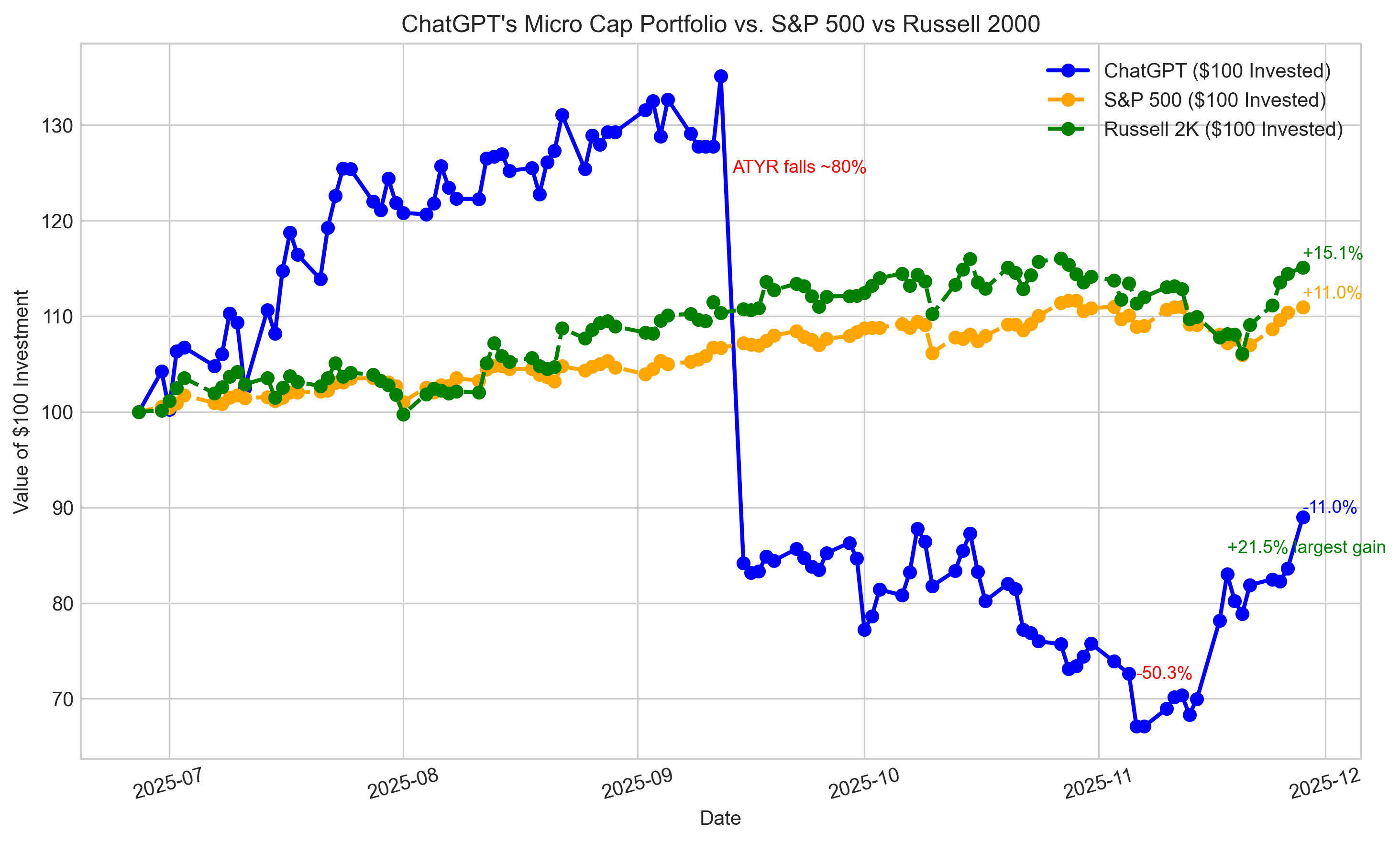
By @nathanbsmith729 [ 4 Min read ]
Another strong week… Read More.
What Comes After Growth Hacks: AI-Driven Marketing Systems 
By @khamisihamisi [ 3 Min read ]
What comes after growth hacks isn’t more hustle. Its systems and those systems are powered by AI. Read More.
Meet ScyllaDB: HackerNoon Company of the Week 
By @companyoftheweek [ 4 Min read ]
Meet ScyllaDB, the high-performance NoSQL database delivering predictable millisecond latencies for Discord and hundreds more. Read More.
Why Ledger’s Latest Data Breach Exposes the Hidden Risks of Third-Party Dependencies 
By @ishanpandey [ 3 Min read ]
Ledger data breach via Global-e exposes customer info. No crypto stolen, but phishing attempts surge. Third-party risks examined. Read More.
The Next Big Thing Isn’t on Your Phone. It’s AI-Powered XR and It’s Already Taking Over. Part II 
By @romanaxelrod [ 7 Min read ]
AI-powered XR won’t be won by smart glasses alone. Why Big Tech is stuck optimizing and how deep tech, AI-driven R&D, and new materials are reshaping computing Read More.
Code Smell 12 – Null is Schizophrenic and Does Not Exist in The Real-world 
By @mcsee [ 5 Min read ]
Programmers use Null as different flags. It can hint at an absence, an undefined value, en error etc. Multiple semantics lead to coupling and defects. Read More.
5 Gen Z Marketing Trends That Will Make or Break Brands in 2026 
By @lomitpatel [ 4 Min read ]
Discover 5 Gen Z marketing trends for 2026. Learn how brands can build community, use AI transparently, and engage Gen Z with culture and authenticity. Read More.
Write Symfony Commands Like You Write Controllers—Finally 
By @mattleads [ 12 Min read ]
Symfony 7.4 makes Console commands expressive and type-safe. Read More.
I Saw a Phishing Site That Traps Security Bots 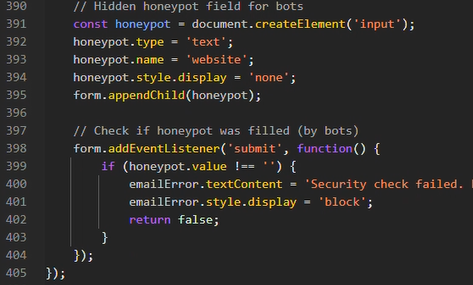
By @behindthesurface [ 5 Min read ]
How modern phishing kits use honeypots, cloaking, and adversary-in-the-middle attacks—and how defenders can turn those same tactics against them. Read More.
Anyone Can Be a Victim to a Phishing Scam. Here’s My Story. 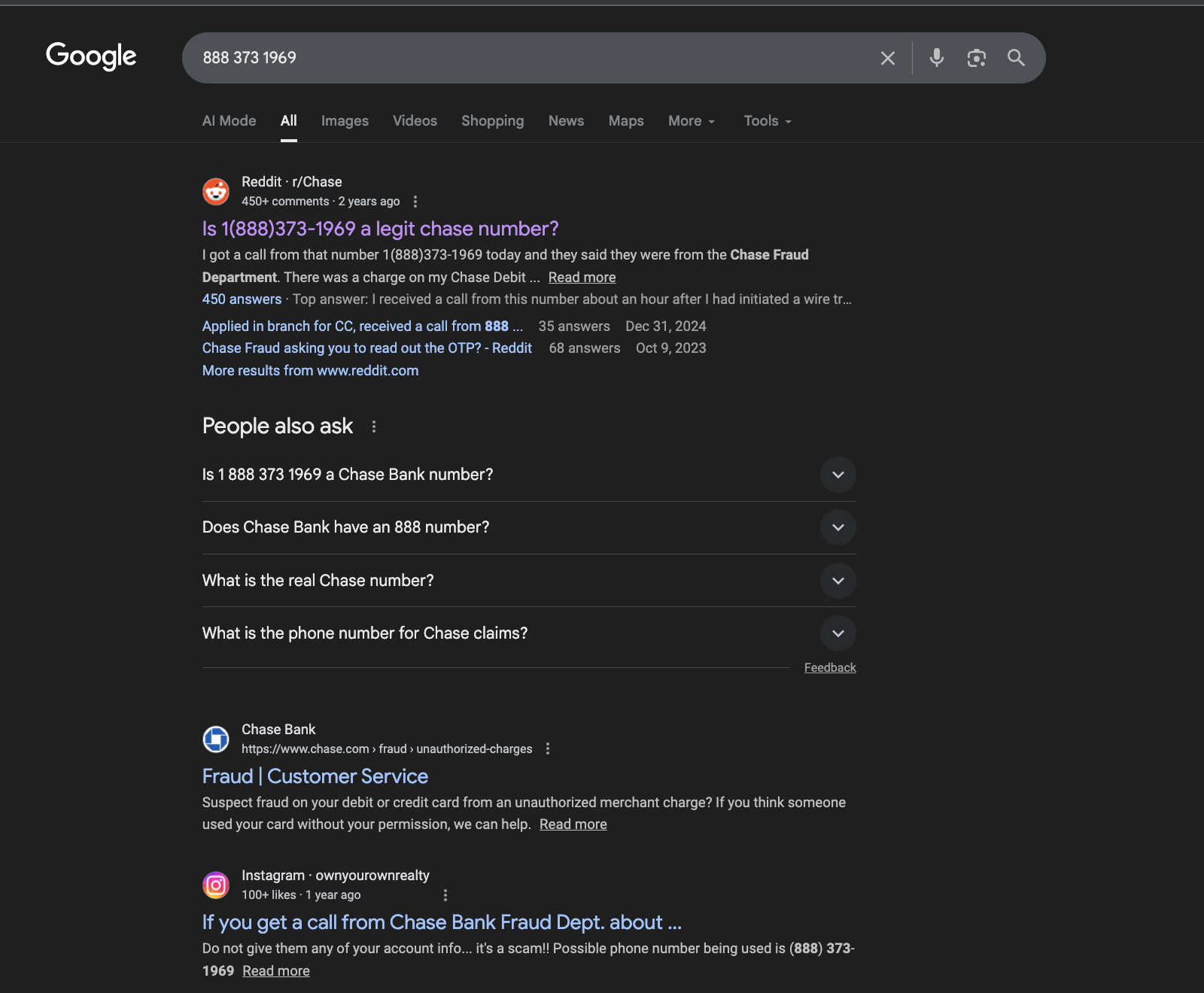
By @linh [ 5 Min read ]
Got a call from 888-373-1969 claiming to be the Chase fraud department? Trust but verify should be your principle to avoid phishing scam! Read More.
🧑💻 What happened in your world this week? It’s been said that writing can help consolidate technical knowledge, establish credibility, and contribute to emerging community standards. Feeling stuck? We got you covered ⬇️⬇️⬇️
ANSWER THESE GREATEST INTERVIEW QUESTIONS OF ALL TIME
We hope you enjoy this worth of free reading material. Feel free to forward this email to a nerdy friend who’ll love you for it.
See you on Planet Internet! With love,
The HackerNoon Team ✌️
.gif)











