Popular messaging app WhatsApp on Tuesday unveiled a new technology called Private Processing to enable artificial intelligence (AI) capabilities in a privacy-preserving manner.
“Private Processing will allow users to leverage powerful optional AI features – like summarizing unread messages or editing help – while preserving WhatsApp’s core privacy promise,” the Meta-owned service said in a statement shared with The Hacker News.
With the introduction of the latest feature, the idea is to facilitate the use of AI features while still keeping users’ messages private. It’s expected to be made available in the coming weeks.
The capability, in a nutshell, allows users to initiate a request to process messages using AI within a secure environment called the confidential virtual machine (CVM) such that no other party, including Meta and WhatsApp, can access them.

Confidential processing is one of the three tenets that underpin the feature, the others being –
- Enforceable guarantees, which cause the system to fail or become publicly discoverable when attempts to modify confidential processing guarantees are detected
- Verifiable transparency, which allows users and independent researchers to audit the behavior of the system
- Non-targetability, which prevents a particular user from being targeted without breaching the whole security architecture
- Stateless processing and forward security, which ensures that messages are not retained once the messages are processed so that an attacker cannot recover historical requests or responses
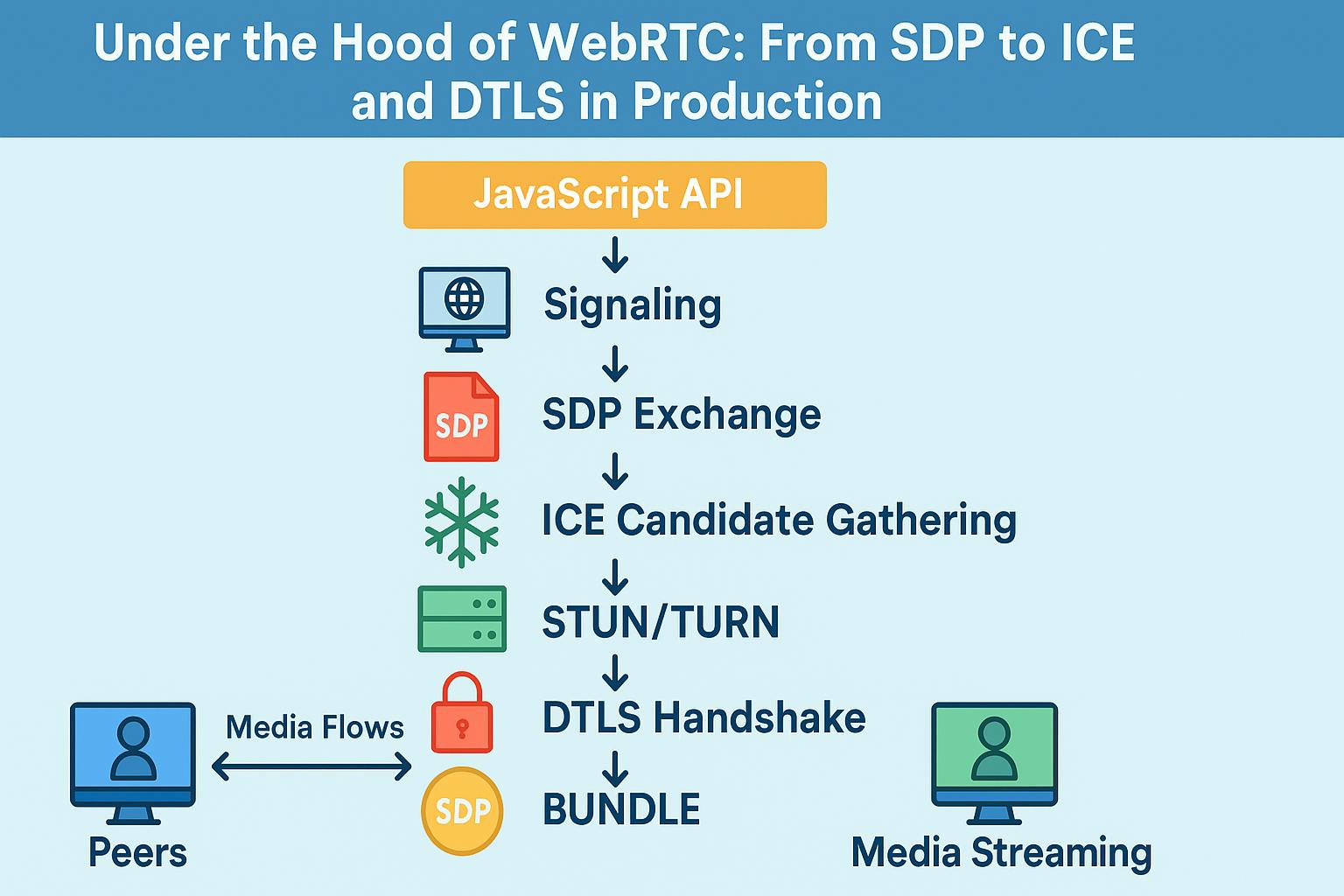
The system is designed as follows: Private Processing obtains anonymous credentials to verify that future requests are coming from a legitimate WhatsApp client and then proceeds to establish an Oblivious HTTP (OHTTP) connection between the user’s device and a Meta gateway via a third-party relay that also hides the source IP address from Meta and WhatsApp.
A secure application session is subsequently established between the user’s device and the Trusted Execution Environment (TEE), following which an encrypted request is made to the Private Processing system using an ephemeral key.
This also means that the request cannot be decrypted by anyone other than the TEE or the user’s device from which the request (e.g., message summarization) is sent.
The data is processed in CVM and the results are sent back to the user’s device in an encrypted format using a key that’s accessible only on the device and the Private Processing server.
Meta has also acknowledged the weak links in the system that could expose it to potential attacks via compromised insiders, supply chain risks, and malicious end users, but emphasised it has adopted a defense-in-depth approach to minimize the attack surface.

Furthermore, the company has pledged to publish a third-party log of CVM binary digests and CVM binary images to help external researchers “analyze, replicate, and report instances where they believe logs could leak user data.”
The development comes as Meta released a dedicated Meta AI app built with Llama 4 that comes with a “social” Discover feed to share and explore prompts and even remix them.
Private Processing, in some ways, mirrors Apple’s approach to confidential AI processing called Private Cloud Compute (PCC), which also routes PCC requests through an OHTTP relay and processes them in a sandboxed environment.
Late last year, the iPhone maker publicly made available its PCC Virtual Research Environment (VRE) to allow the research community to inspect and verify the privacy and security guarantees of the system.