Your Internet Service Provider (ISP) is the first hop between you and the internet. Each time you connect, you pass information to your ISP, including domain names, IP addresses, connection timestamps, and any unencrypted HTTP traffic. While this is mostly fine, if you’re like me, you’ll probably want a bit more security and privacy for your online activities.
Now, most folks think that using a good VPN service is the only way to protect their online privacy. However, there is another solution: a local DNS.
The Domain Name System (DNS) essentially translates human-readable website addresses into computer-readable IP addresses, making it vital for navigating the internet. By default, it’s not encrypted, meaning ISPs and other services can see your requests. But the good news is that you can make your own private, local DNS in an afternoon, and I’m going to show you how.
Local DNS vs. ISP snooping
Your connection and logs in your hands
A chain of events occurs when you type a website’s address (URL) into your browser. The first step is a DNS server query to translate the name you typed into an IP address. This request is typically sent in plain text, and the ISP is usually the party responding unless you have a hardened configuration, such as DNS-over-HTTPS or DNS-over-TLS. This means that your ISP maintains a log of the websites you’ve visited.
Now, DNS is very revealing because of its simplicity. Cookies and trackers may be blocked depending on the browser you use, but this isn’t the case with DNS requests. If you visit Facebook or log into your bank, regardless of the device you use, and even if you use incognito browsing, your ISP typically sees the DNS lookup for the domain you’re visiting. Over time, this metadata may create a profile of your routines and interests, including your work hours, medical interests, hobbies, and more.
However, privacy is just one of the concerns associated with DNS. In certain markets, failed DNS lookups can be redirected to ad-filled pages, or worse, malware. In other cases, policy requirements may be enough to block certain domains. So, DNS snooping is much more than a privacy concern for the everyday person.
Take control of your DNS with a local configuration
A new flexible layer of control
DNS is one of the services most people outsource by default. Most folks use their ISP’s default DNS settings, or alternatively switch to a third-party DNS provider like Google or Cloudflare. The only issue is that these third parties may be able to see your requests.
However, one of the most effective ways to change this dynamic is by running a local DNS. This way, a small DNS service running on your own machine becomes your trusted resolver.
A resolver receives requests for a website and finds its matching IP address. This process is typically handled by the ISP’s resolver, but if you’re setting up a local DNS, you have control.
This shift in autonomy puts you in a position to decide how your requests are processed. You can either resolve them yourself by querying authoritative servers directly or forward them to a trusted resolver. However, requests that leave your computer will be unencrypted and still visible to the ISP or upstream resolver if your local DNS setup doesn’t use DNS-over-HTTPS (DoH) or DNS-over-TLS (DoT). You don’t have full privacy without an encrypted DNS protocol; you only gain control over caching, filtering, and which upstream service you trust.
This is a powerful type of control that allows you to apply caching and custom rules to block specific sites from your kids’ devices or gain faster access to the domains you visit regularly. You may even add a hosts file that blocks known trackers.
DNS vs. VPN
They protect different parts of your internet connection
You may easily confuse what a local DNS achieves with what a VPN does, but they address different problems.
A VPN will encrypt your entire internet traffic, including DNS lookups. It also routes your traffic through a secure tunnel. When you use a VPN, a few things are achieved: you hide your IP address, block your ISP from seeing your activity, and also mask your identity from the websites you visit.
The role of a local DNS is limited primarily to how lookups are resolved. It does not hide your activity from network observers or your ISP, and it does not provide encryption or anonymity. So, while a VPN offers privacy and identity protection, a local DNS provides flexibility and control; they may both be complementary services. Even with encrypted DNS, other metadata, such as Server Name Indication (SNI) in TLS handshakes, can leak visited domains to sophisticated network observers.
Misconfigured local DNS settings are a privacy risk. They can bypass your VPN tunnel and cause DNS leaks that expose your queries to your ISP.
How I created a local DNS in an afternoon
A free local DNS on Windows 11
When I decided to set up my DNS server, what I was looking for was something practical and free. So, no Raspberry Pi and no subscriptions—just something that would work on Windows 11. Here’s exactly what I did:
- I downloaded Acrylic DNS Proxy from the Mayakron website, then installed it using the default option. Acrylic is ideal because it’s free and lightweight, and it doesn’t need a complex configuration. However, please note that Acrylic itself doesn’t encrypt your DNS traffic—it simply forwards your requests. For encryption, you’ll need a resolver or tool that supports DNS-over-HTTPS (DoH) or DNS-over-TLS (DoT).
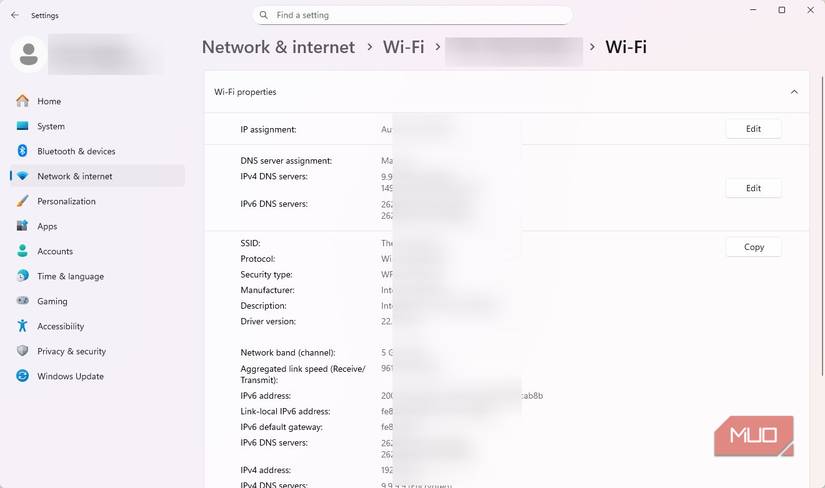
- Then, I opened the Control Panel network connections settings. Here, I right-clicked on my active connection (Wi-Fi or Ethernet) and chose Properties.
- I selected Internet Protocol Version 4 (TCP/IPv4) and clicked Properties. Then, I selected Use the following DNS server addresses and set my Preferred DNS server to 127.0.0.1. This way, Windows will always send DNS lookups to Acrylic running locally.
-
I then set Quad9 as the upstream resolver to which Acrylic forwards requests by launching Acrylic, clicking File, then Open Acrylic Configuration, and setting the parameters below to the following values:
- Primary Server Address: 9.9.9.9
- Primary Server Port: 53
- Secondary Server Address: 149.112.112.112
- Secondary Server Port: 53
Quad9 is an ideal upstream resolver because it actively blocks some known malicious domains, but you’ll need to add a free hosts file or filter lists to Acrylic to stop known ad/tracker domains. Of course, you can also use any other DNS server that prioritizes online safety.
This setup makes a real difference. My cached DNS queries were answered locally, which sped up the time it takes to resolve domain names, especially on slow internet connections, because cached DNS lookups bypass the initial hiccup. You may also choose to add a free hosts file that blocks domains known to be used by ad trackers, so intrusive requests don’t make it as far as my browser.
I recommend a local DNS
I’ve tried a few different DNS experiments, with varying levels of success. Some are too technical, and some are too time-consuming for the return. However, setting up a local DNS is different. It gives you control, filtering, and some speed benefits—but it won’t stop your ISP from seeing the IP addresses you’re connecting to. To do that, you’ll need to pair your local configuration with an encrypted DNS, or you could use one of our recommended VPN services to protect your whole connection.