New findings this week showed that a misconfigured platform used by the Department of Homeland Security left sensitive national security information—including data related to the surveillance of Americans—exposed and accessible to thousands of people. Meanwhile, 15 New York officials were arrested by Immigration and Customs Enforcement and the New York Police Department this week in or around 26 Federal Plaza—where ICE detains people in what courts have ruled are unsanitary conditions.
Russia conducted conspicuous military exercises testing hypersonic missiles near NATO borders, stoking tensions in the region after the Kremlin had already recently flown drones into Polish and Romanian airspace. Scammers have a new tool for sending spam texts, known as “SMS blasters,” that can send up to 100,000 texts per hour while evading telecom company anti-spam measures. Scammers deploy rogues cell towers that trick people’s phones into connecting to the malicious devices so they can send the texts directly and bypass filters. And a pair of flaws in Microsoft’s Entra ID identity and access management system, which have been patched, could have been exploited to access virtually all Azure customer accounts—a potentially catastrophic disaster.
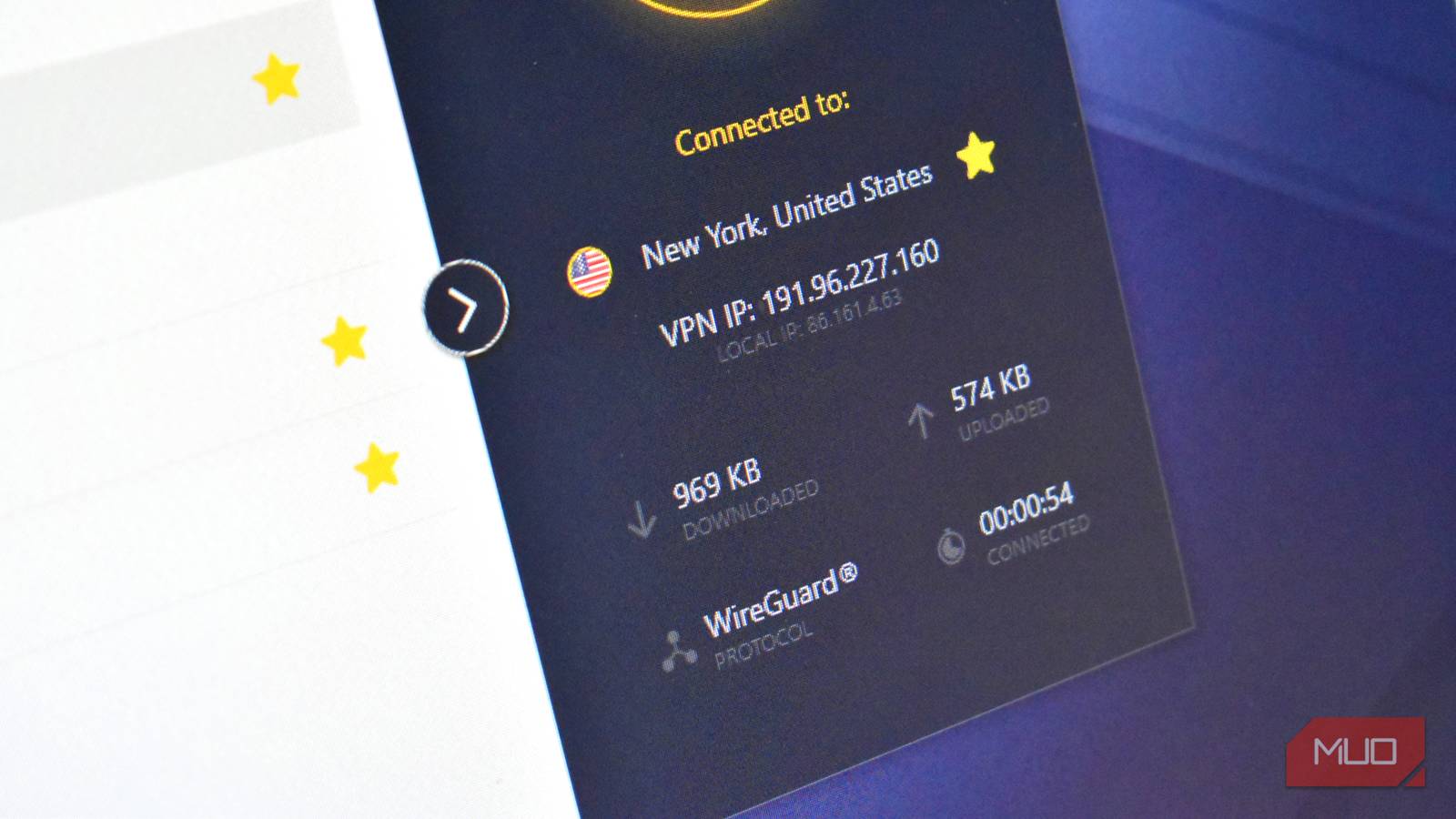
WIRED published a detailed guide this week to acquiring and using a burner phone, as well as alternatives that are more private than a regular phone but not as labor-intensive as a true burner. And we updated our guide to the best VPNs
But wait, there’s more! Each week, we round up the security and privacy news we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
The cybersecurity world has seen, to its growing dismay, plenty of software supply chain attacks, in which hackers hide their code in a legitimate piece of software so that it’s silently seeded out to every system that uses that code around the world. In recent years, hackers have even tried linking one software supply chain attack to another, finding a second software developer target among their victims to compromise yet another piece of software and launch a new round of infections. This week saw a new and troubling evolution of those tactics: A full-blown self-replicating supply chain attack worm.
The malware, which has been dubbed Shai-Hulud after the Fremen name for the monstrous Sandworms in the sci-fi novel Dune (and the name of the Github page where the malware published stolen credentials of its victims) has compromised hundreds of open-source software packages on the code repository Node Packet Management, or NPM, used by developers of Javascript. The Shai-Hulud worm is designed to infect a system that uses one of those software packages, then hunt for more NPM credentials on that system so that it can corrupt another software package and continue its spread.
By one count, the worm has spread to more than 180 software packages, including 25 used by the cybersecurity firm CrowdStrike, though CrowdStrike has since had them removed from the NPM repository. Another count from cybersecurity firm ReversingLabs put the count far higher, at more than 700 affected code packages. That makes Shai-Hulud one of the biggest supply chain attacks in history, though the intent of its mass credential-stealing remains far from clear.
Western privacy advocates have long pointed to China’s surveillance systems as the potential dystopia awaiting countries like the United States if tech industry and government data collection goes unchecked. But a sprawling Associated Press investigation highlights how China’s surveillance systems have reportedly been largely built on US technologies. The AP’s reporters found evidence that China’s surveillance network—from the “Golden Shield” policing system that Beijing officials have used to censor the internet and crack down on alleged terrorists to the tools used to target, track and often detain Uyghurs and the country’s Xinjiang region—appear to have been built with the help of American companies, including IBM, Dell, Cisco, Intel, Nvidia, Oracle, Microsoft, Thermo Fisher, Motorola, Amazon Web Services, Western Digital, and HP. In many cases, the AP found Chinese-language marketing materials in which the Western companies specifically offering surveillance applications and tools to Chinese police and domestic intelligence services.
Scattered Spider, a rare hacking and extortion cybercriminal gang based largely in Western countries, has for years unleashed a trail of chaos across the internet, hitting targets from MGM Resorts and Caesar’s Palace to the Marks & Spencer grocery chain in the United Kingdom. Now two alleged members of that notorious group have been arrested in the UK: 19-year-old Thalha Jubair and 18-year-old Owen Flowers, both charged with hacking the Transport for London transit system—reportedly inflicting more than $50 million in damage—among many other targets. Jubair alone is accused of intrusions targeting 47 organizations. The arrests are just the latest in a string of busts targeting Scattered Spider, which has nonetheless continued a nearly uninterrupted string of breaches. Noah Urban, who was convicted on charges related to Scattered Spider activity, spoke from jail to Bloomberg Businessweek for a long profile of his cybercriminal career. Urban, 21, has been sentenced to a decade in prison.