If you think scam emails are all poorly-worded messages asking you to help a faraway prince transfer millions of dollars out of his country, you need to be aware of today’s much trickier phishing attempts.
3
“Hello, Pervert” Blackmail
This scam email has been around for years, but it continues to trick people; there are always questions about it on Reddit and similar sites. You receive an email that looks like it came from your own address. It explains that the sender was able to install a spyware program on your computer that gives them complete access to everything you do on your machine, including your contacts and webcam.
They then state that they have compromising video of you watching explicit content online, and threaten to send the videos to all your contacts if you don’t send them cryptocurrency. The message includes threatening language that you only have 24 or 48 hours to send the money, and that if you try to reset your device or go to the police, they’ll release the video immediately.
Over the years, this scam has evolved to sometimes include more personal details, which lends more credibility to what the scammer says. The message might have your home address, a photo of your house on Google Maps, or a password you’ve used in the past.
In reality, this is all a sham. The sender doesn’t have access to your email account; they use email spoofing to make it look like the message came from you. They use broad language in the email in hopes that they can get an emotional reaction from as many people as possible. If they truly had video or your contacts list, they would share a sample so you knew it was real.
When they include an old password, it’s from a data breach that anyone can look up, not something they got from hacking you. It’s the same with home addresses; this data is unfortunately dumped publicly after security breaches, which anyone can then look up and screenshot on Google Maps.
If you still use the compromised password anywhere, update it. Otherwise, you should ignore this email.
2
Fake Purchase Emails
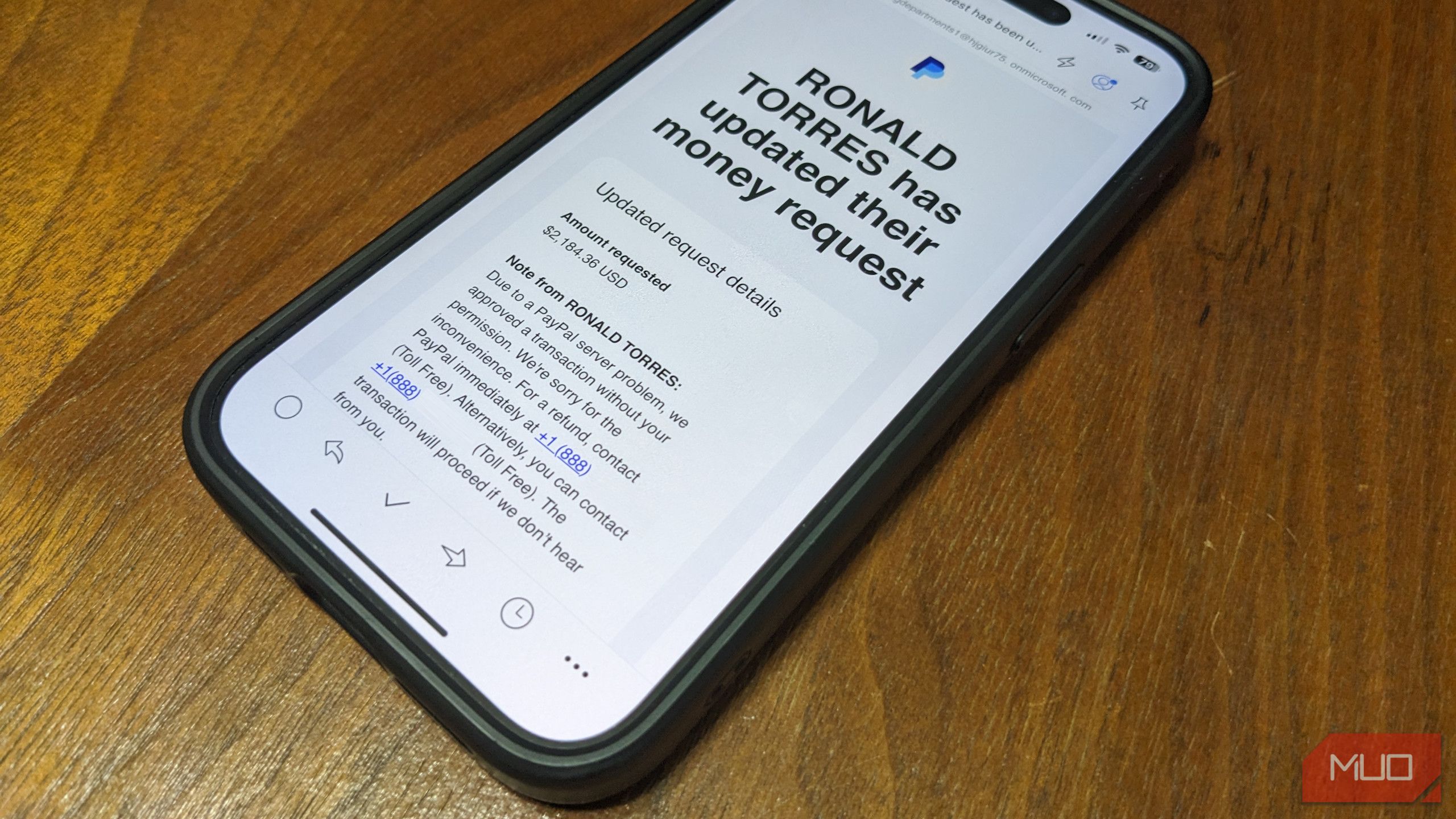
Another common email scam that’s designed to trick as many people as possible is the fake receipt. Sometimes, these pretend to be from a PC security tool like Norton or McAfee. Past versions of this scam sometimes forged a Geek Squad email, and I’ve also seen them faked in the style of big retailers like Amazon to claim you purchased a MacBook or other expensive item.
Regardless of the fake sender, the formula is the same: a receipt for an expensive purchase that you didn’t make, along with a phone number to call if the purchase was “unauthorized”. They hope most people will panic and call immediately to cancel the purchase, with that number leading you to the fraudsters.
If you call them, they’ll want to take your credit card number, or more likely, it will proceed like a tech support scam. They’ll ask to connect to your PC and show you made-up “problems” before asking for payment.
Looking closely, you’ll see the signs of these emails being fake. Even if the formatting and grammar are clear and correct (which they rarely are for scam emails), they won’t have specific details about the card you used to “purchase” the item, the ZIP code for delivery, or similar. Almost every legitimate purchase receipt email will have this information.
While scammers can create fake PayPal emails for this scheme, they can also abuse PayPal’s systems to send real invoices for made-up purchases. Any PayPal user can send other people invoices as desired; this doesn’t mean you have to pay them. Similar to the above, these will include a note with a fake phone number to contact. This is the point of the scam—they don’t expect you to pay the invoice.
You should ignore any purchase emails for items you don’t remember buying. If you can’t recall, check your credit card transactions; any purchase that doesn’t show up there is not real and was made up for a scam. You should never call phone numbers provided in an email. It’s always the best option to check a company’s official site for support contact info.
1
AI Levels Up Email Scams
AI’s many powers enable scammers to create more email attacks that are more sophisticated and better targeted—plus they can generate them faster.
One illustrative example is “lost pet” scams, where people use the contact info shared on “lost pet” posters and listings to pretend they have someone’s animal and extort money from them. With AI image generation being even more impressive now, if you have your email address in the listing, someone could take advantage of this. Using reference photos from your listing, they could generate AI photos of your pet, then run the same scam by pretending they found the animal.
AI image generation can also be used to create more realistic fake images for romance scams, celebrity impersonation scams (which often target the elderly), or even to impersonate your friends. Never trust something that was sent to you randomly; always contact the person through a known method to verify.
Thanks to AI, it’s also easier for scammers to proofread their emails, fixing the common hallmarks of poor English that mark scam emails. You can no longer trust an email simply because it contains no spelling mistakes.
AI can also find a lot of information about people in record time. If you have even a moderate online presence, AI can summarize that info for a scammer, which gives them more ideas on how to fool you. They can pretend to have met you at an event you attended, give you specific details about your past work that they’re a “fan” of, or similar. Or they could find out where you work and craft a phishing email claiming to be a job satisfaction survey from HR, for example.
Many of the top scam threats in 2025 rely on AI. Knowing how to spot AI video and other AI-generated content is becoming more important all the time.
Even as they evolve, the majority of scam emails still rely on the same principles. They’re overly generic to target as many people as possible, and they use emotional triggers to make you act quickly without thinking.
When something seems off, always take a moment to calm yourself and think logically. Scam emails might be getting smart, but you can still outsmart them.