July 30, 2025
To secure reprogrammable chips, the US must address supply chain risks
Table of Contents
1. Executive summary
Field-programmable gate arrays (FPGAs) are specialized computer chips critical to the US economy and national security. FPGAs are vital components in American military systems like the Javelin anti-tank missile and F-35 fighter jet, American-built automobiles like Volvo’s EX90, and cloud computing systems like Microsoft Azure. However, the supply chain for FPGA chips designed and used by US firms faces serious risks, particularly around cost, availability, and security, which have not been analyzed in depth from a policy perspective.
Contemporary analysis has largely focused on leading-edge logic chips, relying on assumptions about semiconductors that are not valid for FPGAs due to their unique flexibility and longevity.
This report analyzes the FPGA supply chain for US firms and the trade-offs these companies make among risks to cost, availability, and security; assesses how those trade-offs will change given a shifting global environment; and recommends policy interventions for the US government.
Overall, US firms tend to prioritize cost while significantly underinvesting in addressing substantial security and availability risks. Security risks are high given FPGAs’ technical complexity. Availability risks are largely driven by geographic and supplier concentration. Over the medium term, the People’s Republic of China’s (PRC’s) ongoing build-out of lagging-edge semiconductor manufacturing capacity will reduce FPGA costs, but this incremental boost in capacity will carry additional availability and security risks. In short, firms will continue prioritizing short-term costs and create negative externalities from availability and security risks.
US government intervention is required to build resilience against availability risks and develop technical measures that mitigate security risks, especially given increased PRC involvement in the FPGA supply chain. We recommend that the US government secure the US FPGA supply chain, protect critical national security capabilities and substantial economic industries, and continue to support American global technological leadership through four linked policy interventions:
- Use existing government infrastructure as a data-sharing and analytics hub for FPGA supply chains to improve situational awareness and future policy interventions.
- Invest in long-term efforts to improve the technical security of FPGAs.
- Build a stockpile of critical FPGAs for military and commercial applications to provide bridge capacity in the event of supply disruptions.
- Launch cross-sector planning efforts for potential supply disruptions to accelerate recovery.
These initiatives, coordinated by the Department of Commerce or Defense, should serve as a pilot for developing supply chain interventions for other critical technologies and industries.
2. Introduction
2.1 Problem statement
Semiconductors are critical to US national security and the economy. At the same time, the US semiconductor supply chain faces major economic and security vulnerabilities. These deficiencies have resulted in a flurry of (imperfect) legislation and policies in recent years, most notably the 2022 CHIPS and Science Act passed by Congress. However, specialized semiconductors like field-programmable gate arrays (FPGAs) have received much less policy attention despite their equality importance to US national interests.
Unfortunately, these recent US policies for semiconductors have ignored this market segment, assuming that the vulnerabilities and strengths in other semiconductor markets apply to specialized silicon. Export control discussions focus on leading-edge graphics processing units (GPUs) and the advanced manufacturing equipment needed to make them. Supply chain resiliency efforts often assume that all chips become obsolete as quickly as those leading-edge logic chips.
FPGAs are critical in many important applications. For example, the American military’s advanced F-35 fighter jet and its FGM-148 Javelin anti-tank missile depend on FPGAs and other specialized semiconductors, particularly for guidance and control systems. FPGAs are not only deployed in military equipment—they are also critical to most American automobiles and telecommunications networks. The electric EX90 SUVs Volvo assembles in North Carolina rely on FPGAs for their advanced driver assistance systems, while AT&T relies on FPGAs in Nokia equipment to operate their 5G network.
Unlike traditional leading-edge logic chips, FPGAs offer hardware-level flexibility, because the physical circuitry on an FPGA can be re-designed after they leave the factory. As a result, individual FPGAs often remain in production for over 20 years. FPGAs offer a unique mix of customization and performance, meaning they cannot easily be replaced.
Today’s policy debates lack the nuance to address specialized silicon and its unique characteristics. As a result, the FPGA supply chain has yet to be analyzed in depth, despite substantial differences from the overall semiconductor supply chain.
This report will address three key questions:
- What are the key risks in the FPGA supply chain for US firms and what trade-offs do firms make between those risks?
- Are effective mitigations and adaptations in place to address these risks?
- Which policy interventions should the US government take to address these risks?
The FPGA supply chain for US firms is the collection of such networks that involve US firms as suppliers, designers, manufacturers, or customers of FPGAs. A key risk is a supply chain risk with sufficient likelihood or impact on the American economy or national security to merit policy intervention from the US government.
2.2 Policy significance
FPGAs differ from other logic chips in two fundamental ways. First, their hardware can effectively be reconfigured after they leave the factory. This capability creates flexibility and allows customers to redeploy FPGA chips between different applications with minimal difficulty. A single FPGA chip could be repurposed for many contexts over its lifetime. Second, this flexibility significantly extends FPGA product lifecycles, which often last 20 years or more. In contrast, rapid product development cycles often quickly render other semiconductors obsolete.
Despite a relatively small market size of approximately $10 billion, FPGAs play critical roles in the development and deployment of modern AI models, military equipment, telecommunications infrastructure, and automotive sectors. Any disruption to the cost, availability, or security of US FPGAs would have substantial negative impacts across these sectors.
These factors mean that the FPGA supply chain is fundamentally different than the broader semiconductor supply chain and requires distinct policies, particularly given China’s growing capabilities in legacy-node semiconductors and FPGAs.
Today, US policymakers hold largely untested assumptions regarding FPGA supply chain risks, mitigations, and adaptations. In particular, policymakers assume:
- Semiconductor security vulnerabilities for non-military applications (i.e., commercial or consumer) are less critical than for military applications
- Onshoring leading-edge logic chip manufacturing ensures sufficient semiconductor supply chain availability (e.g., with the CHIPS and Science Act’s $52 billion investment)
- The US government can exert sufficient influence and/or control over foreign firms to ensure the semiconductor supply chain meets:
- US customers’ economic needs for availability and cost-effectiveness
- The US government’s national security interest in secure and reliable semiconductors
These assumptions may not hold for FPGAs, whose unique characteristics and expanding strategic importance expose gaps in current US policy. Addressing these risks requires tailored approaches that account for the distinct role FPGAs play in both commercial and national security applications.
2.3 Supply chain risk framework
Supply chain risks are those that threaten the cost, availability, or security of FPGA chips designed and sold by US firms, used by US firms in other products or services, or used by American end-users. US firms face three primary categories of risk when sourcing FPGAs:
- Cost risk includes both certain and potential costs that may be incurred both today and in the future. For example, selecting a higher-priced vendor to avoid vendor lock-in creates certain immediate costs. In contrast, accepting vendor lock-in by designing equipment or chips to align with a specific vendor’s products creates potential future costs if the vendor raises prices. Both of these risks are included as cost risks. Manufacturing quality is also a part of cost risk.
- Availability risk includes all risks that could limit the ability of US firms to acquire FPGAs. The two main availability risks are “can’t make” and “won’t sell” risks. “Can’t make” risks include scenarios where suppliers or manufacturers no longer have the capacity to produce FPGA chips or required inputs. For example, a major earthquake in Taiwan could damage foundries and prevent manufacturers from producing FPGAs. “Won’t sell” risks include scenarios where sufficient production capacity exists, but firms choose not to supply FPGAs to the US market. Those decisions could be caused by individual firms prioritizing higher-margin products or government regulation.
- Security risk includes all scenarios that reduce customers’ confidence that the FPGAs will do only what customers expect. Security risks include deliberate and unintentional failures to meet product specifications, particularly security specifications. For example, analysts recently identified undocumented communication devices in PRC-made power inverters, raising alarms over possible foreign access to US energy systems. Similar security risks could be introduced to FPGAs through hardware, gateware (see more below), or related software.
Managing supply chain risks requires making trade-offs, typically along an “efficient frontier” where the only way to reduce one risk is to increase another. These supply chain risks are deeply interrelated. For example, operating redundant distribution networks (e.g., warehouses, trucks) will reduce availability risk but increase cost risk.
In this model, government interventions to address FPGA supply chain risks can take two forms:
- Change the trade-offs: Incentivize firms to make different trade-off decisions along the frontier (e.g., reducing security risk and increasing cost risk)
- Change the game: Change the shape of the efficient frontier by implementing structural shifts (e.g., developing novel, low-cost solutions to security risks, imposing tariffs to increase cost of producing in some geographies)
3. Field-programmable gate arrays (FPGAs)
3.1 FPGA overview
Field-programmable gate arrays (FPGAs) are used in diverse applications because they offer more flexibility and longevity than other logic chips.
Figure 1: Chip archetypes mapped by performance and flexibility
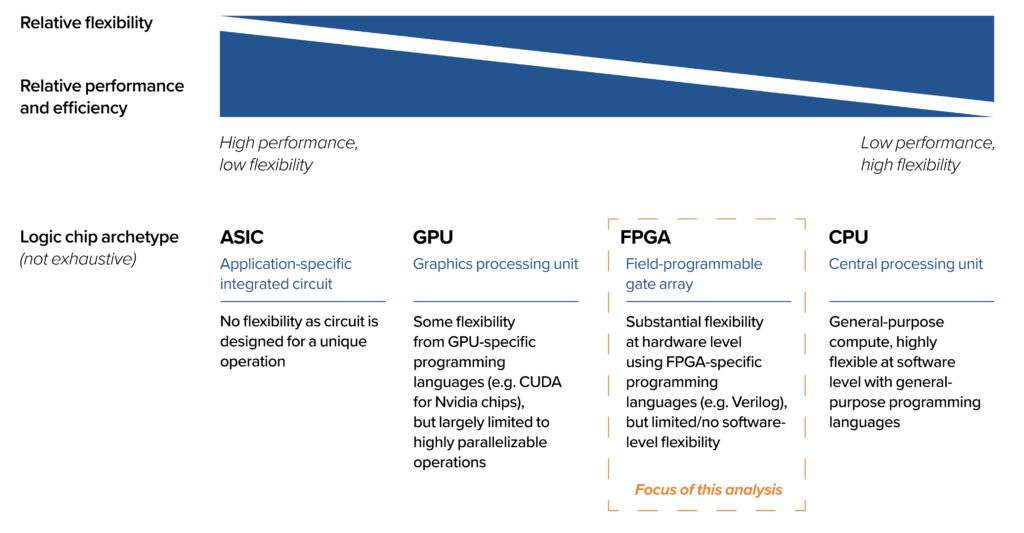
As shown in Figure 1, there are four types of logic chips, which form a spectrum trading off performance and efficiency for flexibility. Central processing units (CPUs), like those in consumer laptops, represent one extreme as highly flexible semiconductors that perform a wide variety of tasks, but with relatively low performance or efficiency. On the other extreme are application-specific integrated circuits (ASICs), which can perform only the specific operations for which they were designed, but with relatively high performance or efficiency.
FPGAs occupy a middle ground. They are somewhat flexible and can be reconfigured to execute different operations once manufactured, but with less performance or efficiency than ASICs. FPGAs are reconfigured by loading specialized code onto the chip that describes the active physical connections and logic elements in the chip. This code, called gateware, effectively transforms the FPGA into a new, custom-designed circuit, eliminating the need to manufacture new physical chips when responding to evolving requirements. As a result, FPGAs are typically used for workloads that require higher performance or efficiency than a general-purpose logic chip can provide, but that do not have the volume of demand to justify designing and manufacturing a custom ASIC chip. FPGAs are often used for research and development (R&D) as well as early versions of products. As production volume increases and unit economics shift, FPGAs can be replaced by ASICs or CPUs in future product generations to optimize cost, performance, or power efficiency.
FPGAs have a long working life and correspondingly long production lifecycles—often five to twenty-five years. This longevity is due in part to FPGAs’ flexibility, which allows for repurposing older FPGAs for novel tasks. As such, the FPGA market is substantially less cyclical than other segments of the semiconductor market. Most FPGAs on the market today are produced at legacy process nodes, typically between 16nm and 28nm. In comparison, leading edge semiconductor production takes place at the 3nm process node, as of mid-2025.
While alternative semiconductors exist, their adaptability and performance are insufficient compared to FPGAs. However, despite FPGAs’ critical applications across sectors, they are only a small component of the broader semiconductor market. FPGAs have an estimated market size of roughly $10 billion, which represents approximately 0.02 percent of the approximately $697.2 billion global semiconductor industry.
Figure 2: An overview of the semiconductor value chain, from initial design through end use
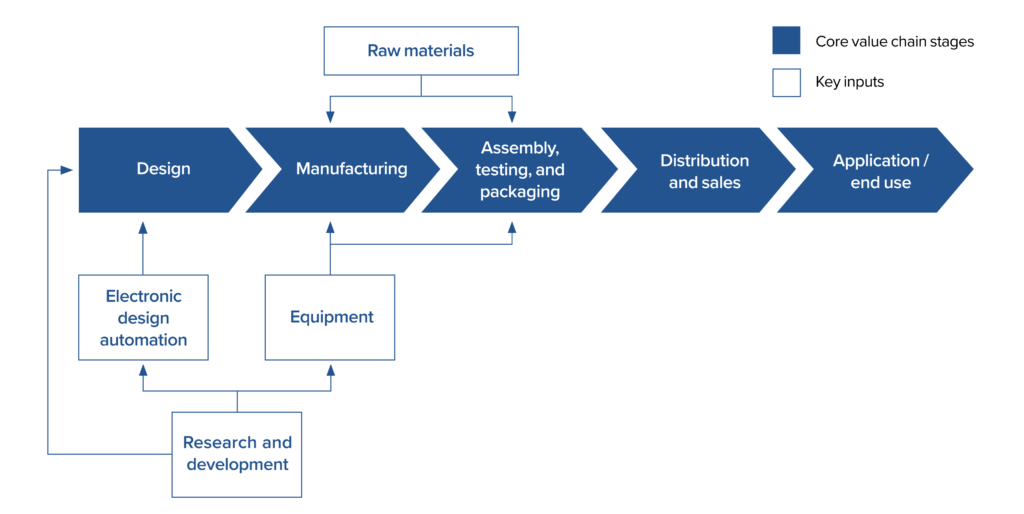
The semiconductor industry is highly globalized and concentrated, with clear leading countries and firms at most stages of the value chain. We use the value chain model described in Figure 2 to analyze the FPGA industry, focusing our analysis on four categories of participants:
3.2 FPGA applications
AI, cloud, and data centers
FPGAs are often used as accelerators to supplement general-purpose logic chips for compute-intensive workloads in data center contexts, including AI model training and inference. FPGAs can provide parallel processing capabilities for neural network inference, which can reduce latency and power consumption compared to traditional CPU or GPU solutions for some algorithms. For other cloud-based workloads, cloud service providers often integrate FPGAs into their data center architectures. For example, Microsoft has installed FPGAs in most Azure data centers. More broadly, FPGAs often underpin software-based networking approaches in data centers. Given the integration of FPGAs and other semiconductors—particularly GPUs—in the AI context, FPGAs should be considered as a critical component of overall AI and semiconductor strategy.
Many FPGA customers in AI, cloud, and data centers are less price-sensitive, limiting the impact of cost risks. However, availability risks could create economic harm, particularly as AI models are deployed throughout the American economy. Security risks could also threaten economic harm and disrupt US technological leadership in AI development.
Military equipment and defense systems
FPGAs are extensively used in radar systems, electronic warfare equipment, and secure communications platforms, providing advanced signal processing and encryption capabilities. The versatility and reprogrammable capabilities of FPGAs mitigate hardware obsolescence in defense systems by reducing the frequency and associated costs of hardware replacements, making military customers relatively price-insensitive. However, both availability and security risks in FPGAs could create major gaps in American security capabilities, particularly those involving missile guidance systems.
Telecommunications
FPGAs are often critical components in telecommunications infrastructure, where they excel in two principal areas. First, FPGAs deliver strong performance in signal processing tasks, allowing 5G networks to handle large volumes of data with minimal delays. For example, 5G networks rely on FPGAs for multiple input/multiple output (MIMO) systems, which improve connection quality and speed by dynamically adjusting wireless signals. Second, the reprogrammable nature of FPGAs allows telecommunications providers to reprogram the chips to adhere to evolving network standards, protocols, or applications. Telecommunications infrastructure typically involves low margins and carries critical information, heightening the impact of cost and security risks respectively. However, as telecommunications infrastructure is generally not replaced on an ongoing basis, the impact of availability risks is likely more limited.
Automobiles
FPGAs are fundamental to modern automobiles. In advanced driver assistance systems, FPGAs process data from multiple sensors (e.g., cameras, radar) to enable safety features like lane keeping and collision avoidance, while also integrating various sensor inputs for autonomous driving decisions. FPGAs also power in-vehicle entertainment systems by managing video interfaces and multimedia features, performing tasks like video decoding, image rendering, and audio processing. In electric vehicles, FPGAs often implement specialized control algorithms and execute complex computations to enhance power management by optimizing battery efficiency, controlling power distribution, and enabling sophisticated charging systems. FPGA reconfigurability also allows automobile manufacturers to update and upgrade systems to increase efficiency, security, and safety throughout the vehicle lifecycle. The automotive industry would face substantial economic impacts from cost and availability risks, as seen during the COVID-related automobile chipset shortage. There are also emerging security concerns related to automobile software and hardware, including risks from FPGAs.
4. FPGA risk analysis
As described in Section 2.3, we focus our analysis on FPGA cost, availability, and security risks. We consider each type of risk across the FPGA value chain outlined in Section 3.2, then examine the trade-off decisions firms make between risks. Figure 3 shows which supply chain risks are most relevant for each stage of the FPGA value chain.
Figure 3: Relevant supply chain risks at each stage of the FPGA value chain
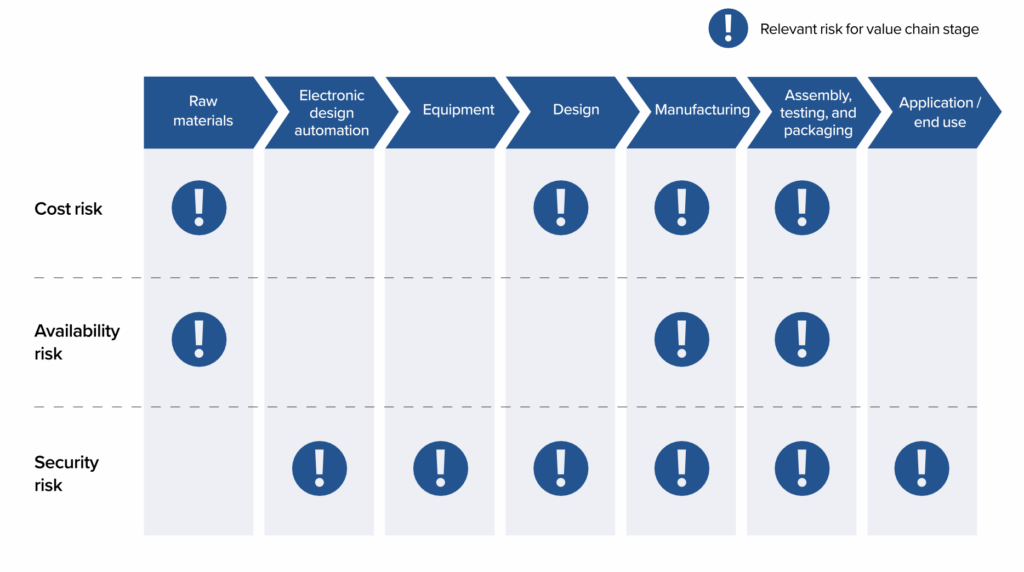
4.1 Cost
The FPGA supply chain faces four key drivers of cost risk:
- Potential US government tariffs on semiconductor imports
- Short- and medium-term shortages in some key input materials
- Medium- and long-term impacts of climate change
- Medium-term increases in lagging-edge production capacity place downwards pressure on costs
First, recent proposals to impose tariffs on imported semiconductors have encountered widespread pushback from a broad spectrum of industries. As the United States holds only an approximate 12 percent share of the overall semiconductor manufacturing market and less in assembly, testing, and packaging (ATP), any tariffs would have broad impacts across the industry. Most manufacturing and assembly, testing, and packaging in the US FPGA supply chain also take place outside the country, meaning semiconductor import tariffs would substantially increase FPGA costs across the manufacturing and ATP stages of the value chain.
Second, increasing competition between the United States and the PRC raises the likelihood of further PRC restrictions on critical minerals, particularly given China’s history of using its critical mineral supply as a geopolitical tool. China dominates the market for several critical minerals that are essential inputs for FPGA manufacturing, particularly refined gallium, where it controls about 99 percent of the market. Leveraging this dominance, China banned all exports of gallium to the United and imposed more stringent licensing requirements for other critical minerals in April 2025. PRC restrictions have led to significant price increases, with the price of gallium alone rising 80 percent since December 2024. While other countries could step in to provide additional gallium for the semiconductor industry, prices may remain elevated or increase further before production can scale.
Third, over the medium- and long-term, climate change creates mitigation and adaptation costs for suppliers, chip designers, and manufacturers. Semiconductor firms are likely to continue at least some investment in mitigation efforts and manufacturers will continue to face operational disruptions from the impacts of climate change, which will increase their cost structure to account for mitigation response and adaptation.
Fourth, our research indicates that the PRC is launching a major build-up of capacity at older, lagging-edge process nodes of semiconductor manufacturing, including substantial state investments in FPGA chipmakers. Big Fund investments in PRC FPGA firms like Anlogic provide early indicators that FPGAs are a focus area for the PRC. According to Jeremy Mark, Senior Fellow with the GeoEconomics Center of the , there is “no evidence that there is a slacking of [Chinese] investments and commitment of resources toward semiconductors and SMEs [as] its technology growth strategy, particularly in AI, requires semiconductors.”
The PRC is also developing FPGA-specific design capabilities. PRC FPGA firms including Anlogic, Gowin Semiconductor, and Pango Microsystems have received substantial government support as they develop competitive portfolios, beginning at the low end of the segment. These firms provide the PRC’s semiconductor and AI ecosystems with critical FPGA capabilities—for example, Pango is now the largest FPGA supplier to Huawei.
This growing FPGA manufacturing capacity will allow firms to produce FPGAs at lower costs than the current market, but this incremental capacity will likely come with higher availability and security risks than most of today’s capacity. This will increase the effective cost of reducing availability and security risks in the FPGA supply chain.
Given the scale of PRC investments in lagging-edge manufacturing capacity overall and in FPGAs in particular, the resulting downward cost pressure will outweigh input-based and climate impacts on costs, driving FPGA costs down overall in the medium term. However, considering the uncertainty of US semiconductor tariffs and the timing of PRC capacity coming online, FPGA costs may increase temporarily in the short term as costs increase for the raw materials, manufacturing, and ATP stages.
Overall, the impact of increased cost risks for the US FPGA supply is moderate. Major defense firms and the US military are largely price-inelastic customers and would likely absorb any cost increases. For commercial applications, our analysis suggests a substantial ability to absorb FPGA price increases. Using electric vehicles as an example of commercial use of FPGAs, we conducted a tear-down analysis of Tesla’s financial statements. Our findings suggest that Tesla could absorb approximately a 5x price increase in FPGA components while breaking even on a gross margin basis.
4.2 Availability
The FPGA supply chain faces two principal availability risks, “can’t make” and “won’t sell,” which affect the sourcing of raw materials, manufacturing, and ATP. “Can’t make” risks include scenarios where suppliers or manufacturers no longer have the capacity needed to produce FPGA chips or required inputs. “Won’t sell” risks include scenarios where the capacity exists, but firms choose not to supply FPGAs to the US market, either due to governments regulating firms’ activities or individual firms prioritizing higher-profit opportunities elsewhere in the semiconductor market.
“Can’t make” risks
Industry concentration—including suppliers, manufacturers, and geographies more broadly—fosters several “can’t make” risks. For example, ASML, the only supplier of the “extreme ultraviolet lithography” equipment needed to manufacture leading-edge chips and a leader in less-advanced lithography systems, relies largely on firmware that may be susceptible to bugs and security vulnerabilities, which could cause major downtime for manufacturing.
Geographic concentration means an individual natural disaster (e.g., seismic activity in Taiwan) or direct US-PRC conflict could eliminate substantial FPGA manufacturing capacity. The accelerating competition between the United States and the PRC creates the potential for kinetic conflict, likely in East Asia and possibly on or near Taiwan. Any such conflict could substantially damage semiconductor industry facilities and limit manufacturing capacity. The likelihood of such a conflict is the subject of ongoing debate. The Economist Intelligence Unit assesses a low probability of such a conflict occurring in the short term, while Harvard Kennedy School professor Graham Allison believes that conflict is possible, but far from certain. In contrast, some US military leaders have assessed direct US-PRC conflict to be likely. Overall, the probability of such conflict is low but not negligible.
“Won’t sell” risks
US-PRC competition also drives major “won’t sell” risks. The United States has steadily increased export controls and commercial restrictions targeting the PRC. While the PRC response to date has largely focused on critical mineral exports, growing PRC influence over semiconductor firms across Asia raises the possibility that the government could restrict semiconductor exports to the United States and its allies. The FPGA industry is likely to face outsized risk from such restrictions or similar efforts. FPGA’s small market size would limit the economic impact to the PRC and other East Asian actors, while its strategic importance to the United States increases its value as a target.
“Won’t sell” risks also include the possibility of firms independently re-prioritizing their production capacity towards larger and potentially higher-profit segments of the semiconductor industry. However, interviewed experts report that large segments of the FPGA market are relatively price-inelastic and could absorb price increases. As such, these economically induced “won’t sell” risks are assigned a low probability.
Overall, “can’t make” risks have a low probability, and “won’t sell” risks have a moderate probability of occurrence for the FPGA market. However, given their critical applications, any disruptions to FPGA availability could threaten US military readiness and economic prosperity.
4.3 Security
There are three categories of security vulnerabilities—hardware, gateware, and related software—in the FPGA value chain. Drawing on a framework and definitions developed by the Lawfare Institute’s Trusted Hardware and Software Working Group, mitigating security risks is the process of building trust to ensure FPGAs do not contain security vulnerabilities. The analysis considers mitigations in line with the three methods to build trust included in the Working Group’s framework: trust in technical performance, trust in corporate governance, and trust in nation-state policy and law.
First, hardware supply chain attacks on FPGAs involve physical tampering with the FPGA chip during manufacturing, assembly, testing, and packaging. This tampering could establish a foundation that enables nefarious actors to launch gateware and software attacks on FPGA end-users. Returning to the ASML example, their critical lithography machines could also pose a hardware supply chain risk, particularly if they use monolithic and poorly documented software systems.
The PRC may have successfully executed a hardware supply chain attack at Supermicro, a US-based server manufacturer, exposing US military network data to the PRC. While this potential attack was focused on the assembly stage (not manufacturing) and experts disagree about the plausibility and success of this attack, the fact that the incident cannot be deemed impossible, even in hindsight, demonstrates the feasibility of hardware supply chains as an attack vector across several stages of the value chain. Today, there appear to be few barriers against hardware supply chain attacks on FPGAs, especially at the assembly, test, and packing (ATP) stage of the value chain.
Second, FPGA gateware (the reconfigurable code that defines the active physical connections and logic elements in the FPGA chip) could be compromised at the manufacturing, assembly, testing, and packaging, or application/end-use stages of the value chain. This risk includes insider attacks and improper security configurations, although it can be mitigated by vendor-provided proprietary security features like secure boot, which verifies gateware authenticity during startup. Industry experts report that it is “easier to attack a chip by injecting code into the [gate]ware than by getting into TSMC.” Successful gateware attacks could compromise sensitive data or remotely introduce malicious configurations.
Third, software supply chain attacks on FPGAs could emerge through the cloud stack used by chip designers at the design stage of the value chain. Semiconductor designers usually do not have full control over the configuration their cloud-based design software, which is typically developed by an electronic design automation (EDA) firm such as Cadence or Synopsys. Unsecured cloud layers may risk compromising FPGA chip designs and relevant intellectual property that provides the United States with technological advantage over other nations. For example, in 2024, Microchip Technology, a US semiconductor company that specializes in FPGAs for defense, aerospace, and automotive applications, confirmed unauthorized access of the company’s server, which led to manufacturing facilities operating at a reduced capacity and hindered the firm’s ability to fulfill orders.
The Spectre and Meltdown hardware vulnerabilities in Intel CPUs demonstrate the potential damage of supply chain attacks on FPGAs. While Spectre and Meltdown appear to have been caused by innocuous design errors, they represented massive security vulnerabilities in almost every processor in use at the time, including leaking data to potential attackers. If a malicious actor were to insert similar vulnerabilities into FPGAs via the software used to design the chips, the full set of security and economic activities described in Section 3 would be at risk.
Turning to trust-building measures to mitigate these risks, we consider trust in technical performance, corporate governance, and nation-state policy and law. While these dimensions of trust are mutually interdependent, they provide a convenient categorization to assess trust-building.
Technical solutions to address the security concerns raised above (across hardware, gateware, and software attack vectors) are generally feasible and the US National Institute of Standards and Technology (NIST) has drafted best-practice security guidance, although these technical methods do incur incremental cost risk.
Trust in a supplier’s corporate governance generally requires extensive engagement and organizational audits—while also feasible, these would likely incur significant costs while providing less benefit than technical solutions.
Finally, appropriate levels of trust in nation-state policy and legal environments vary widely between countries involved in the FPGA supply chain. Figure 4 displays selected dimensions of the World Bank’s Worldwide Governance Indicators for China, Taiwan, and the United States. Across political stability and absence of violence/terrorism, regulatory quality, rule of law, and voice and accountability, the US and Taiwan receive generally high scores whereas China receives generally lower scores. As such, we conclude that, in general, trust-building efforts focused on nation-state policy and law are less feasible for FPGA supply chain participants operating in China, but reasonably feasible elsewhere.
Figure 4: Figure 4: World Bank governance indicators for China, Taiwan, and the United States (2025)
Most FPGA firms do not invest sufficiently in trust-building measures in any of the above dimensions. This decision likely reflects the general market-based tendency to prioritize reactive security over preventative security measures, necessitating government intervention.
5. Overall assessment
The US FPGA supply chain faces substantial, unmitigated risks to availability and security, which will be exacerbated by a PRC build-up of FPGA manufacturing capacity, increasing the effective cost of ensuring availability and security.
Today, FPGA market participants overwhelmingly focus on reducing cost risk, often at the expense of increasing availability or security risks. However, availability and security risks create broad externalities (see Sections 4.2 and 4.3), including substantial economic, national security, and geopolitical consequences. Individual FPGA firms cannot fully internalize the costs of these risks given information asymmetries and spillover effects. As a result, firms underinvest in ensuring security and availability, leading to a market failure that requires US government intervention. Appropriate interventions could include reducing the cost of production with low availability and security risks (e.g., through subsidies) or increasing the effective cost of production with high availability and security risks (e.g., through tariffs imposed on the sources of production). Both forms of intervention would incentivize firms to shift production towards a supply chain construct with lower availability and security risks, onshoring operations in the United States or in other, more trusted nations. Overall, the US government can exert sufficient influence over foreign firms to effectively manage security risks within today’s FPGA supply chain structure but cannot rely on foreign components of the FPGA supply chain to manage availability risks.
The policymakers’ assumptions described in Section 2.2 are mostly invalid, as described in the table below.
6. Policy recommendations
Despite mounting security and availability vulnerabilities within the supply chain, FPGA firms continue to prioritize cost risk excessively. Availability and security risks will likely intensify as China expands its manufacturing capacity for lagging-edge semiconductors, particularly in the lower- and mid-tier FPGA segments. FPGAs remain relatively unaddressed by current US semiconductor policies, which implicitly assume that security risk is not significant for non-military applications, that sufficient availability is provided by onshore manufacturing of leading-edge logic, and that the existing supply chain construct can meet US economic and national security needs. Unfortunately, these assumptions are largely invalid, and policy interventions are needed to address the externalities of FPGA availability and security risks.
We recommend the US government focus on managing FPGA security risks within the existing supply chain structure, which includes a substantial foreign firm presence, and focus on domestic-oriented solutions to address FPGA availability risks.
Addressing the significant, unmitigated risks facing the US FPGA supply chain will require the US government to implement four interrelated policy interventions. The first two address the security risks outside of military applications. The final two address availability vulnerabilities in the current FPGA supply chain as, contrary to typical policy assumptions, the United States’ leading-edge onshoring efforts are inadequate to address domestic demand for FPGAs. These recommendations are summarized in Figure 5.
Figure 5: Four policy interventions to address FPGA supply chain risks
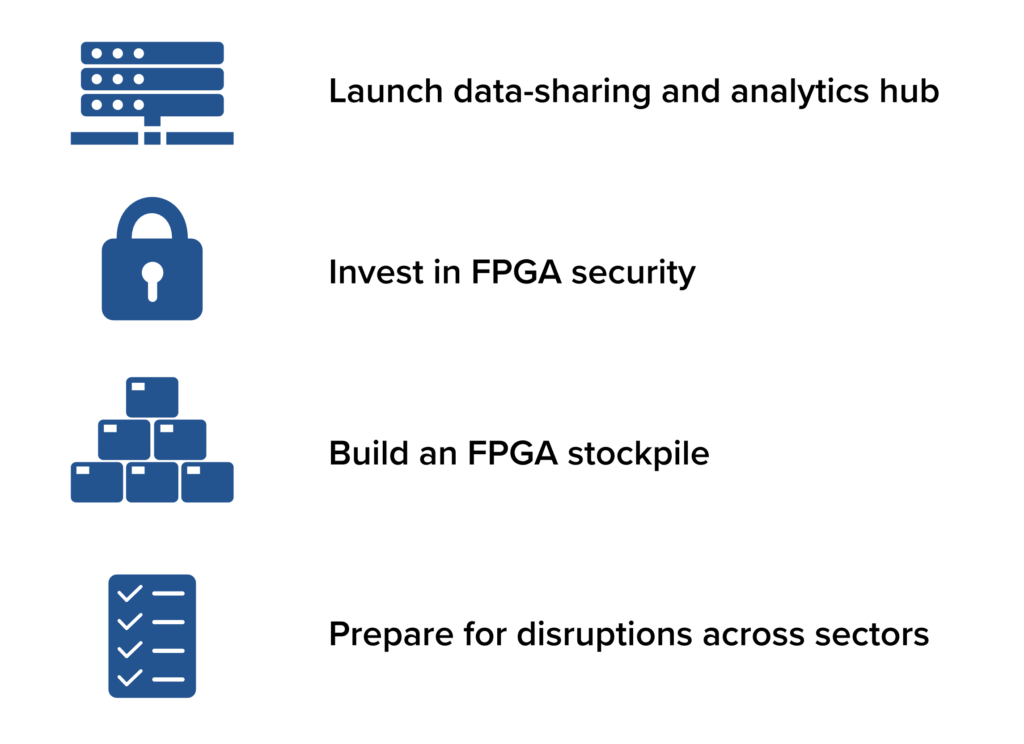
1. Launch a data-sharing and analytics hub
Designate the Department of Commerce’s Supply Chain Center (SCC), administered by the International Trade Administration, as the national data-sharing and analytics hub for FPGA supply and sourcing. Direct the SCC to conduct their second planned 2025 tabletop exercise on FPGA chips.
Strongly incentivize and, where appropriate, require public- and private-sector designers, manufacturers, distributors, and customers of FPGAs to provide the SCC with specific, SKU-level information on their FPGA supply chains, including quantities, prices, and suppliers. This information should include a detailed analysis of the origin countries of FPGAs and the origins of key inputs such as minerals or manufacturing equipment. These data-sharing agreements should become a requirement for CHIPS and Science Act funding agreements, government procurement of FPGAs (both military and commercial), and other federal government support for relevant firms.
The resulting SCC data will provide policymakers and the US FPGA supply chain participants a deeper understanding of the risk environment, enabling more effective design and delivery of policy interventions.
2. Invest in FPGA security
Direct federal research funders to prioritize academic and industrial R&D of enhanced FPGA security techniques, such as improving verification and validation. These funders include the Defense Advanced Research Projects Agency, the National Science Foundation, the Department of Energy, and the National Semiconductor Technology Center in the Department of Commerce.
Direct NIST to review existing FPGA product security standards and modernize them as needed, building upon its recent security report and guidance on cybersecurity for the wider semiconductor manufacturing industry.Direct NIST to develop security audit standards for FPGAs, supporting semiconductor firms’ efforts to proactively investigate their supply chains to identify vulnerabilities and building on existing efforts to design assurance best practices for government use of FPGAs.
Enhance existing engagement with semiconductor industry researchers, policymakers, manufacturers, and customers, including through existing consortia such as the SEMI Semiconductor Manufacturing Cybersecurity Consortium, to kickstart industry-wide efforts to develop FPGA-specific technical security solutions.
3. Build an FPGA stockpile
Using preliminary data and insights from the SCC’s FPGA data-sharing and analytics hub, build a national stockpile of critical FPGA chips for both military and commercial applications. This stockpile would effectively address availability risks by allowing critical firms to source the FPGAs they need from the stockpile if their usual suppliers become unavailable.
Identify key SKUs with long expected lifecycles (5+ years) used for critical applications, in collaboration with public-sector (e.g., DoD, DoE, NSA) and private-sector end-customers of FPGAs, such as cloud service providers, defense prime contractors, telecommunications equipment manufacturers and adjacent firms, and automakers.
Develop and launch procurement, storage, and security strategies for these FPGAs as soon as possible, with an initial focus on specific SKUs with high availability and liquid markets to reduce market disruptions and distortions. Explore innovative procurement and contracting arrangements such as the fixed-price contracts recently deployed by the US government’s Strategic Petroleum Reserve.
4. Prepare for disruptions across sectors
Develop a government-wide playbook to address potential large-scale disruptions to the FPGA supply chain. The government response could include targeted subsidies to critical US firms, technical assistance in re-designing essential products to avoid unavailable FPGAs (e.g., replacing them with stockpiled SKUs or other types of chips), and measured, proportionate policies to respond if disruptions were caused by foreign competitors (e.g., increasing export controls).
Internally, use SCC FPGA data to develop plans for the prioritization of FPGA supplies in the event of supply chain disruptions, including a thorough assessment of legal and regulatory authorities to direct FPGA inventories to specific public- and private-sector actors.
Externally, encourage US FPGA firms and their end-customers to develop data-informed contingency plans for supply chain disruptions through tabletop exercises and computer-based simulations to identify vulnerabilities and develop mitigations. Similarly to the data-sharing agreements described above, the US government should consider a broad range of methods to encourage firms to participate, including CHIPS and Science Act funding and government procurement.
These policy interventions should be coordinated by a small project management team likely within the Departments of Commerce or Defense. This team should focus on managing the implementation of these recommendations with an agile approach using existing government resources. In particular, the team should develop an integrated approach to performance measurement and management, including identifying specific objectives, metrics, and targets for each policy intervention. This performance measurement would enable a “test and learn” approach to iteratively improve the design and implementation of these interventions.
Given the critical role played by private firms in the US FPGA supply chain, the government should encourage engagement and cooperation from the private sector, particularly with security-related interventions. These measures should include procurement priority for federal government contracts and voluntary certifications.
Policies to reconsider
We also note three potential policies that we recommend the US government does not pursue:
1. Subsidized onshore manufacturing, assembly, testing, and packaging of FPGAs
Several barriers prevent the onshore manufacturing of FPGAs.
First, the scale of the lagging-edge market creates economic difficulties, as massive investments would be required to stand up the multiple fabs needed to enter the FPGA market at scale. According to an industry expert, “in order to have ATP near-shore, the United States would need more money and longer-term commitments than the CHIPS Act.”
Second, operational feasibility is limited by the age of lagging-edge WFE, which in many cases is no longer in active production, and also by the PRC build-up of lagging-edge supply, which has limited WFE availability (see Section 4.1).
Finally, following the implementation of the CHIPS and Science Act, semiconductors are often viewed politically as a “solved problem,” limiting justification for massive investments in lagging-edge capacity. Additionally, some experts, like the GeoEconomics Center’s Jeremy Mark, view onshoring as “a bit of a fool’s game to recreate what already exists in so many countries.”
Instead, the US government should emphasize ongoing supply chain coordination with partner and allied nations. In many cases, these nations (e.g., Japan) can offer an appropriate balance of cost, availability, and security risks for many FPGA applications. In particular, their policy and legal environments can facilitate more trust in supply chain security than is generally feasible in China.
These policy interventions should be coordinated by a small project management team likely within the Departments of Commerce or Defense. This team should focus on managing the implementation of these recommendations with an agile approach using existing government resources. In particular, the team should develop an integrated approach to performance measurement and management, including identifying specific objectives, metrics, and targets for each policy intervention. This performance measurement would enable a “test and learn” approach to iteratively improve the design and implementation of these interventions.
Given the critical role played by private firms in the US FPGA supply chain, the government should encourage engagement and cooperation from the private sector, particularly with security-related interventions. These measures should include procurement priority for federal government contracts and voluntary certifications.
2. Export controls on lagging-edge semiconductor manufacturing equipment
Most FPGA production takes place at lagging-edge nodes which have already achieved at-scale production across many countries, limiting the impact of export controls in reducing access to lagging-edge chips. For example, ASML estimates that around 90 percent of all WFE it has ever sold is still in use, representing significant manufacturing capacity at these legacy nodes.In particular, given China’s extensive manufacturing capacity for lagging-edge logic chips, knowledge of these processes and relevant equipment is already widespread in the PRC, largely sourced from outside the United States (e.g., ASML in the Netherlands). As such, export controls would likely be difficult to enforce and would produce limited impact.
Export controls on lagging-edge manufacturing equipment would also impose three major costs on the United States: implementation costs, costs from potential retaliation, and geopolitical costs.
Export controls would be implemented and administered by the Department of Commerce’s Bureau of Industry and Security (BIS), which is already heavily resource-constrained. Additional export controls on these highly technical products would require either incremental budget reallocations to BIS or redirecting existing capacity away from existing BIS priorities.
China is also likely to retaliate in kind to additional American export controls, particularly given the context of the current trade war. Applying standard international relations frameworks, China is likely to misperceive these US export controls as being a deliberate and centrally-directed effort to hobble its economy. This misperception would likely be exacerbated by the general tendency of nations to overestimate the degree to which they are being intentionally targeted by an adversary while overestimating their adversary’s belief that they themselves are not a threat.
Finally, from a geopolitical perspective, US allies, such as the Netherlands and Japan, have recently voiced hesitancy to continue mirroring US export control policies out of economic concerns and fear of PRC retaliation. Should the United States pursue further implementation of semiconductor export controls via its allied nations, Mark also cautions that such “excessive control over exports would raise tensions significantly with other countries.”
3. Separating US FPGA supply chains from the PRC
We recommend that the US government does not in general prevent US FPGA firms from using PRC firms as part of their supply chain, either through direct regulation or through imposing substantial tariffs on PRC-produced FPGAs. Such a policy would be analogous to the Jones Act, which prevents domestic shipping from using vehicles built, owned, crewed, or flagged outside the United States. While it has protected the resiliency of the American merchant marine, the Jones Act has imposed significant economic costs on the United States.
In the case of FPGAs, we assess that PRC presence in the US FPGA supply chain poses risks to the security and availability of FPGAs. However, it also has undeniable cost benefits. While the global FPGA market remains small compared to the overall semiconductor market, FPGAs represent a major input cost for a broad set of products and FPGA unit economics affect product costs across the economy. We conclude that the resulting security risks can largely be mitigated with technical solutions and the availability risks with a US FPGA stockpile, as described in our policy recommendations.
Additionally, fully decoupling US FPGA supply chains from the PRC would substantially increase the cost structures of US FPGA firms, with negative impacts for on American economy and on wider US global technological influence. As many geopolitical analysts expected, the technology ecosystem is beginning to fracture into US- and PRC-led components, with the PRC government actively encouraging domestic chip firms to use technical architectures not controlled by the United States. Reducing the economic competitiveness of US FPGA firms would inhibit them from competing with PRC competitors globally, risking US leadership in the FPGA industry over the long run. However, FPGAs used for highly sensitive and critical applications (e.g., military equipment and defense systems) should continue to prioritize security and availability risks. As a result, US and allied nations should lead the design, manufacturing, assembly, testing, and packaging of these chips.
If the US government does impose tariffs on semiconductor imports, we recommend that they should be narrowly targeted towards the PRC and any other nation that appears to be deliberately building large amounts of lagging-edge semiconductor manufacturing capacity and that poses substantial availability and security risks.
7. Conclusion
Overall, the US government faces a clear opportunity to secure the FPGA supply chain for US firms by leveraging existing government infrastructure to track and analyze supply chain data, launching an FPGA stockpile for critical chips, developing cross-sector plans for supply disruptions, and investing in technical solutions for FPGA security. More broadly, this integrated set of FPGA supply chain policy interventions should be treated as a lighthouse or pilot. This approach involves testing the interventions to harden the US supply chain for critical technologies with a small but important market, such as FPGAs, then adjusting policy design and implementation while rolling out the approach to other high-priority areas (like other types of specialized silicon), before scaling across industrial supply chains more broadly. These policy interventions will strengthen the American economy and ensure US national security.
About the Authors
Andrew Kidd holds a master of public policy from the Harvard Kennedy School and was previously an engagement manager in the high-tech and public sector practices at McKinsey & Company.
Celine Lee holds a master of public policy from the Harvard Kennedy School and previously held fellowships at the United States Senate Committee on Foreign Relations and the American Institute in Taiwan (AIT).
Bruce Schneier is a security technologist and a fellow and lecturer at the Harvard Kennedy School.
Related Content
Explore the program

The ’s Cyber Statecraft Initiative, part of the Technology Programs, works at the nexus of geopolitics and cybersecurity to craft strategies to help shape the conduct of statecraft and to better inform and secure users of technology.








