We live watching our cell phones and what appears on their screen, from a notice from the bank to a code to authorize a payment. This dependency has turned the text message into fertile ground for deception, with campaigns of smishing that imitate well-known companies and sneak into conversations that seem legitimate. The problem is not only technical, it is trust: distinguishing at a glance who is really on the other side.
For years, SMS has treated legitimate and fraudulent messages equally, and that neutrality is exactly what attackers exploit. Malicious campaigns detected in Spain show how names and formats of known entities are copied to gain the trust of the recipient. These messages are designed not to raise suspicion. And often, when doubt arises, it is too late to react.
Say ‘hello’ to verified messages. Faced with the erosion of trust in traditional SMS, the industry has chosen to reinforce the identity of the sender instead of placing all responsibility on the user. Verified messages introduce a relevant change: they make visible whether a company has been recognized as legitimate before the message reaches the mobile. Supported by the RCS protocol, these messages add a name, logo and verification indicators with the intention of reducing one of the main weapons of fraud, confusion about the real origin of the message.
BBVA. This is how it looks on mobile. In Spain, BBVA has been one of the first large banks to show this change visibly for the user. On Android, the bank’s official messages are identified with its name and logo, accompanied by an indicator that indicates them as an official channel. By clicking on that logo, the user can verify that the associated data, such as the telephone number or website, match those of the bank. Furthermore, these communications arrive in a different thread than traditional SMS, precisely to prevent them from being mixed with fraudulent messages.

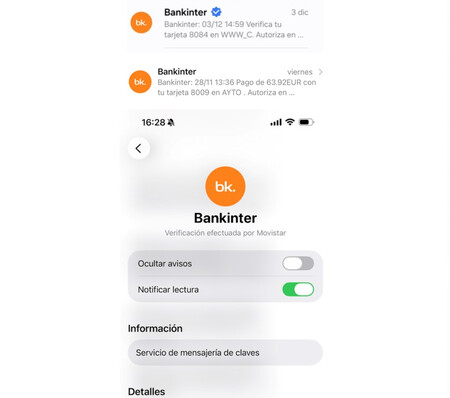
Bankinter has also taken the leap. Bankinter has partnered with Telefónica to distribute verified messages. The entity explains that this will improve the security of “critical communications”, such as single-use codes for transfers or online payments. Here we will also find the sender verification confirmation, the official logo and additional information such as the website and a telephone number.

How verification works. Behind that visible badge there is a process much less obvious to the user. The standard defined by the GSMA establishes several previous stages before a company can send a single verified message. First, the entity must register its identity, with a specific name and logo, and submit it to external certification by a third party that validates that the entity can use that name and logo. This validation is not enough on its own: the authority that issues it must be included in the trusted list of the recipient’s operator. Without that complete string, the check simply doesn’t show.
Who verifies who. Here the so-called Verification Authorities come into play as third parties in charge of validating that a company is who it says it is before it can send verified messages. That role may fall to private companies specialized in digital verification, mobile operators or even government entities, depending on the deployment and the country. Afterwards, it is the user’s operator who decides whether they trust that authority, something that is sometimes reflected visibly in the message itself, as occurs in an official Bankinter example, where the system indicates that the verification has been carried out by Movistar.
The final verification occurs when the message reaches the phone. According to the GSMA standard, the messaging app automatically downloads the sender’s profile and runs a series of technical checks before displaying any badge. It is checked that the signature is still valid, that the authority that issued it is accepted by the user’s operator and that the data has not been altered. Only if everything fits does the verification indicator appear; If something fails, the message loses that appearance of legitimacy.
Does it work on iOS and Android? This scheme is not exclusive to Android. Apple added support for RCS as a carrier service starting with iOS 18, allowing you to send and receive messages with advanced features when not using iMessage. In practice, the behavior is the same: if the operator supports RCS and the standard is implemented, the system can display the name, logo and indicators associated with the sender. Without this support from the operator, the message returns to the familiar terrain of SMS or MMS, without additional verification signals.
For the user, the practical learning is simple: a verified message offers more context and more clues than a conventional SMS, but it does not eliminate the need to remain cautious. Knowing that there is a technical process behind that distinction helps us better interpret what reaches our mobile phones and be wary when something does not match. However, in an environment where malicious actors never sleep, caution remains essential.
Images | Vitaly Gariev | BBVA | Bankinter | Gemini 3 Pro
In WorldOfSoftware | Cybersecurity experts by day, cybercriminals by night: how two professionals fell after using ransomware







-Julian-Chokkattu-Gear.jpg)




